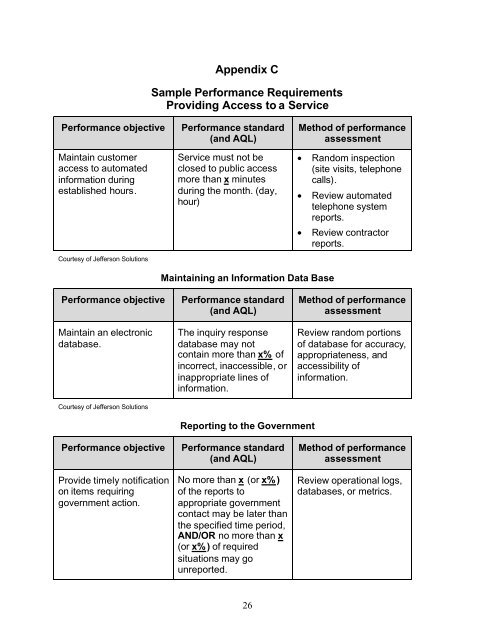
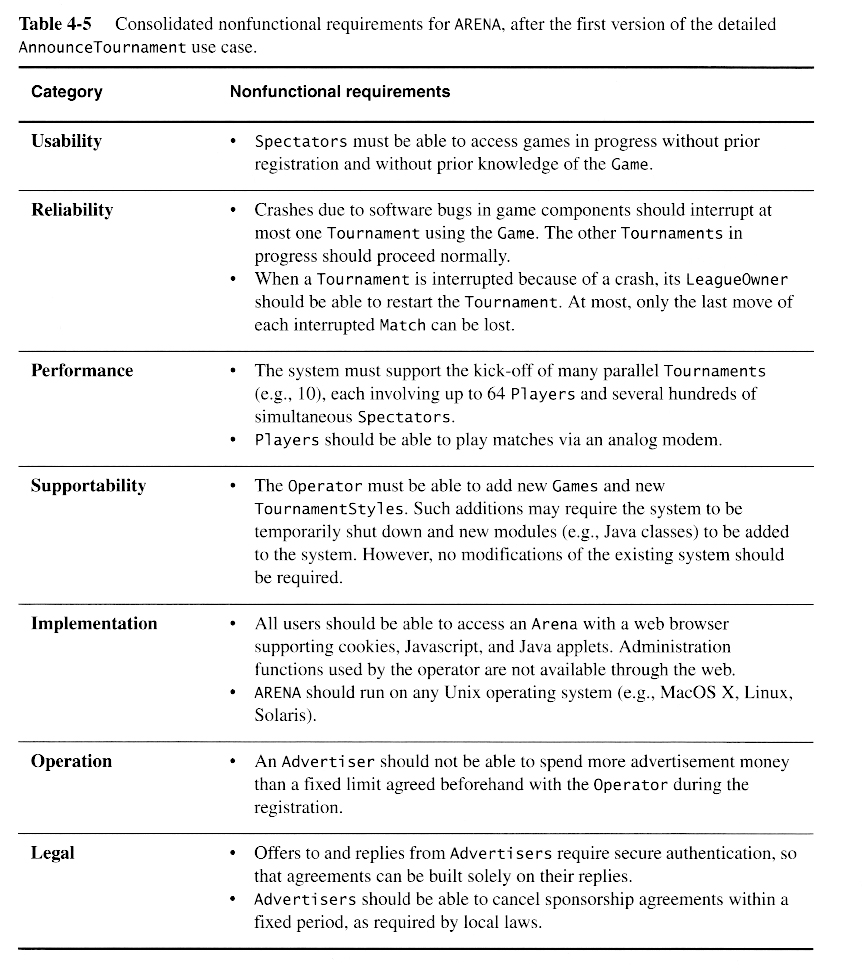
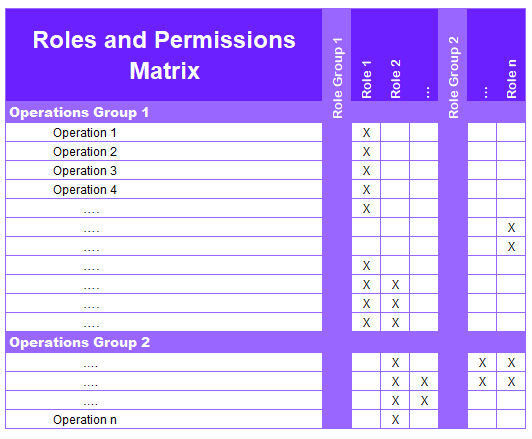
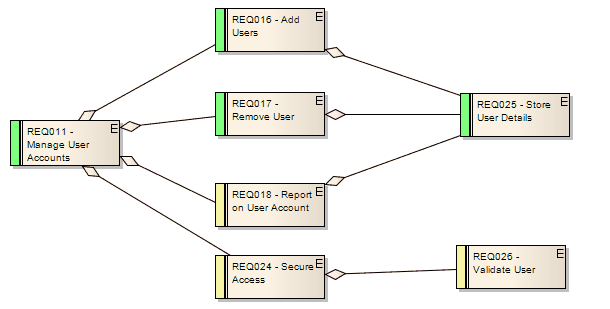
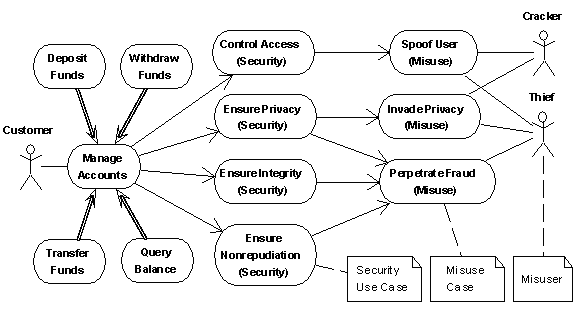
Simple Project – Requirements Ms-Access Database for tracking requirements | Custom Designed Databases

Access requirements of Example 6 using (a) GT RBAC s 1;A representation... | Download Scientific Diagram

Appendix D - Matrix of Additional Examples of Local Access Management Ordinances | Incorporating Roadway Access Management into Local Ordinances | The National Academies Press

Access requirements of Example 4 using (a) GT RBAC 1;U representation,... | Download Scientific Diagram







![Summary of how the example application addresses security requirements [6] | Download Table Summary of how the example application addresses security requirements [6] | Download Table](https://www.researchgate.net/publication/266388792/figure/tbl1/AS:392234483634192@1470527396583/Summary-of-how-the-example-application-addresses-security-requirements-6.png)