Privilege Creep in Cybersecurity: Definition, Risks, and Prevention Strategies — IT Companies Network
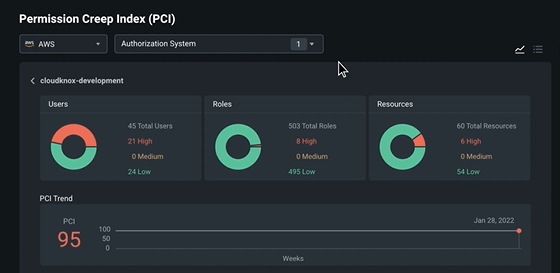
Microsoft makes Entra Permissions Management, formerly CloudKnox, generally available | MSDynamicsWorld.com

CREEP (2004). Copyright: Editorial use only. No merchandising or book covers. This is a publicly distributed handout. Access rights only, no license of copyright provided. Only to be reproduced in conjunction with promotion of this film. Credit: DAN FILMS ...

Privilege Aggregation and Creep by Wentz Wu, CISSP-ISSAP,ISSEP,ISSMP,SSCP,CCSP,CGRC,CSSLP,CISM,PMP,CBAPWentz Wu
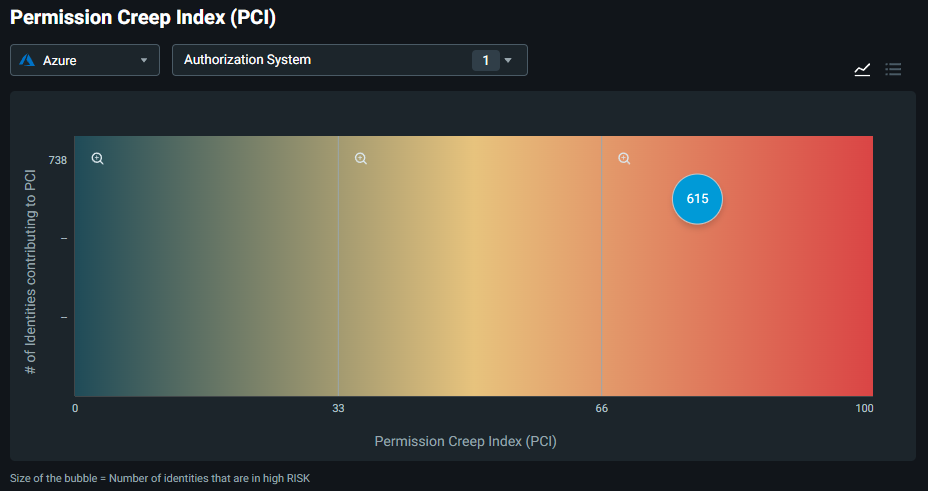
Anzeigen von Statistiken und Daten zu Ihrem Autorisierungssystem in Permissions Management - Microsoft Entra Permissions Management | Microsoft Learn