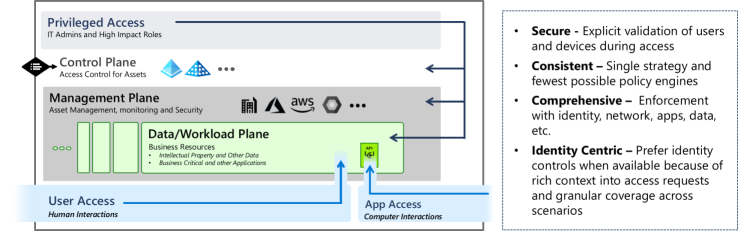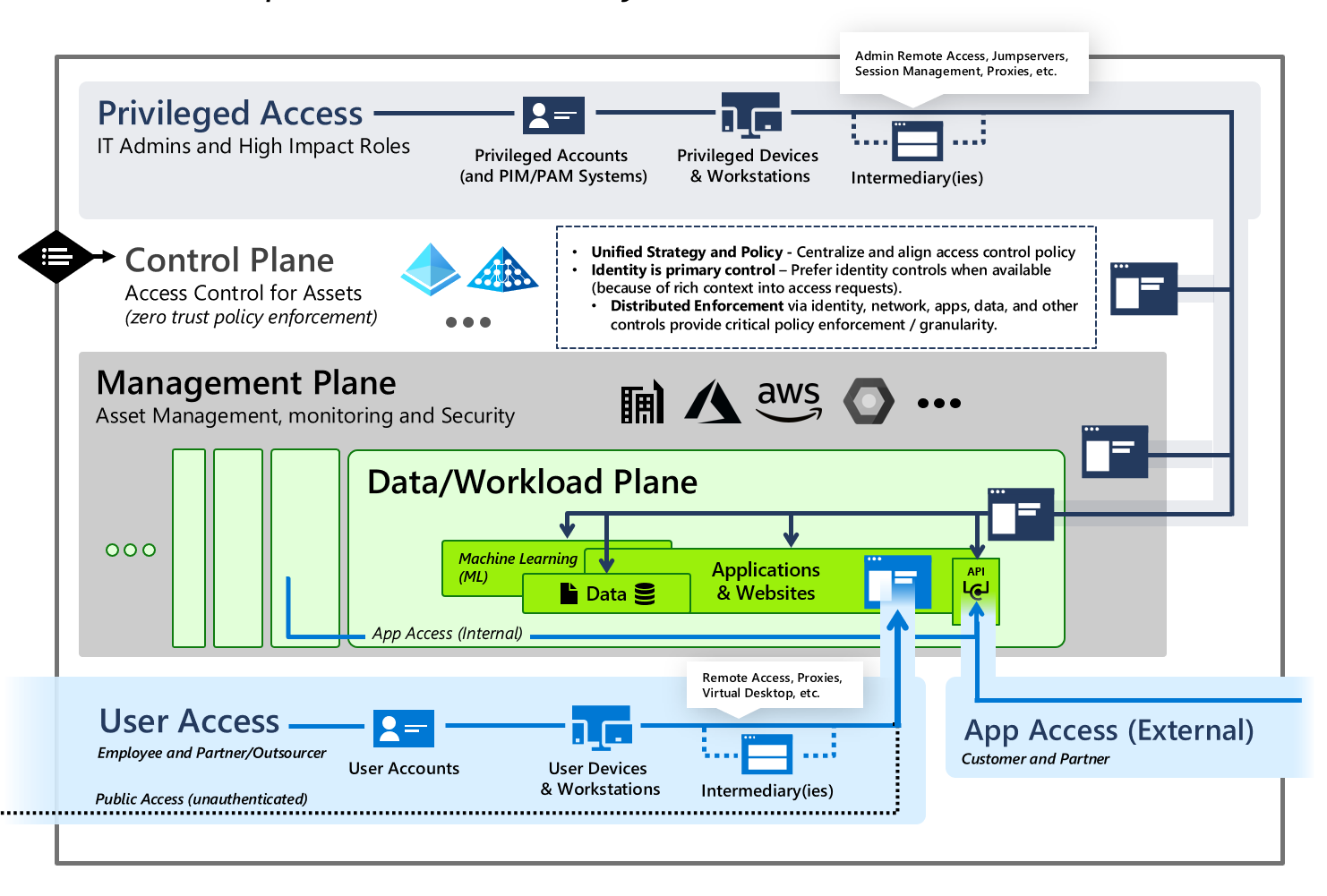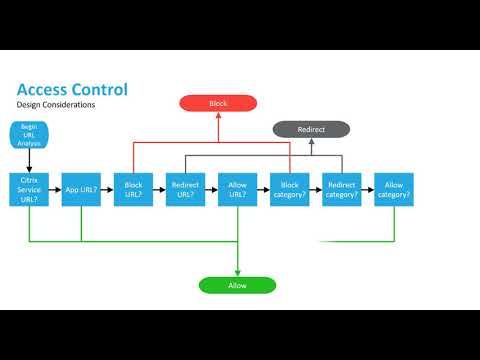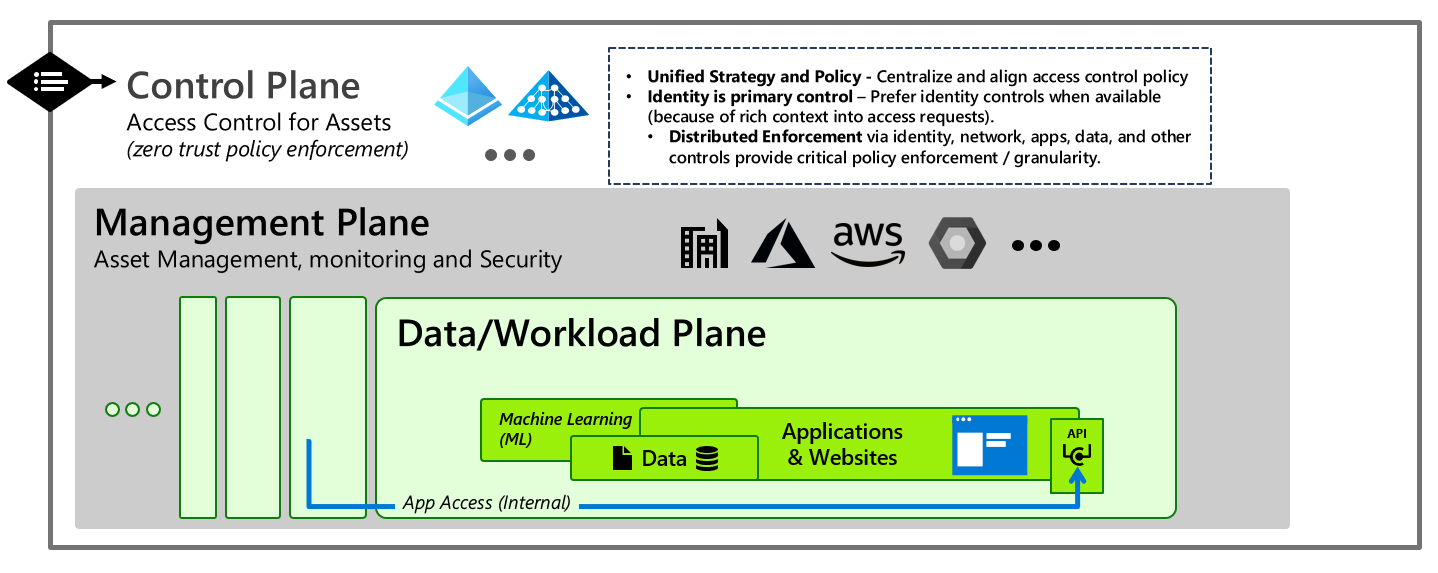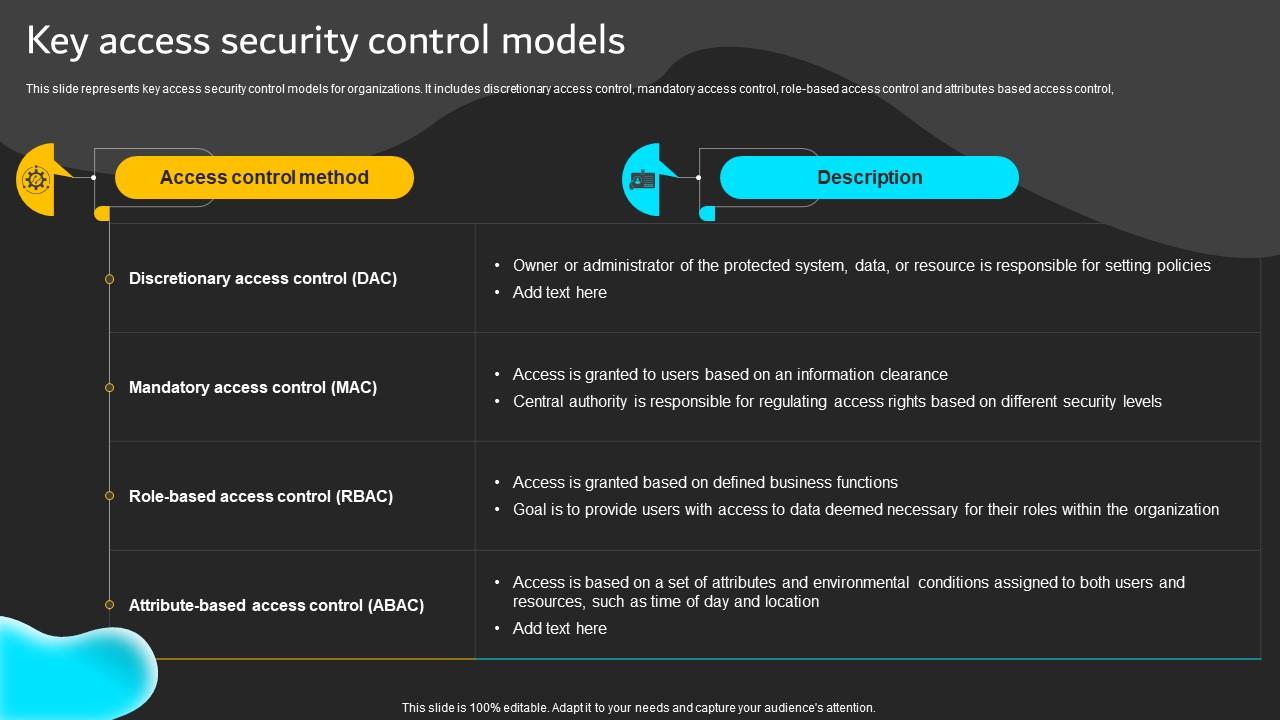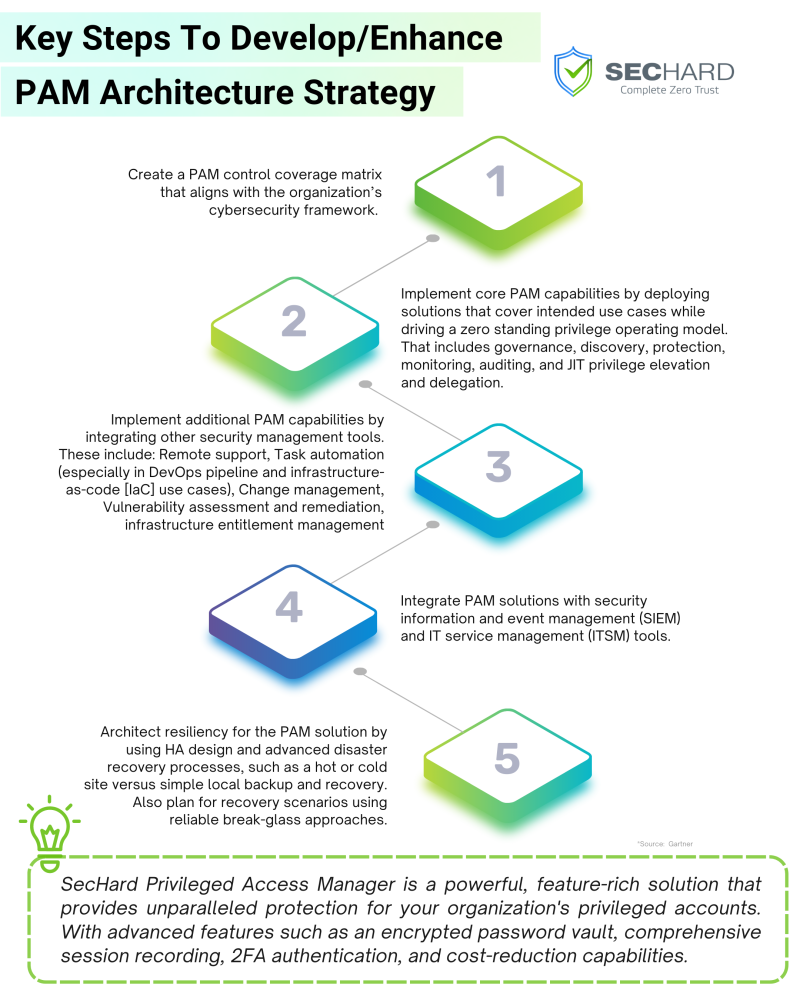
A Comprehensive Guide to Developing an Effective PAM (Privileged Access Management) Architecture Strategy - SecHard

Example of the access control strategy in multi-RF backscatter network. | Download Scientific Diagram
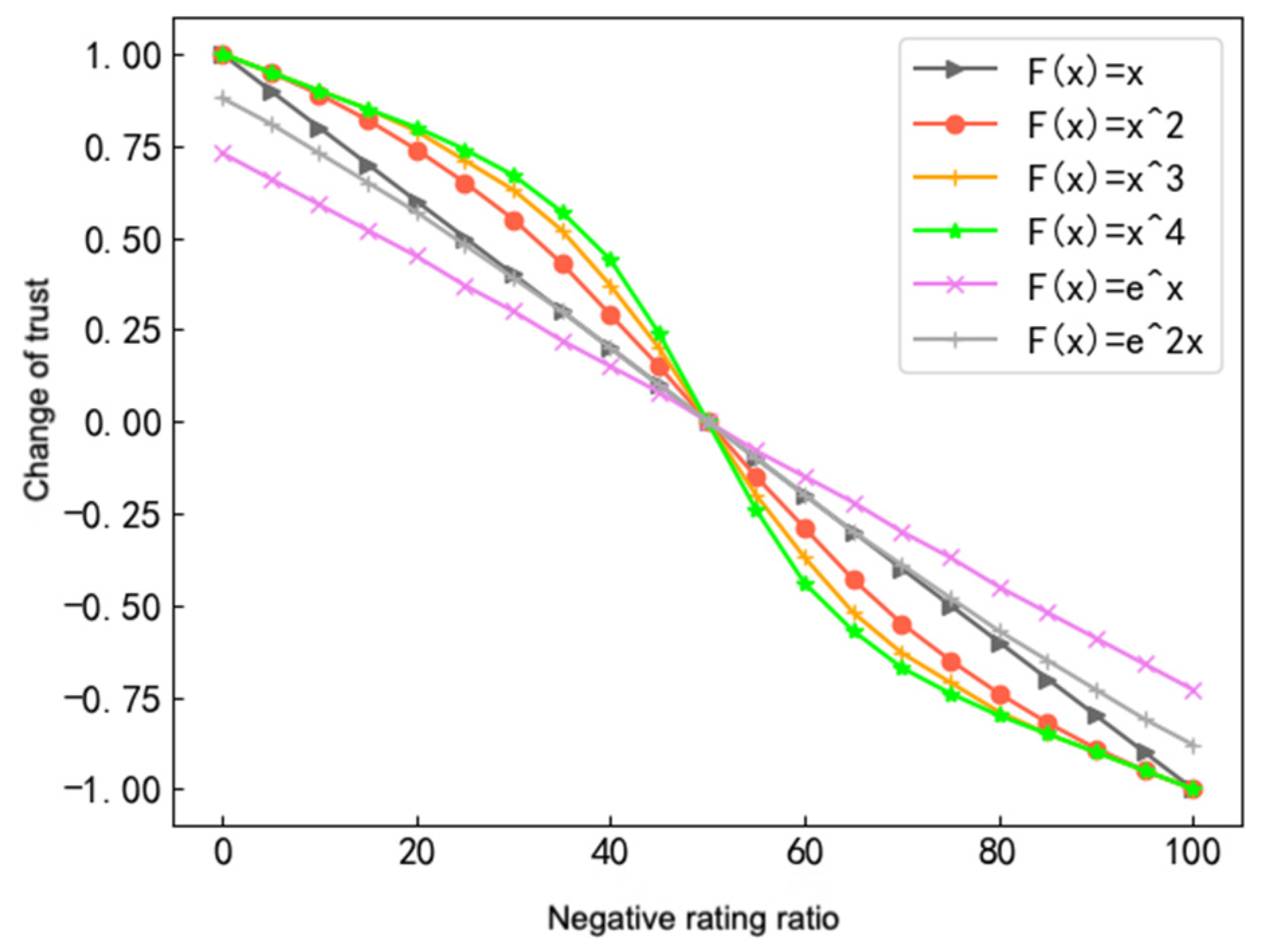
Electronics | Free Full-Text | Access Control Strategy for the Internet of Vehicles Based on Blockchain and Edge Computing