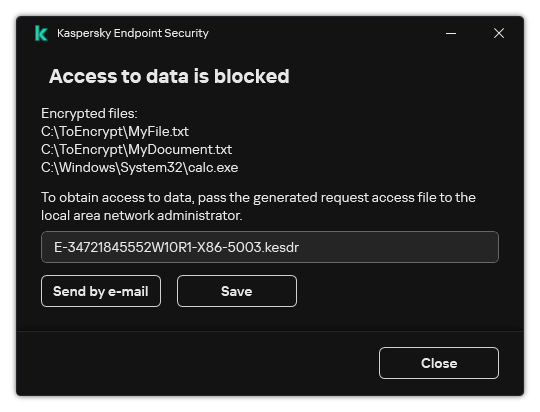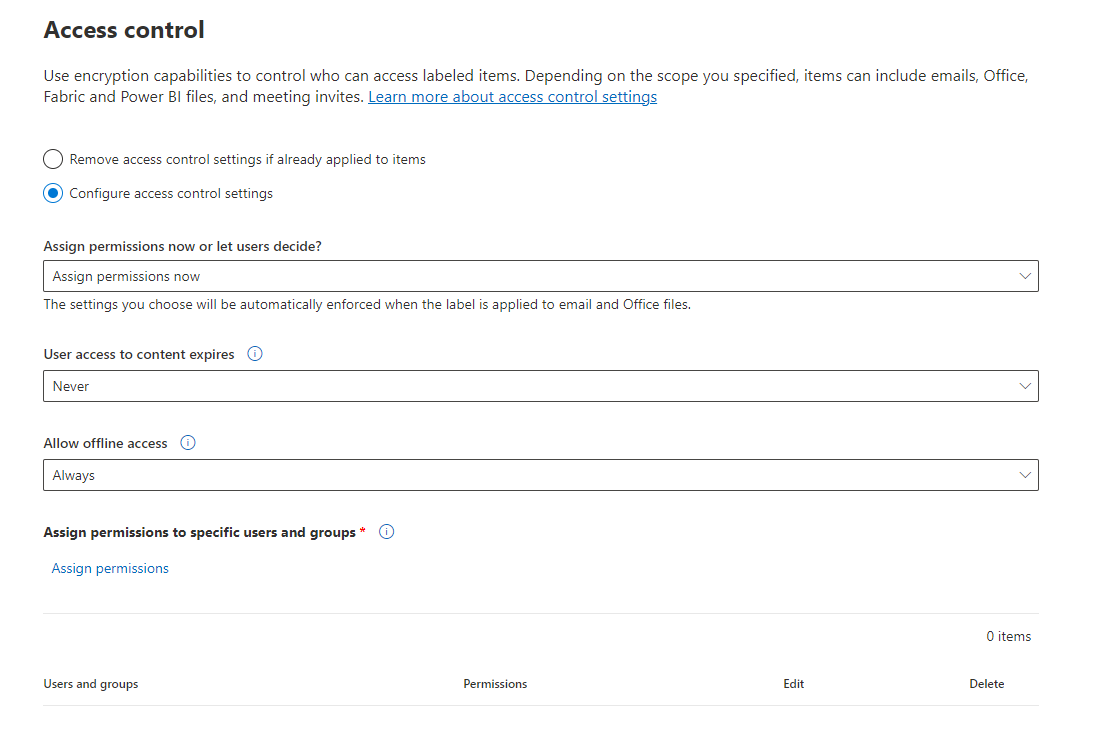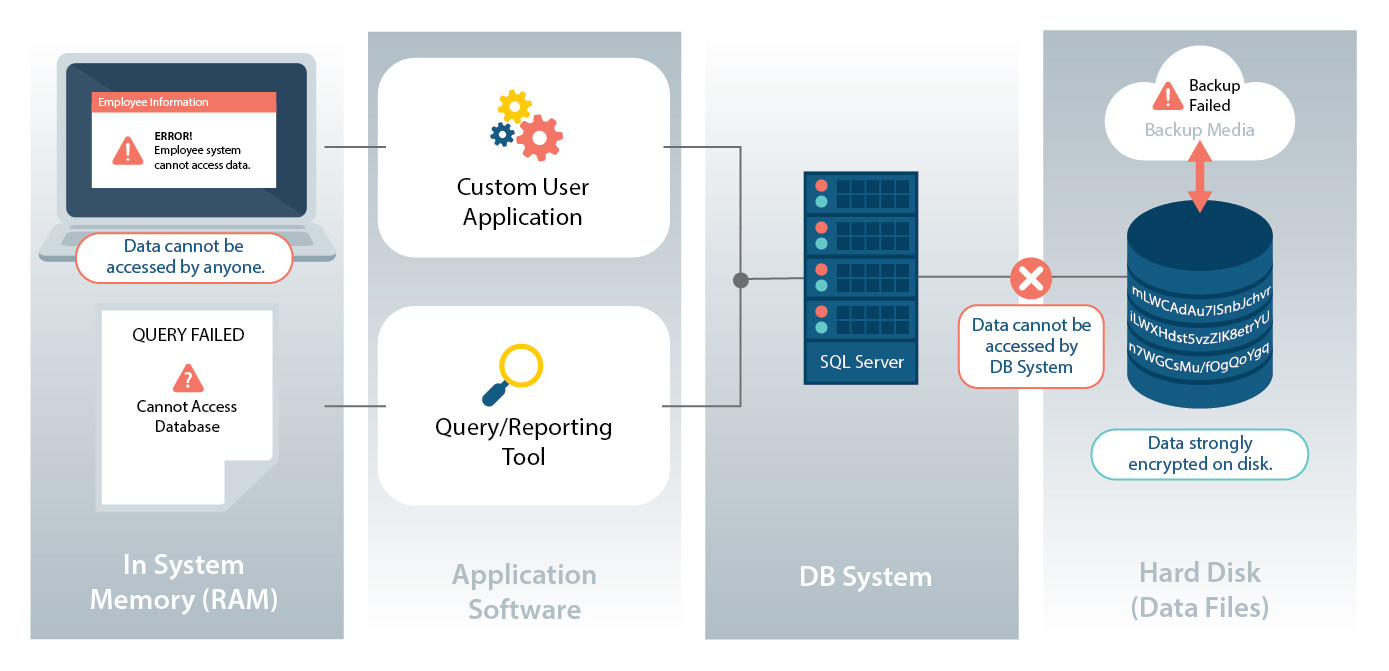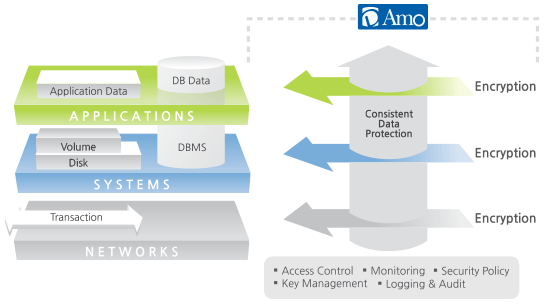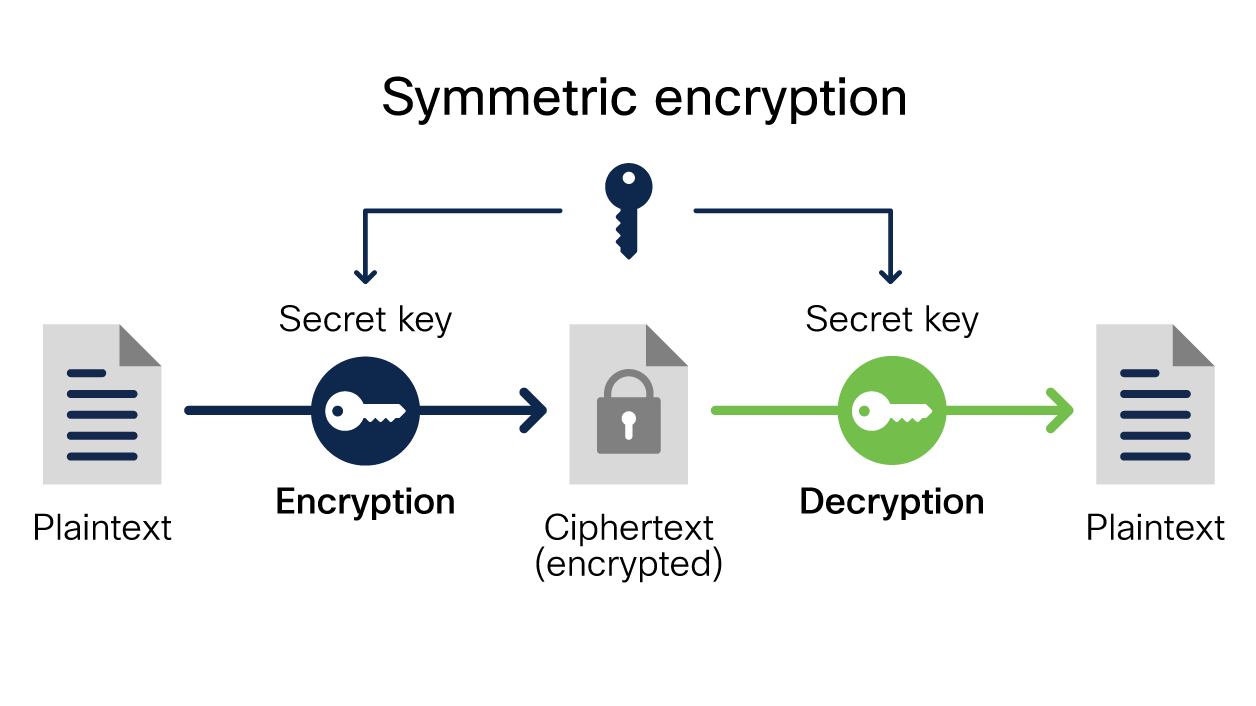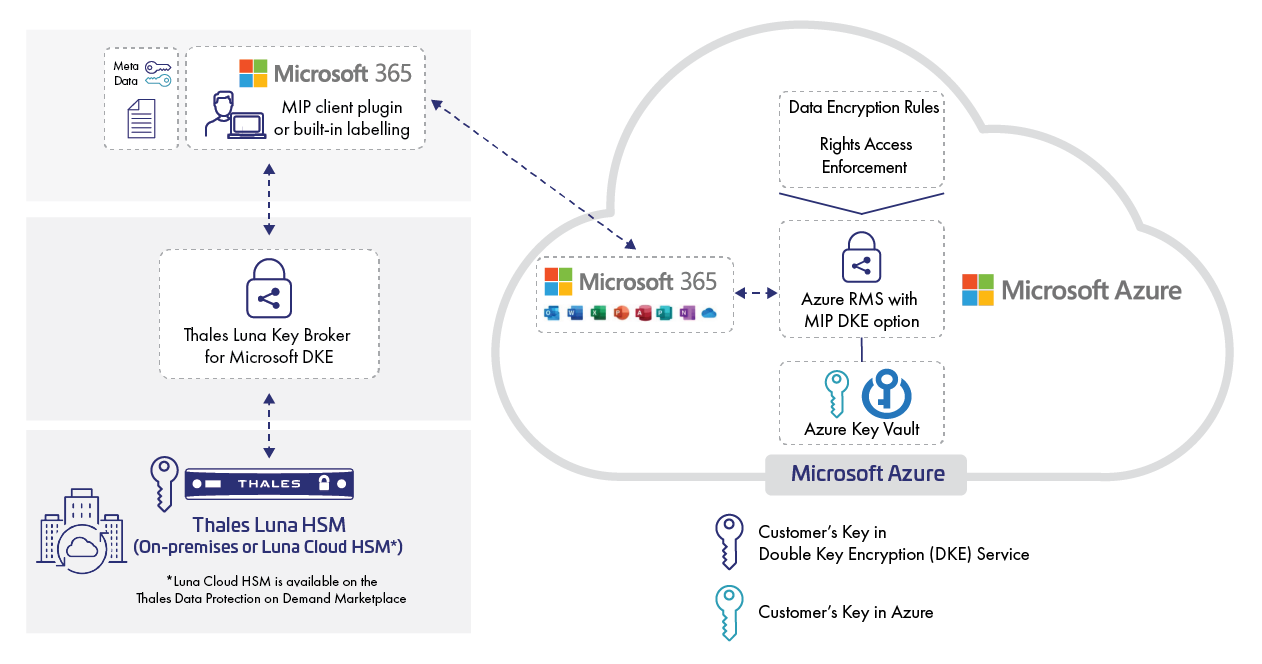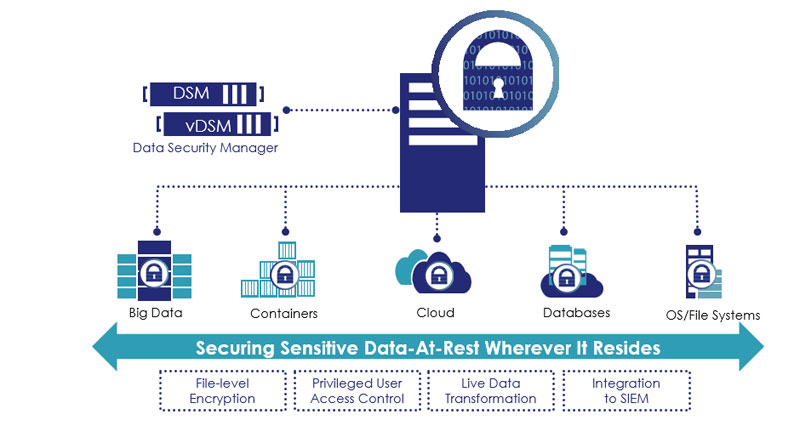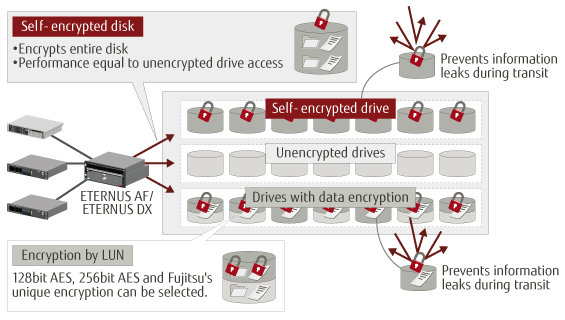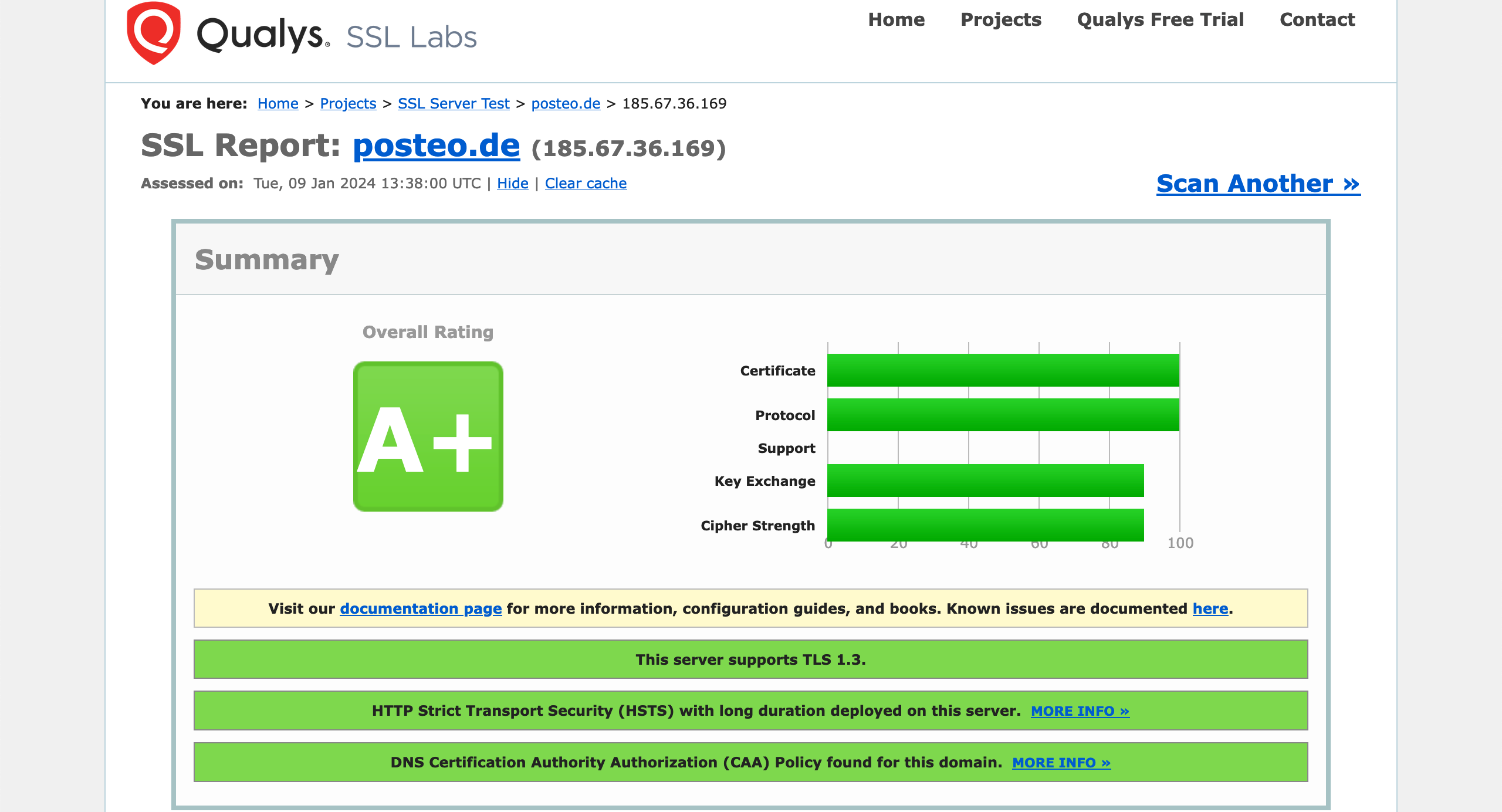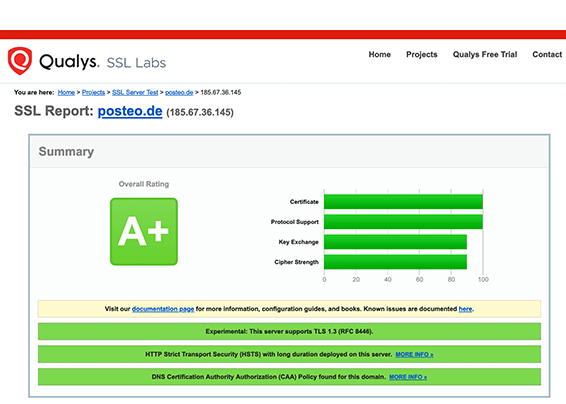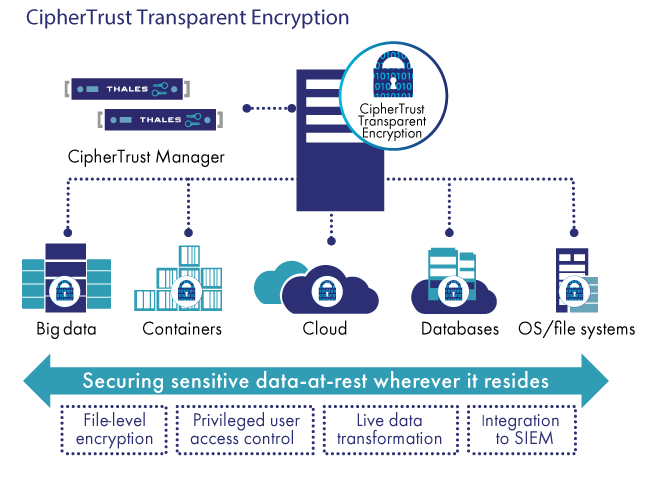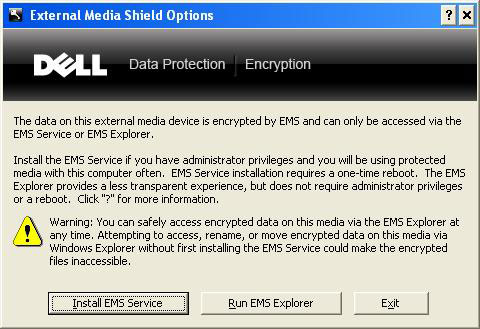
UCI Health Information Services - Data Encryption FAQ: Accessing Encrypted Media from a Non-UC Irvine Medical Center Computer

Invalid private key for encryption app. Please update your private key password in your personal settings to recover access to your encrypted files" - end-to-end-encryption - Nextcloud community
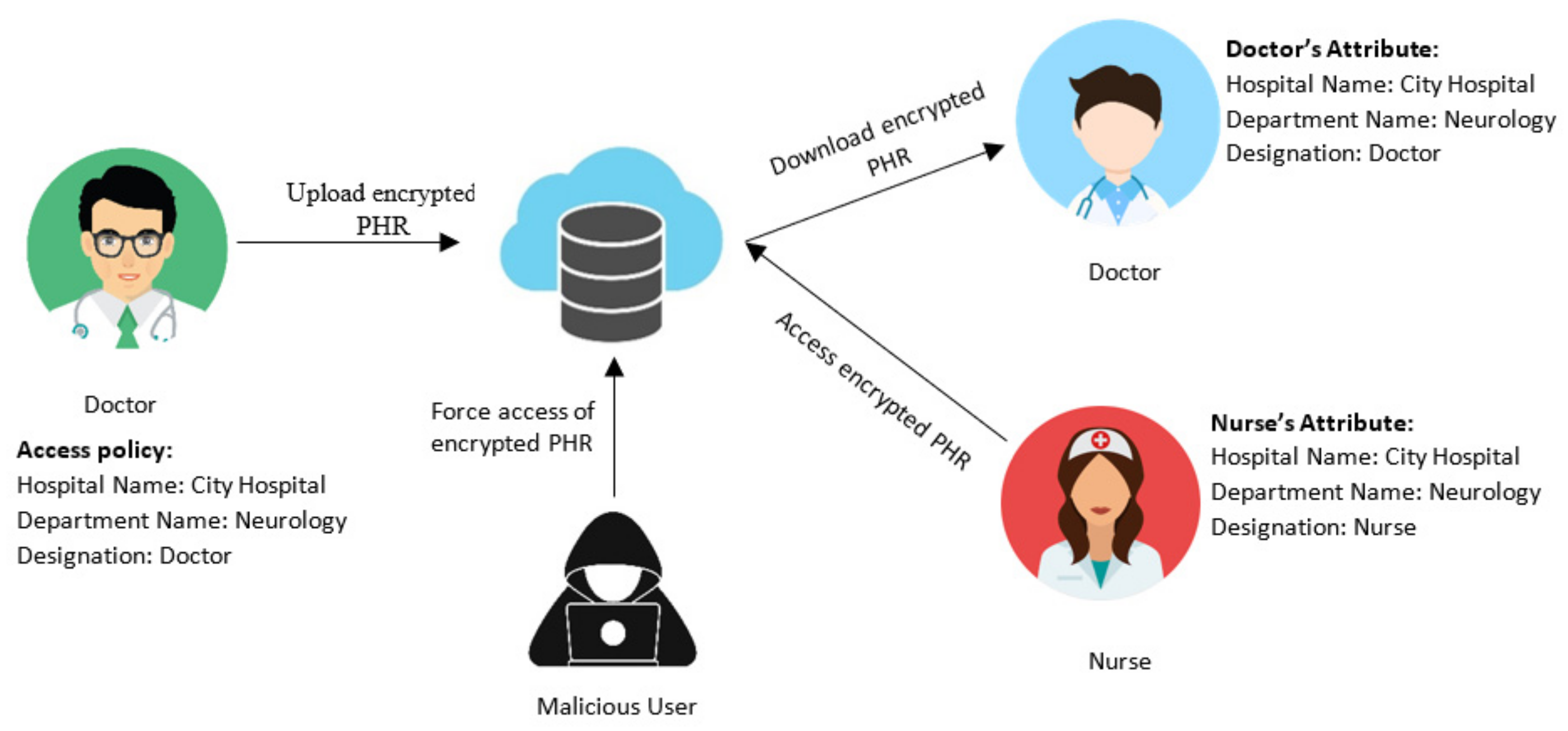
Future Internet | Free Full-Text | Towards Virtuous Cloud Data Storage Using Access Policy Hiding in Ciphertext Policy Attribute-Based Encryption

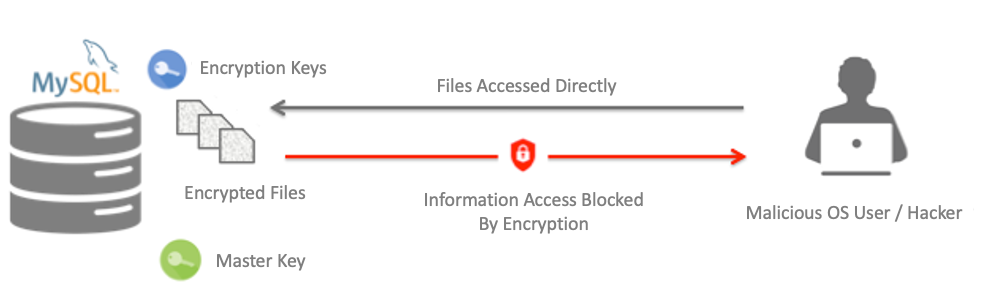
![MS-STOROD]: Encrypted File Access Control and Encryption | Microsoft Learn MS-STOROD]: Encrypted File Access Control and Encryption | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-storod/ms-storod_files/image007.png)