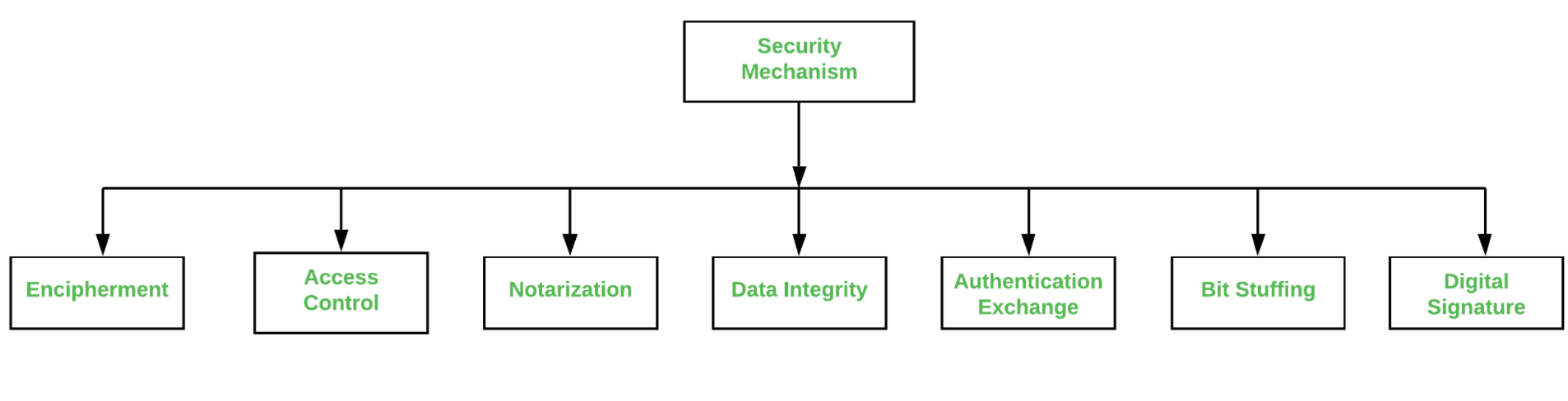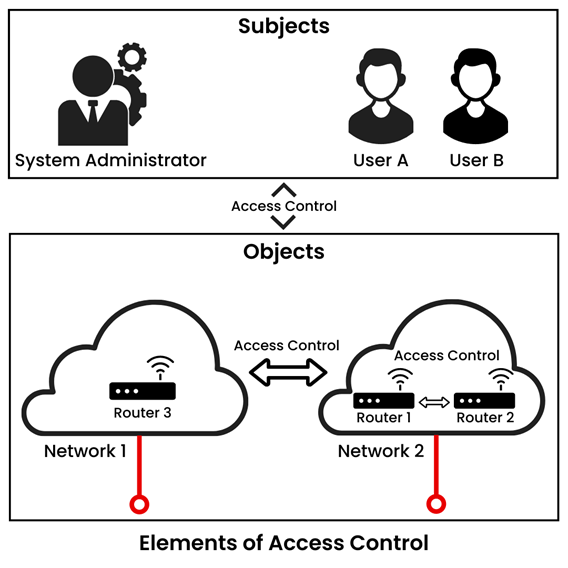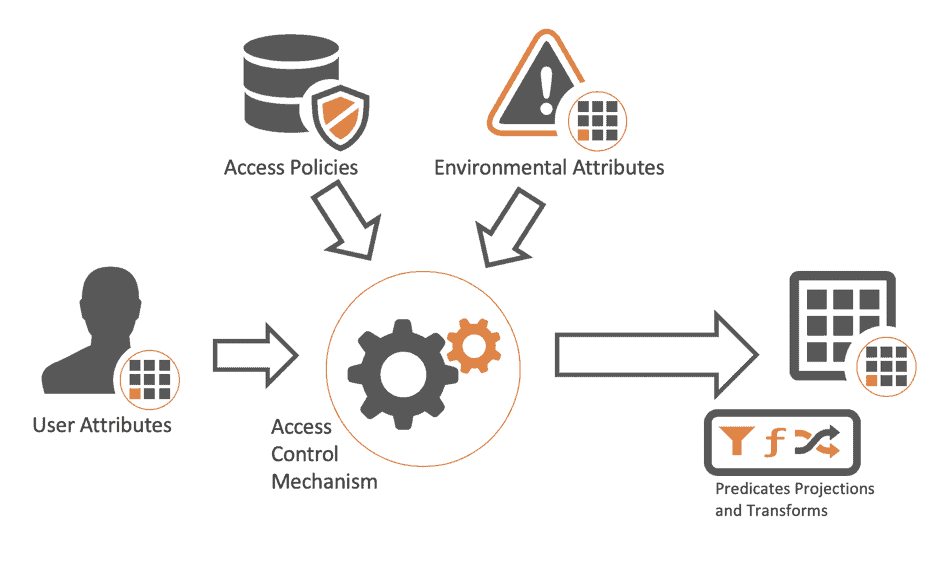
Symmetry | Free Full-Text | Permission-Based Separation of Duty in Dynamic Role-Based Access Control Model
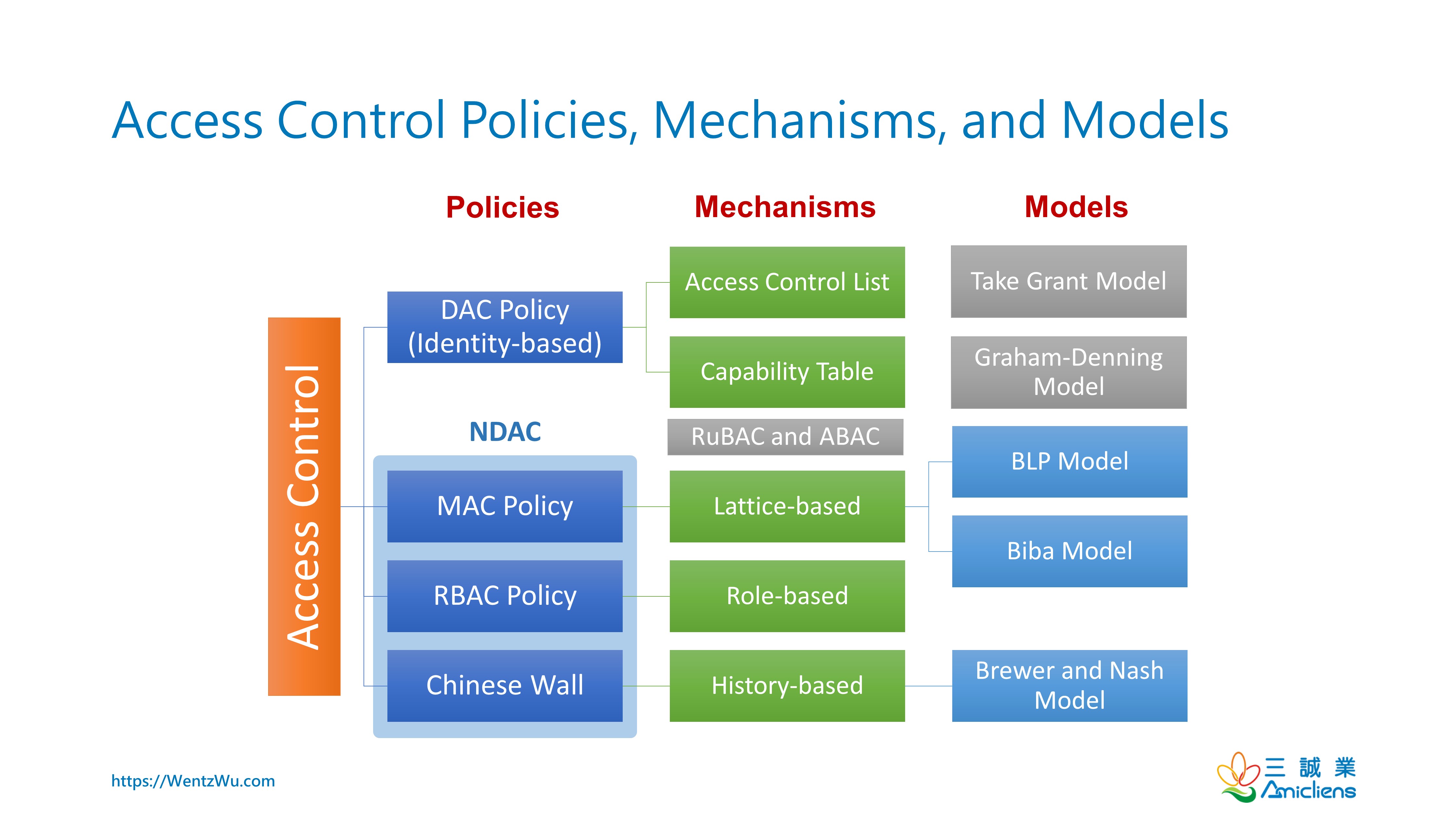
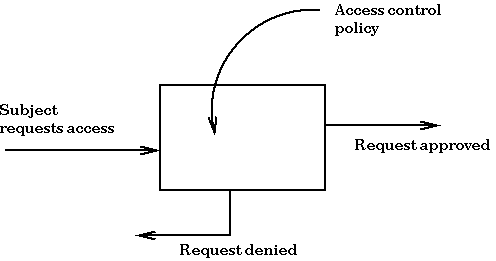
Discretionary and Non-Discretionary Access Control Policies by Wentz Wu, CISSP-ISSAP,ISSEP,ISSMP,SSCP,CCSP,CGRC,CSSLP,CISM,PMP,CBAPWentz Wu

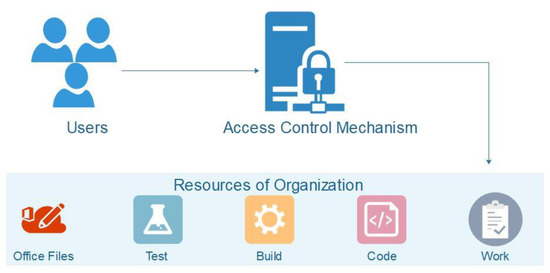
Architecture Of Access Control Mechanism In Run Time Change Management | Download Scientific Diagram




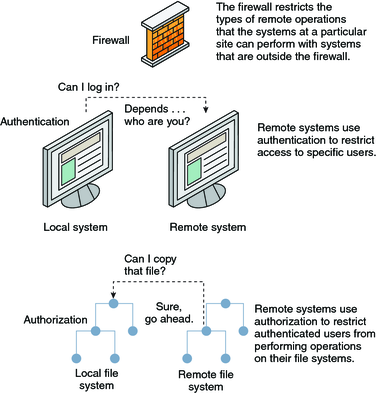
/An%20open%20source%20policy%20language%20for%20Attribute-Stream%20Based%20Access%20Control%20(ASBAC)/attribute-based_access_control_mechanism.png)