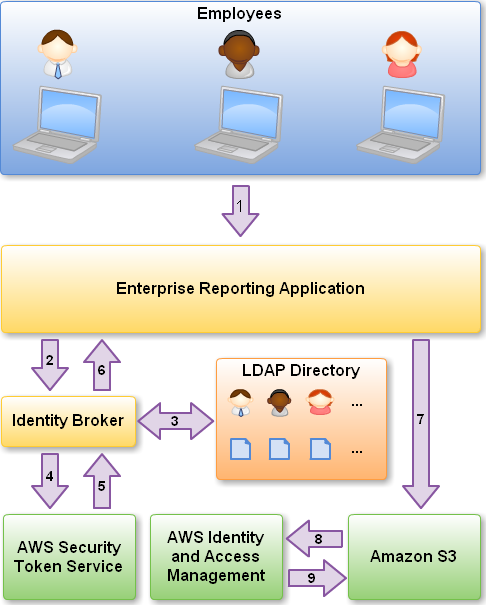
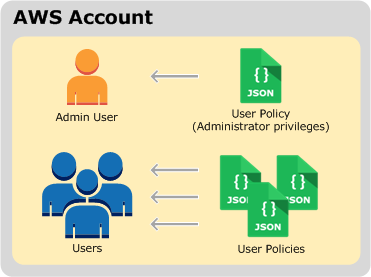
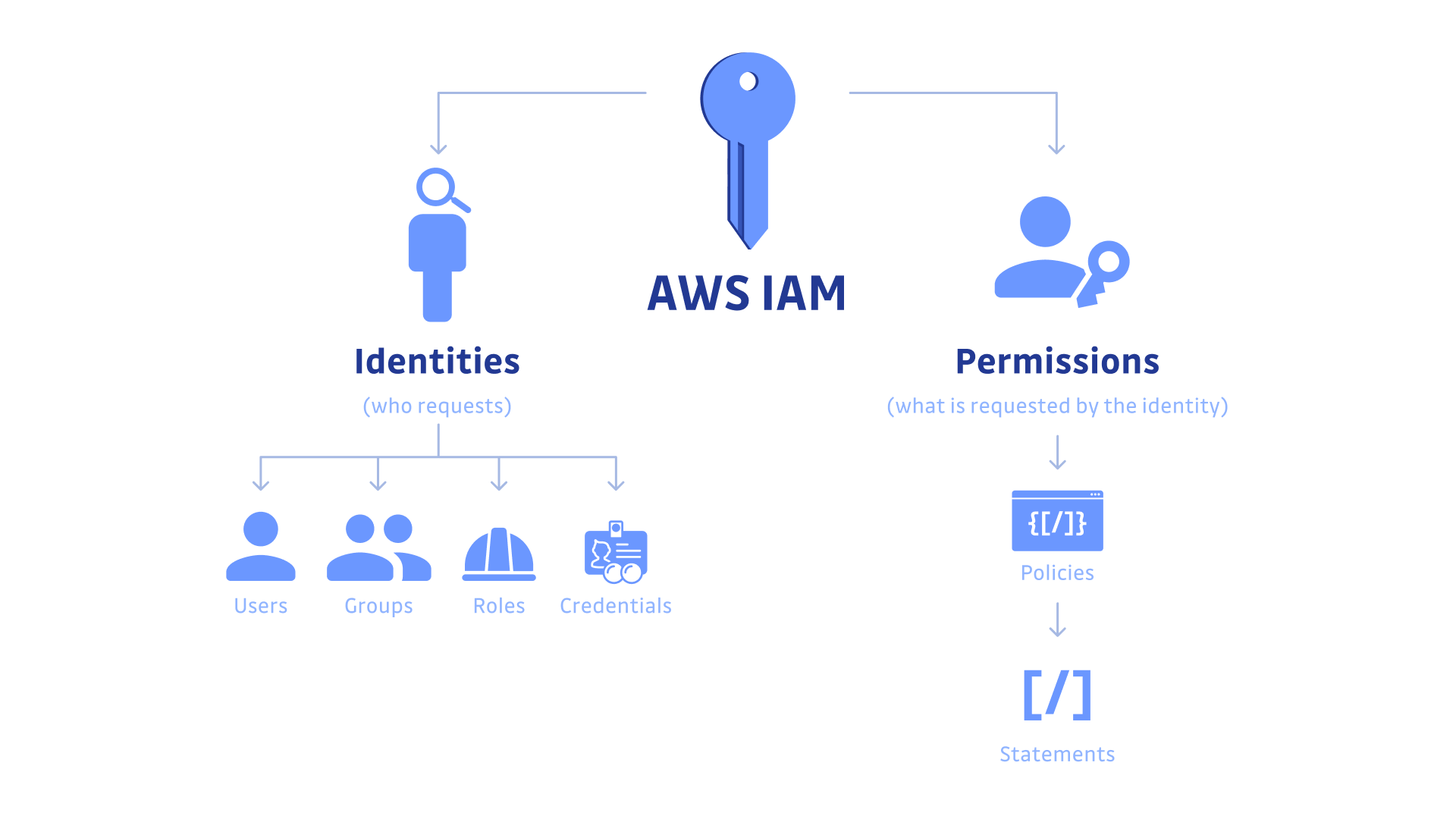
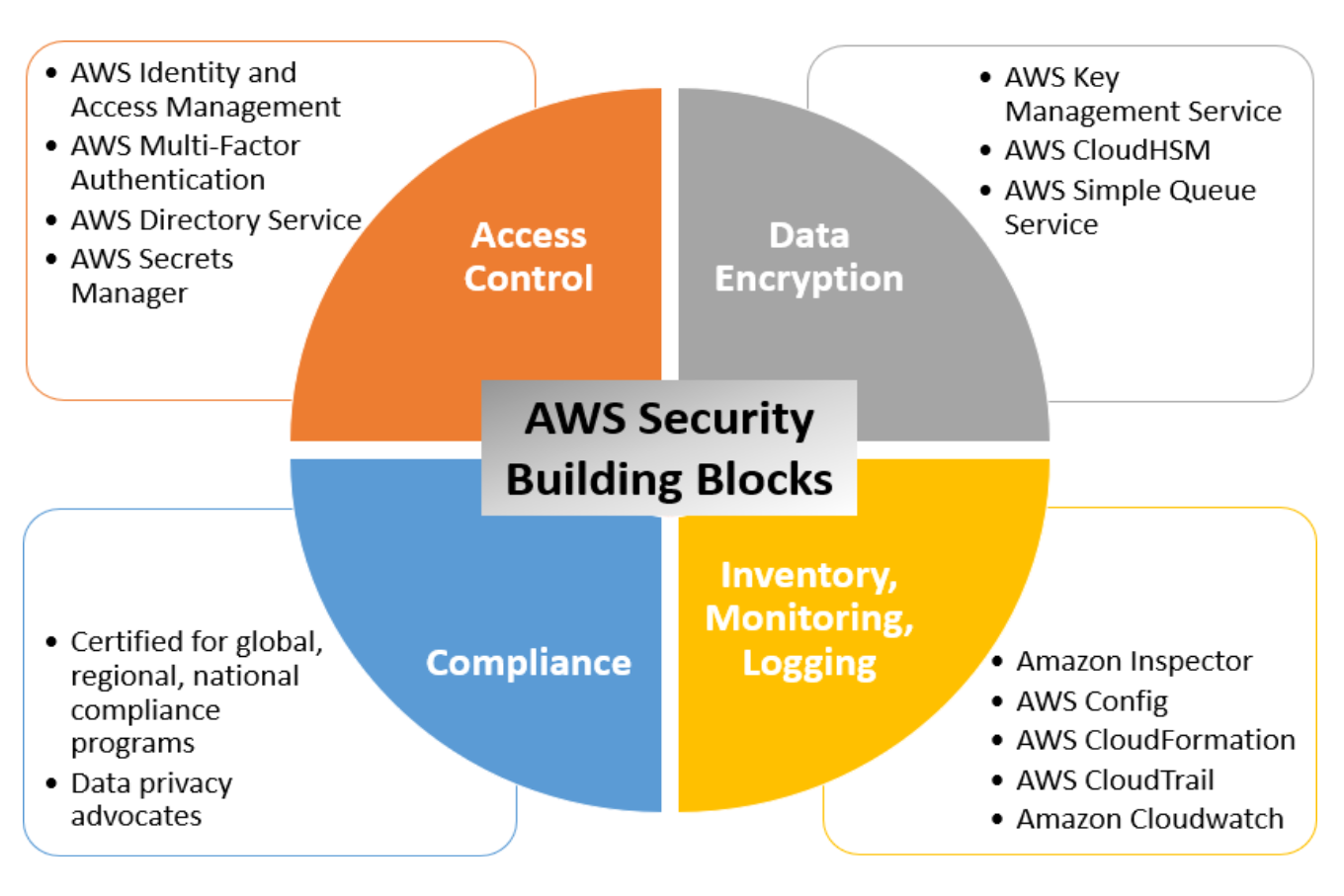
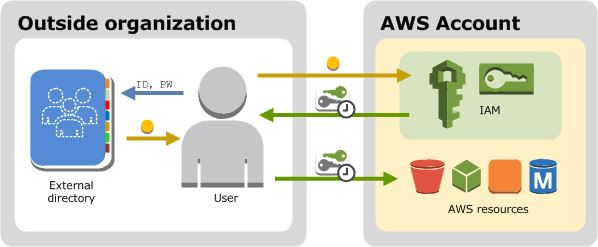
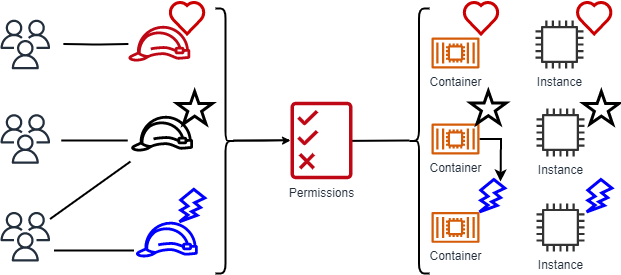
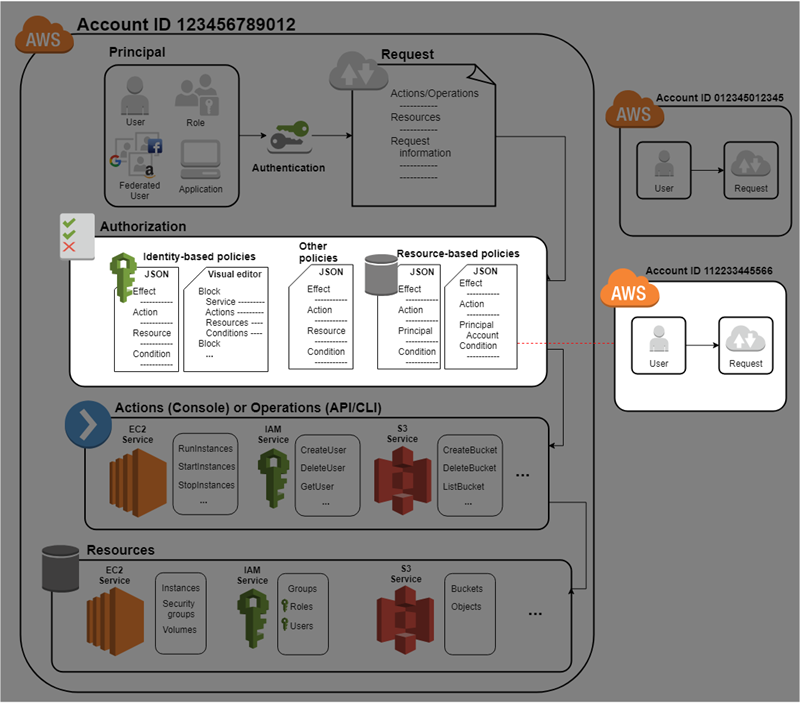
Role-based access control in Amazon OpenSearch Service via SAML integration with AWS IAM Identity Center | AWS Big Data Blog

Role-based access control using Amazon Cognito and an external identity provider | AWS Security Blog

IAM makes it easier for you to manage permissions for AWS services accessing your resources | AWS Security Blog

Scale your authorization needs for Secrets Manager using ABAC with IAM Identity Center | AWS Security Blog

Use attribute-based access control with AD FS to simplify IAM permissions management | AWS Security Blog