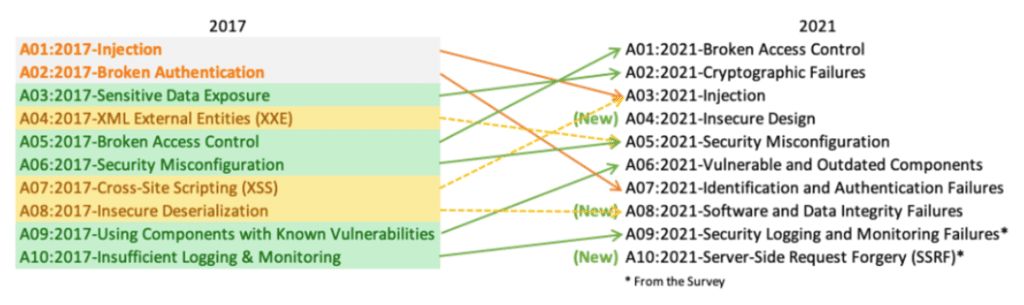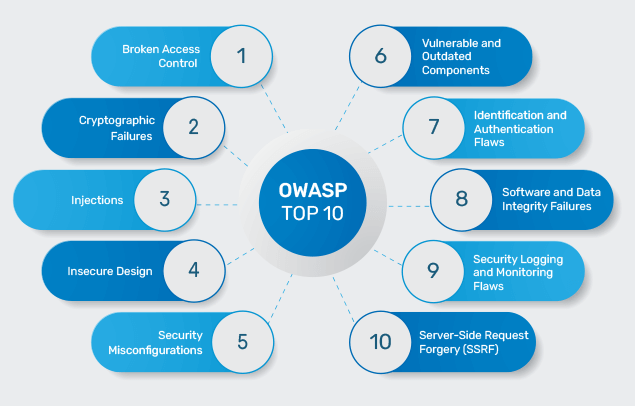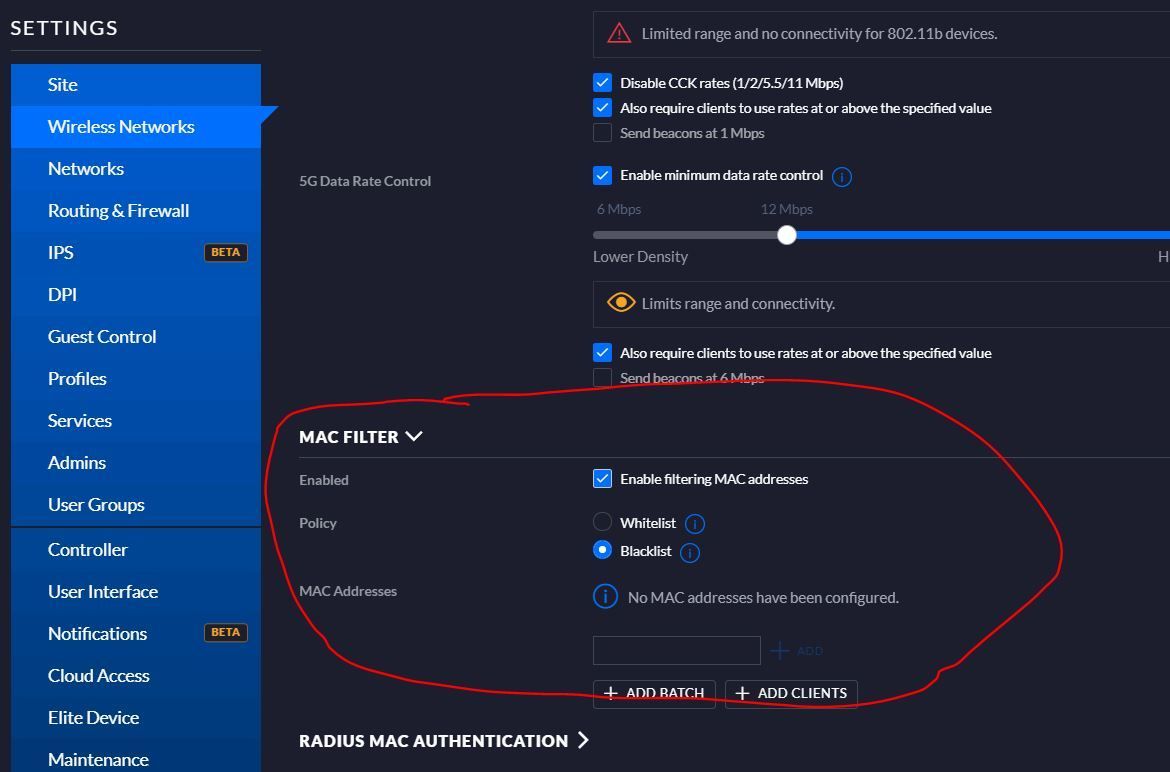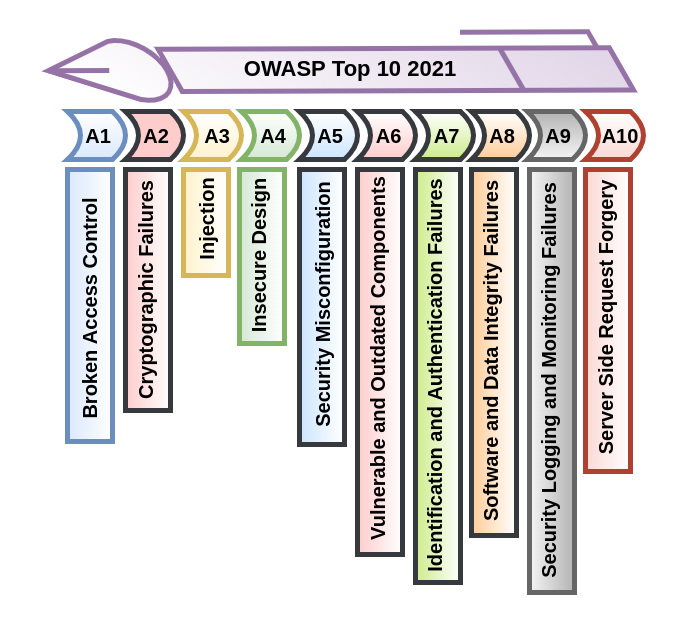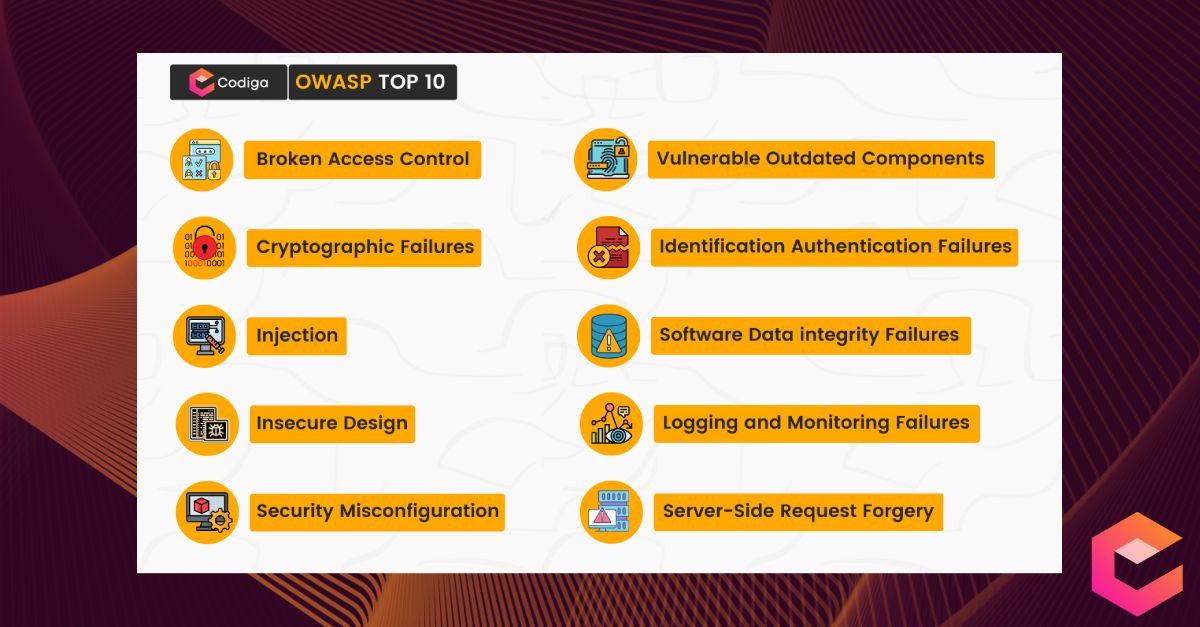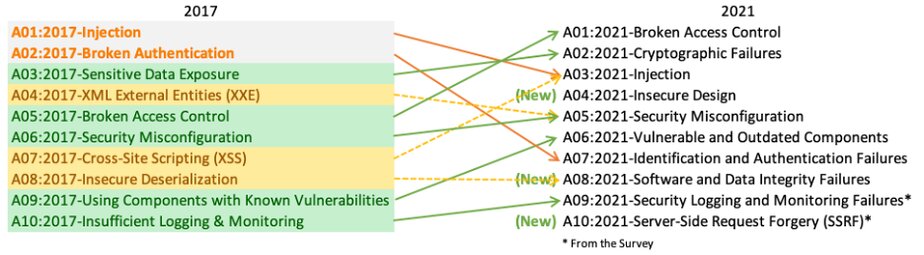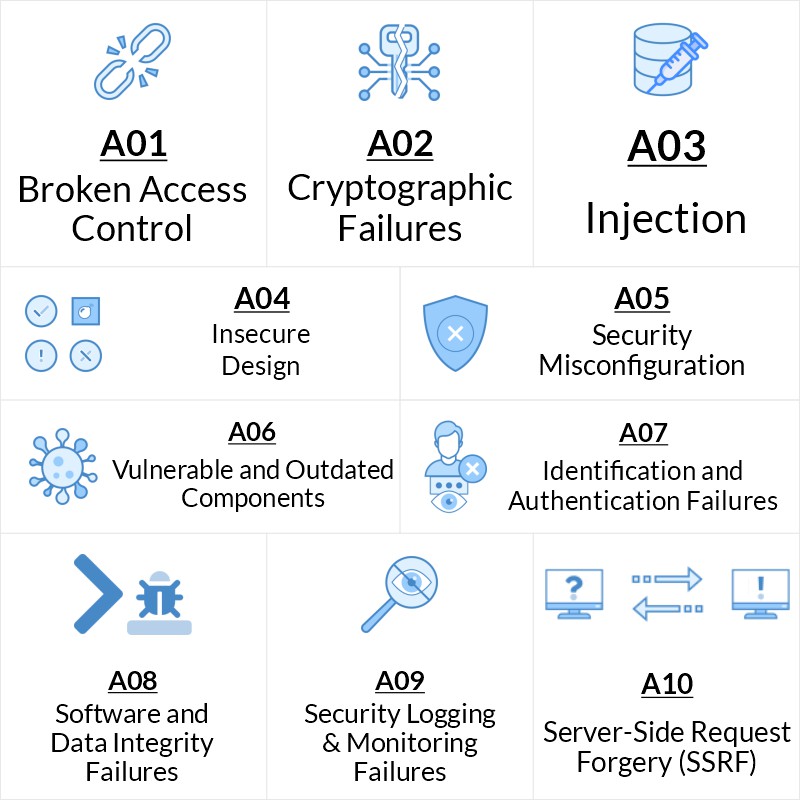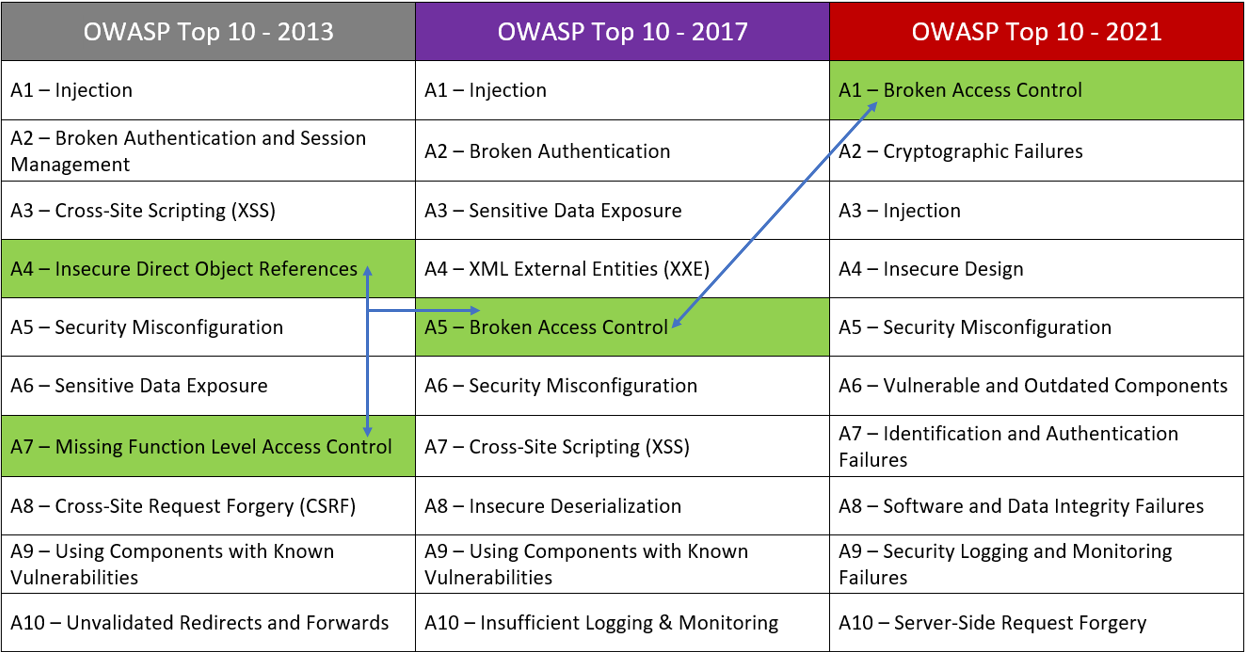
Rise of Broken Access Control. Why authorization flaws are trendy and… | by Rafin Rahman Chy | InfoSec Write-ups

Online Course: OWASP Top 10: #1 Broken Access Control and #2 Cryptographic Failures from LinkedIn Learning | Class Central

It's Official, Broken Access Control is the #1 Threat to your Cloud Application | by Ashish Kar | Medium
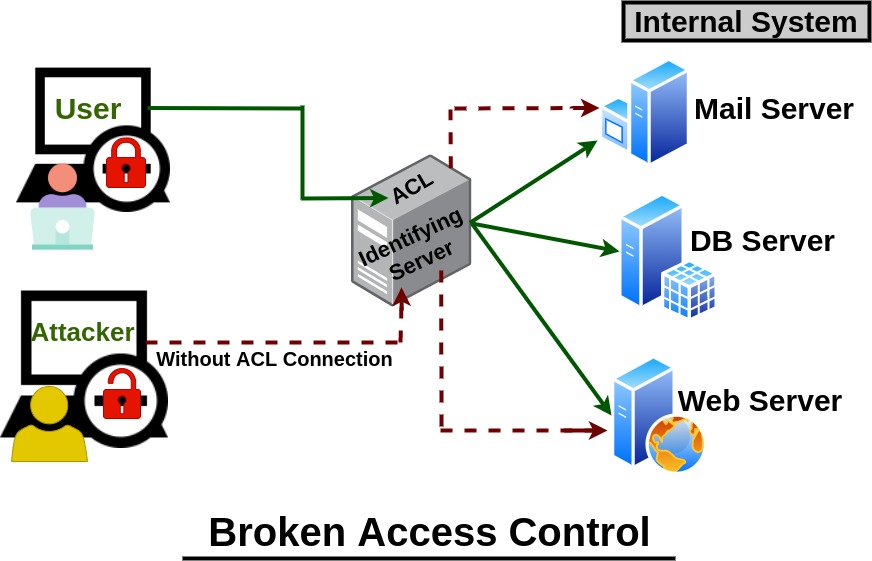
Comprehension The Risk of "Broken Authentication & Broken Access Control" - The most popular web application threats - Cloudkul