Abusing the Internet of Things: Blackouts, Freakouts, and Stakeouts (English Edition) eBook : Dhanjani, Nitesh: Amazon.de: Kindle-Shop

Abusing the Internet of Things: Blackouts, Freakouts, and Stakeouts (English Edition) eBook : Dhanjani, Nitesh: Amazon.de: Kindle-Shop

Abusing the Internet of Things. Blackouts, Freakouts, and Stakeouts Nitesh Dhanjani. Ebook - Księgarnia informatyczna Helion

Abusing the Internet of Things: Blackouts, Freakouts, and Stakeouts (English Edition) eBook : Dhanjani, Nitesh: Amazon.de: Kindle-Shop
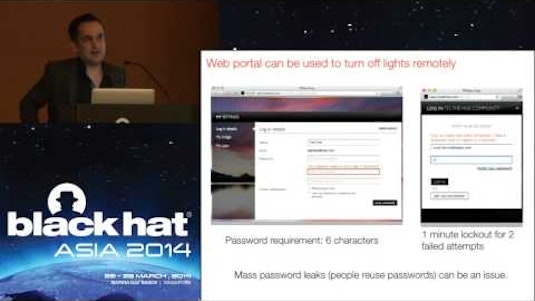
Black Hat Talk: Abusing the Internet of Things - Blackouts, Freakouts, and Stakeouts from Black Hat | Class Central