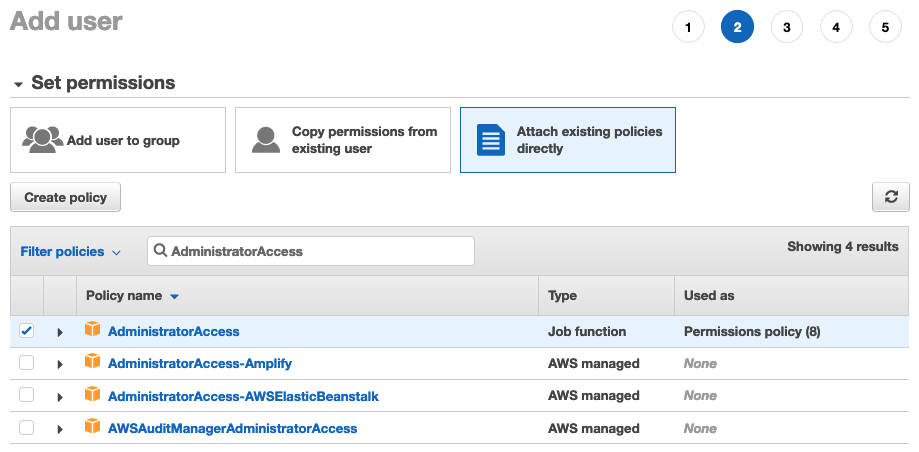
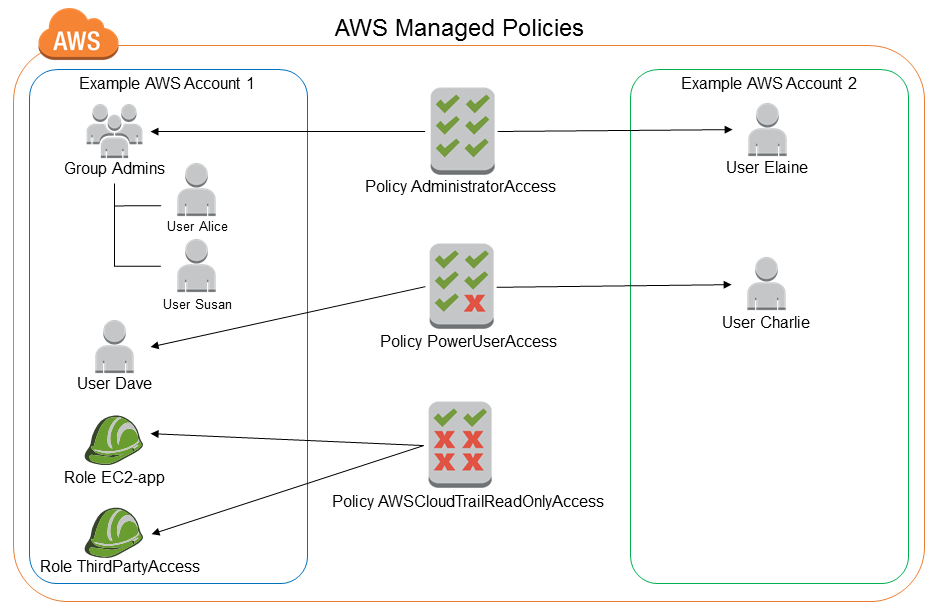
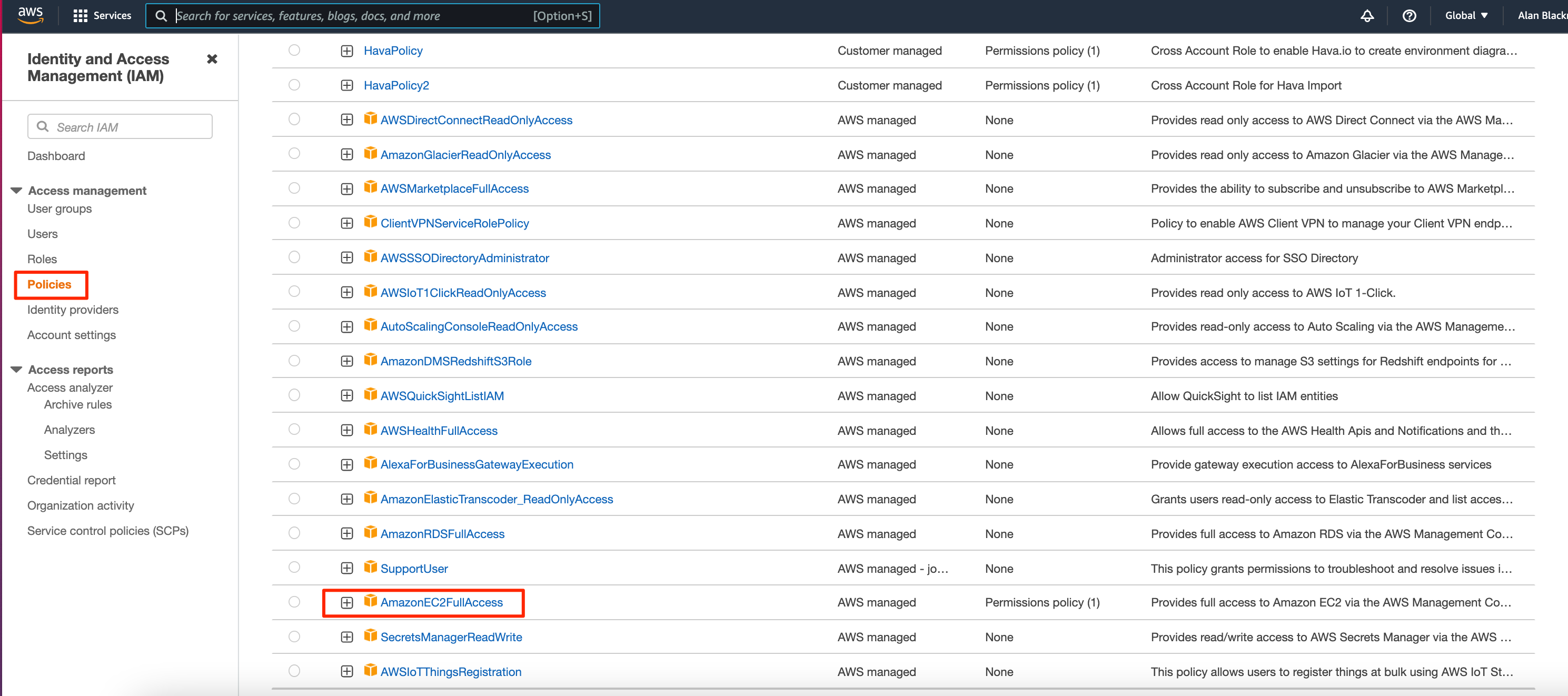
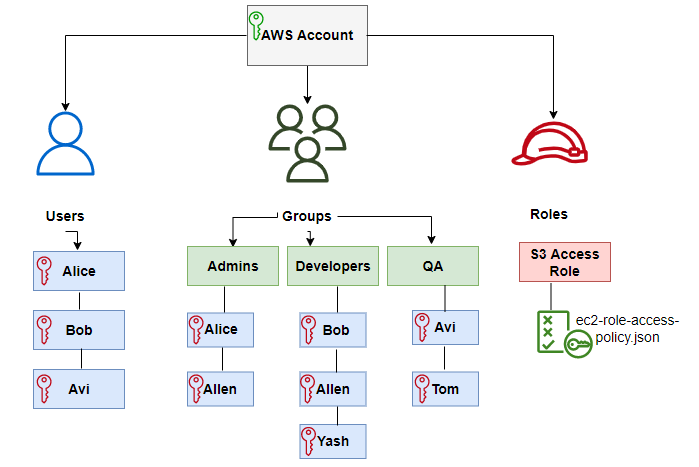
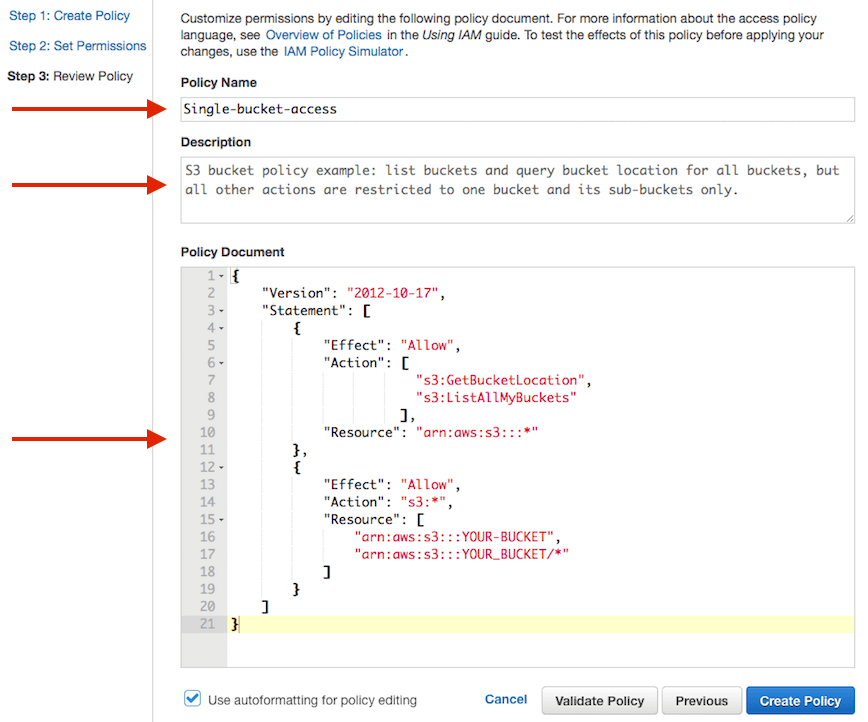
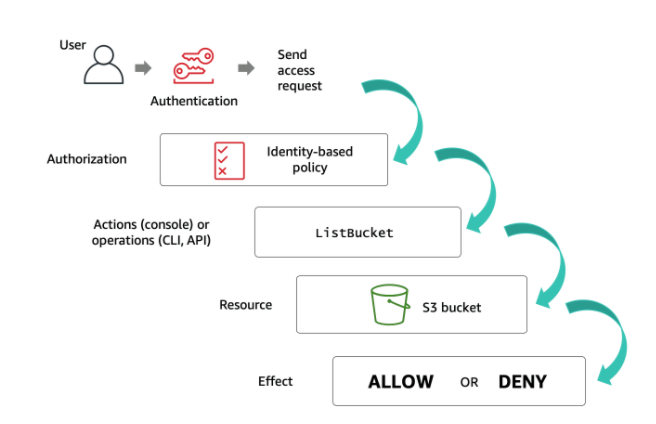
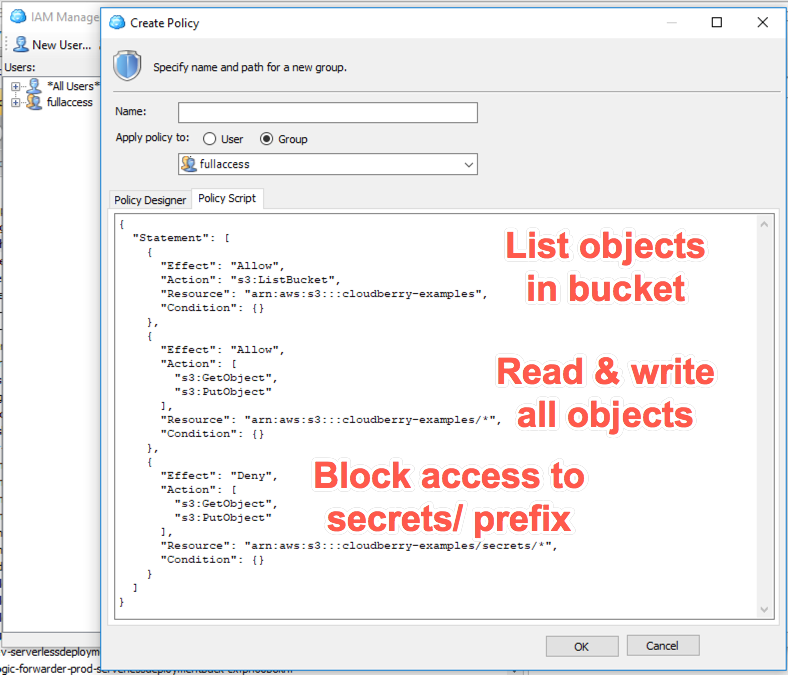
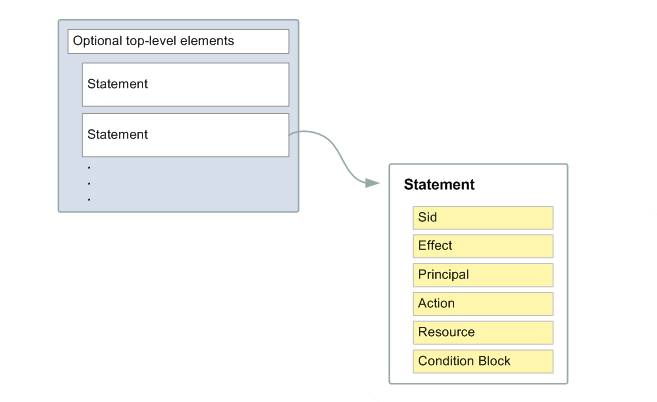
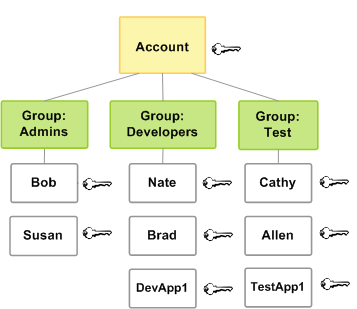
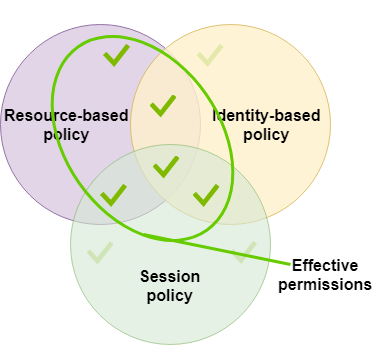
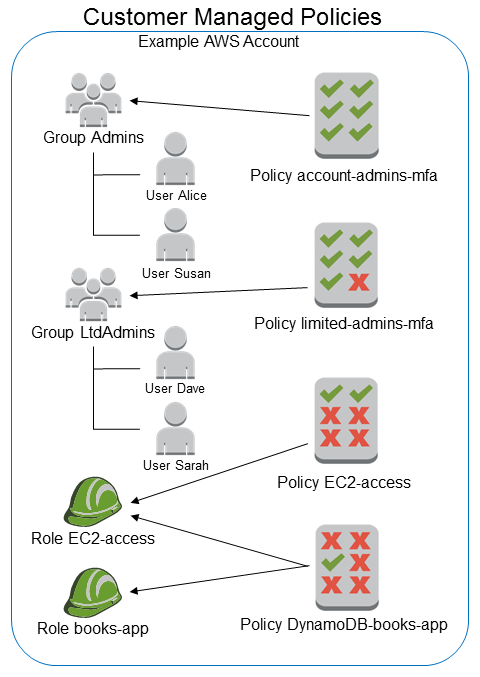
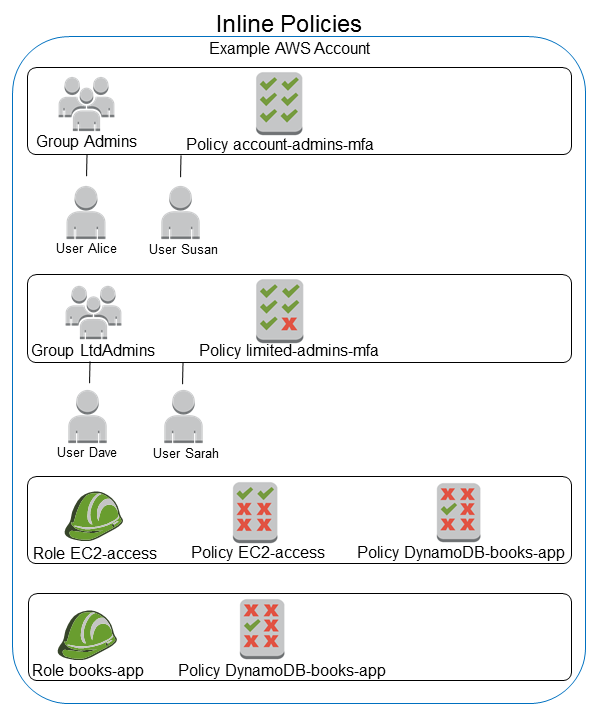
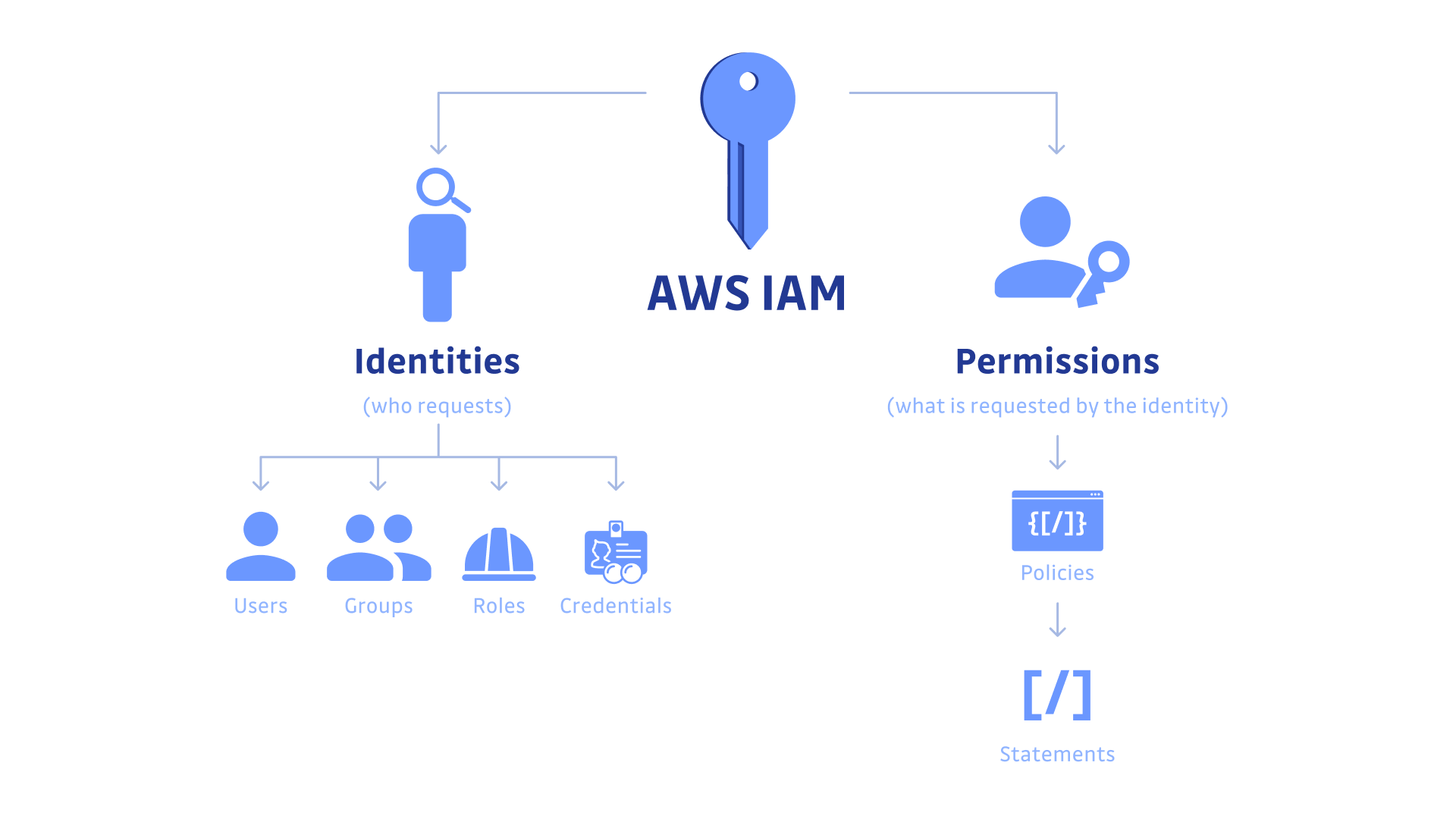
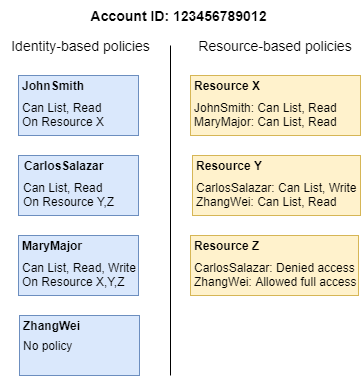
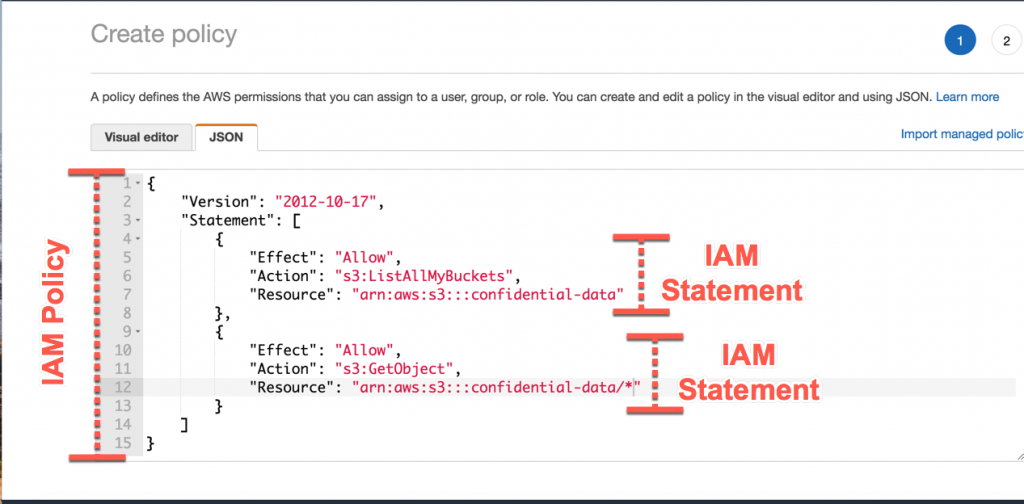
IAM tutorial: Create and attach your first customer managed policy - AWS Identity and Access Management

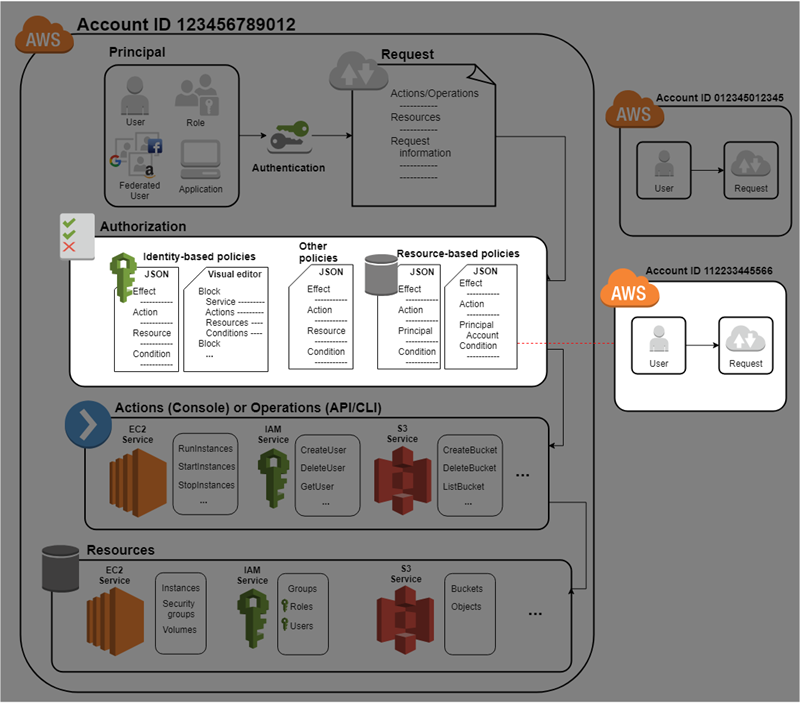
How to use resource-based policies in the AWS Secrets Manager console to securely access secrets across AWS accounts | AWS Security Blog