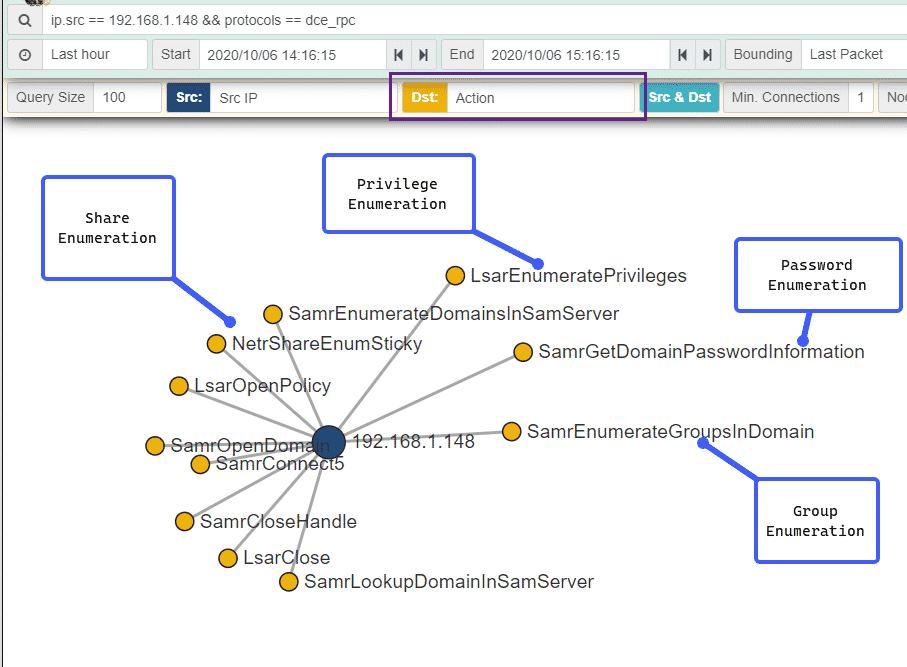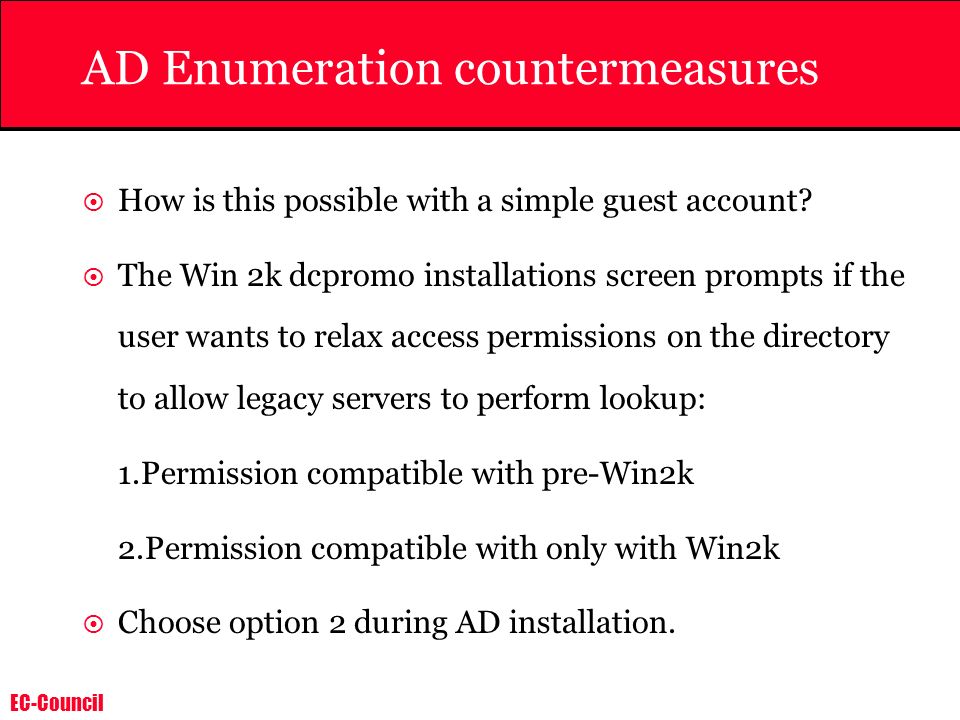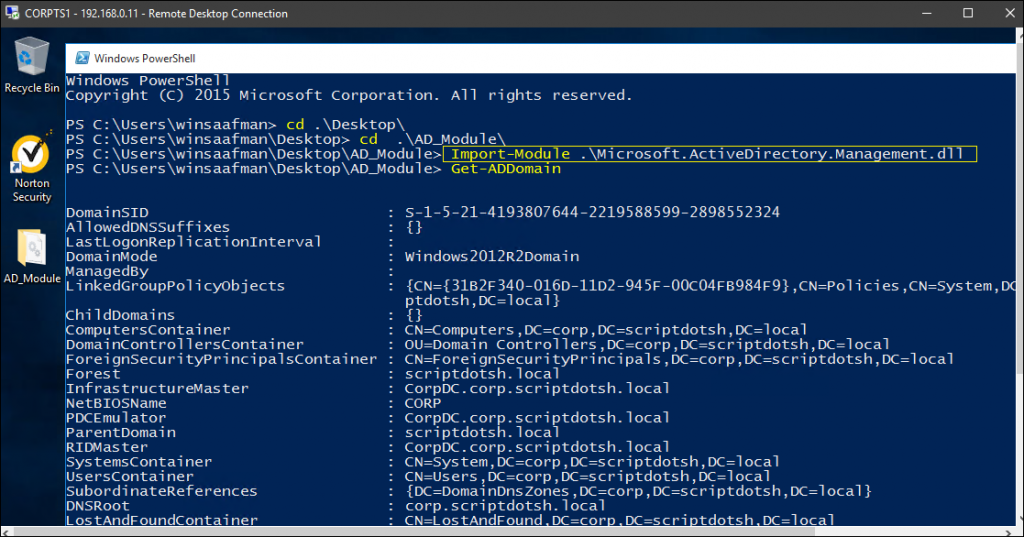
Offensive WMI - Active Directory Enumeration (Part 5) :: 0xInfection's Blog — Ramblings of an Infected Geek.

Automating AD Enumeration. Doing everything manually is cool, but… | by Mohit Panwar | InfoSec Write-ups

Attivo Networks ADSecure-DC solution identifies enumeration and attacks targeting Active Directory - Help Net Security