WordPress Pingback Function Abused in Cyber Attacks | DDoS Prevention | Prolexic by Prolexic - Issuu

Bolstering API Security and Bot Attack Protection with NSFOCUS Next-Generation WAF - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Imperva on X: "In a server-side request forgery (#SSRF) attack, bad actors abuse server functionality to access or modify resources. Learn about the risks, common attack types, and ways to mitigate this

Global Criteria: The 12 Core Functions of the Substance Abuse Counselor – 8th Edition Paperback – January 1, 2021 | CCAPP Continuing Education

Global Criteria: The 12 Core Functions of the Substance Abuse Counselor : Herdman, John W.: Amazon.de: Bücher

UN Office on Drugs & Crime on X: "We can only take action against something we fully understand. Preventing corruption becomes possible when we know root causes, scale and impact. Watch to

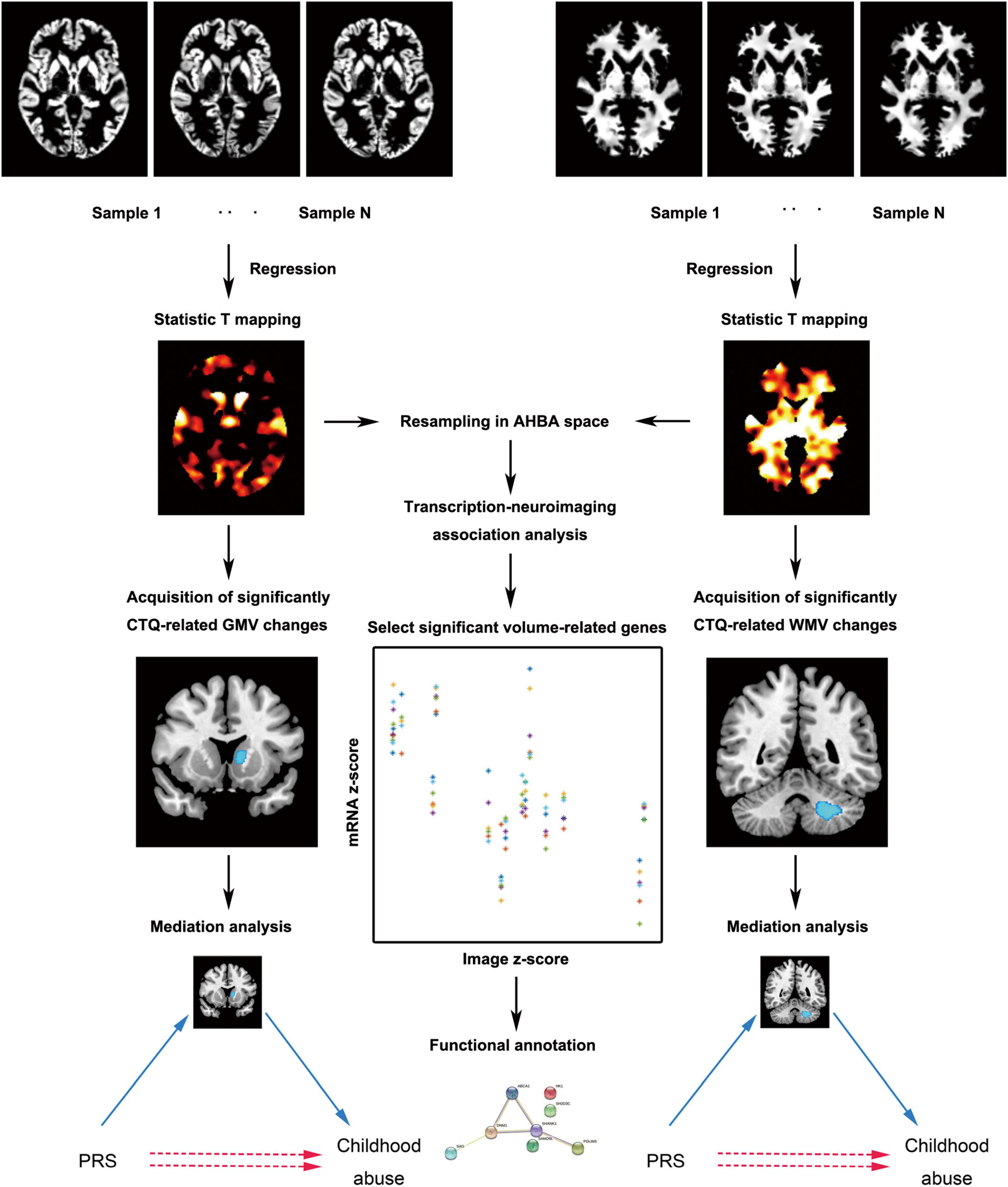
Functional neuroanatomy of childhood abuse. The functional anatomy of... | Download Scientific Diagram

PoPETs Proceedings — No Privacy Among Spies: Assessing the Functionality and Insecurity of Consumer Android Spyware Apps