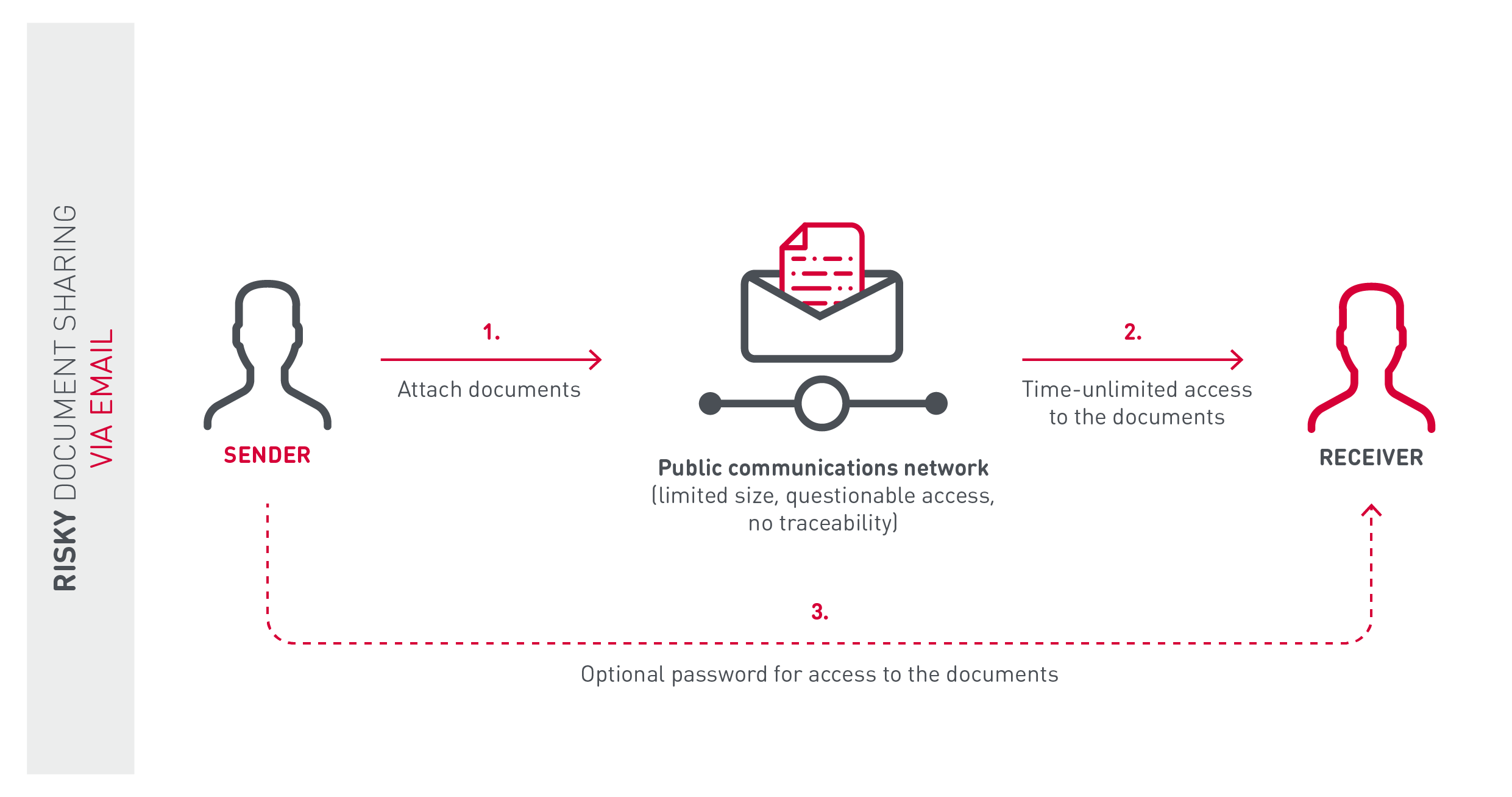
Why Respect Privacy and Confidentiality? Access to Confidential Information (OP ) Protection and Security of Protected Health Information (OP. - ppt download

Businessman collects wooden puzzles with the word Data Protection. Denied access to confidential information. Ensuring the confidentiality of personal Stock Photo - Alamy
Identifying and protecting users' confidential data - Documentation for BMC Helix Business Workflows 20.08 - BMC Documentation

.png)