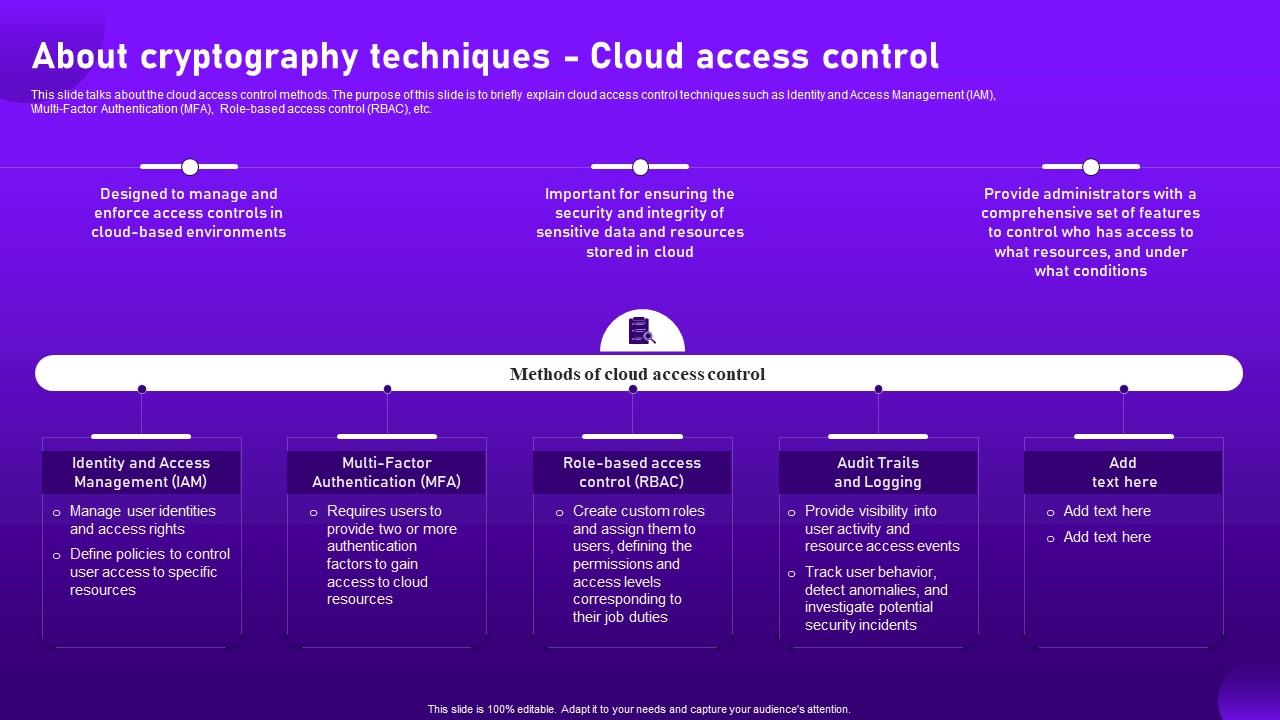
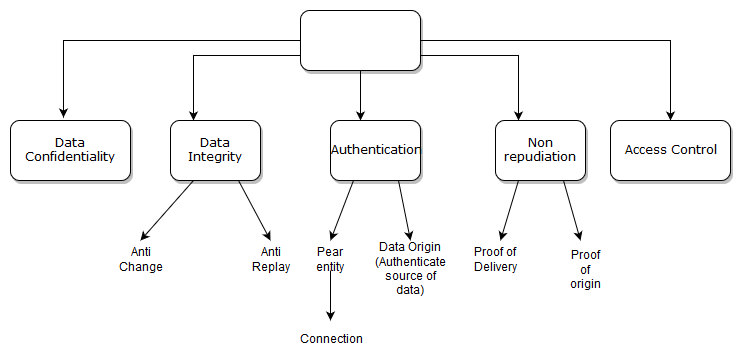
Authentication and Access Control: Practical Cryptography Methods and Tools Book - EVERYONE - Skillsoft
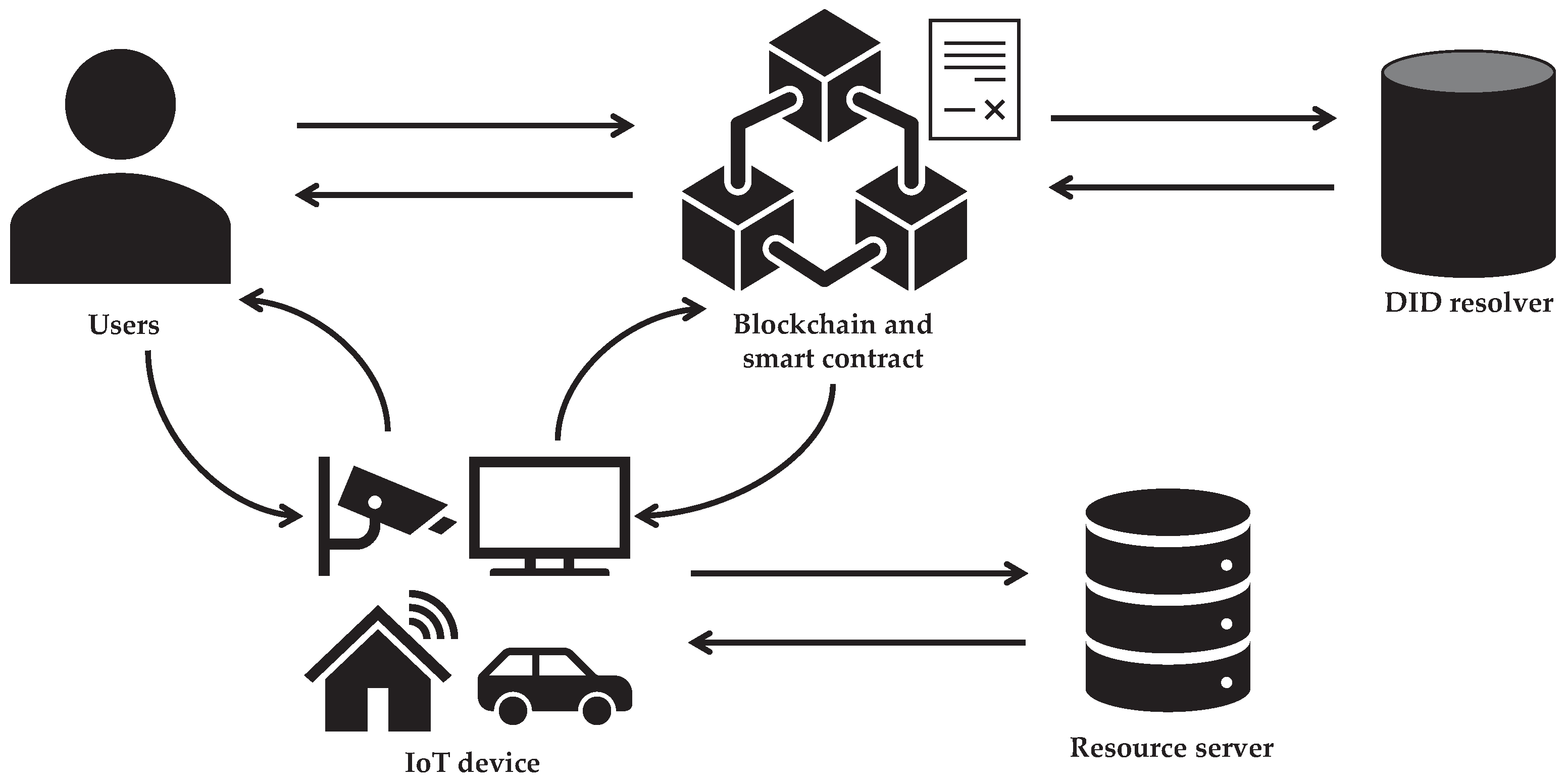
Cryptography | Free Full-Text | Enhanced Authentication for Decentralized IoT Access Control Architecture

Authentication and Access Control: Practical Cryptography Methods and Tools : Boonkrong, Sirapat: Amazon.de: Bücher

Blockchain-envisioned access control for internet of things applications: a comprehensive survey and future directions | Telecommunication Systems