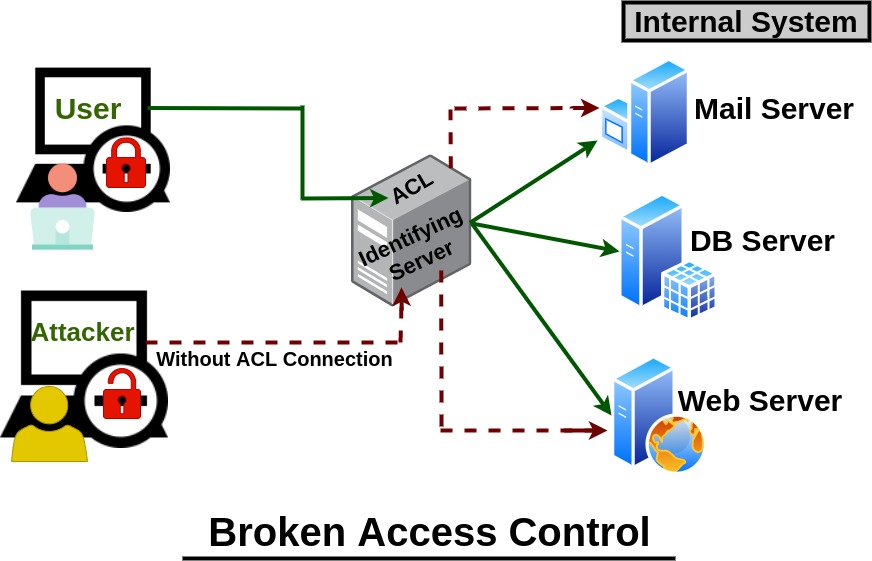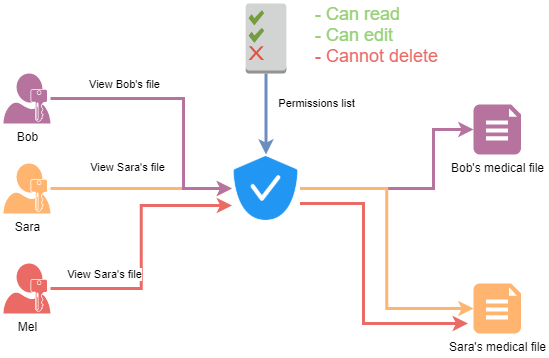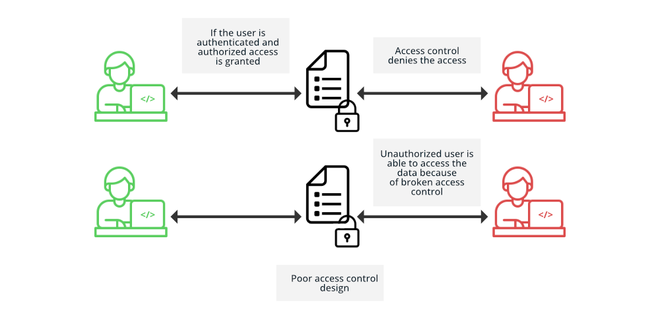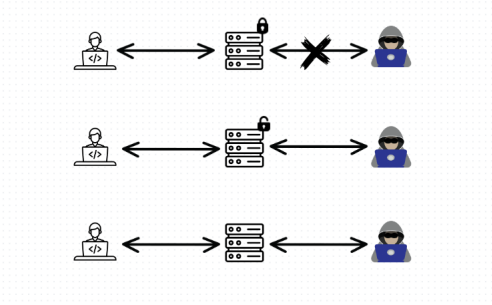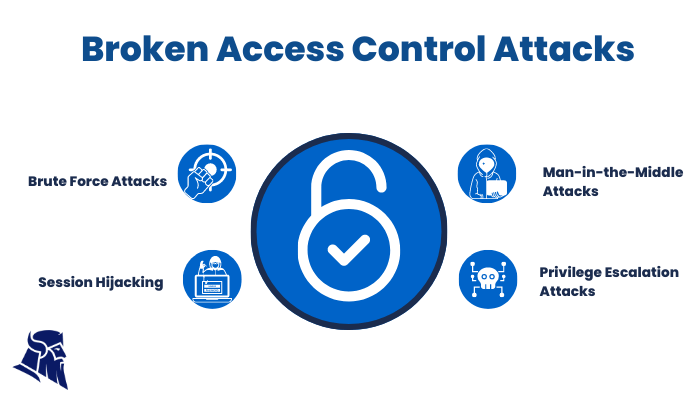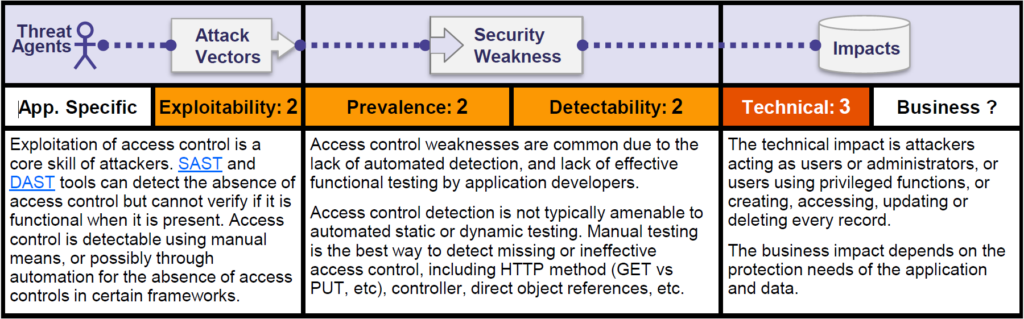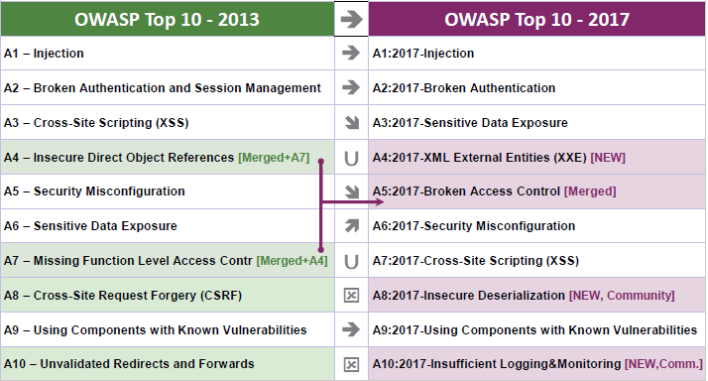
How to Catch Broken Access Control Security Vulnerabilities in Code Review Part 2 | PullRequest Blog

Automated black-box detection of access control vulnerabilities in web applications | Semantic Scholar

How to Catch the Top OWASP 2021 Security Category - Broken Access Control - in Code Review | PullRequest Blog