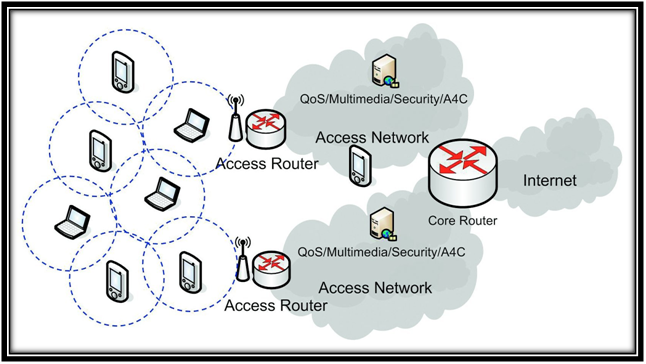
Adapted stream region for packet marking based on DDoS attack detection in vehicular ad hoc networks | The Journal of Supercomputing

PDF) A Survey of Attacks in Mobile Ad Hoc Network | IJIRST - International Journal for Innovative Research in Science and Technology - Academia.edu

Packet dropping attack in Mobile Ad-hoc Networks von Ramandeep Kaur | ISBN 978-3-659-61271-8 | Buch online kaufen -

Symmetry | Free Full-Text | Man-in-the-Middle Attacks in Mobile Ad Hoc Networks (MANETs): Analysis and Evaluation

Analysis of Black hole Attack in Ad hoc On-Demand Distance Vector (AODV) Routing Protocol : Vehicular Ad-hoc Networks (VANET) Context - CORE

The Human Rights Defender of Armenia published the updated Ad Hoc Public Report on consequences of Azerbaijani military attack on the Republic of Armenia. A special closed report was also developed ,
![PDF] Detection and Prevention of Black Hole Attack in Mobile Ad-Hoc Networks: A Survey | Semantic Scholar PDF] Detection and Prevention of Black Hole Attack in Mobile Ad-Hoc Networks: A Survey | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d1e67c8f5080855bb673227755afa33de06e1465/2-Figure2.2-1.png)
PDF] Detection and Prevention of Black Hole Attack in Mobile Ad-Hoc Networks: A Survey | Semantic Scholar

Secure routing in wireless mobile Ad-Hoc network von Govind Sharma und Manish Gupta | ISBN 978-3-659-13705-1 | Buch online kaufen -

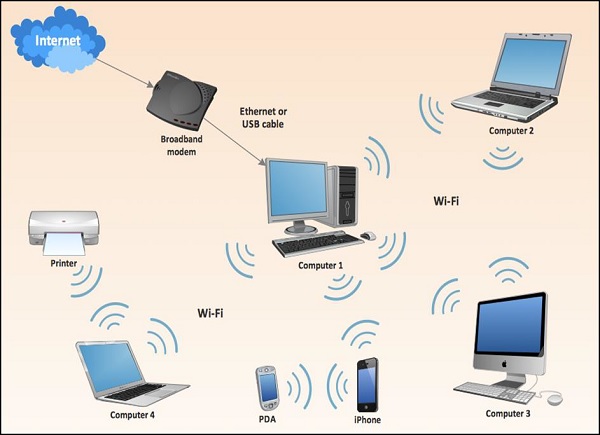





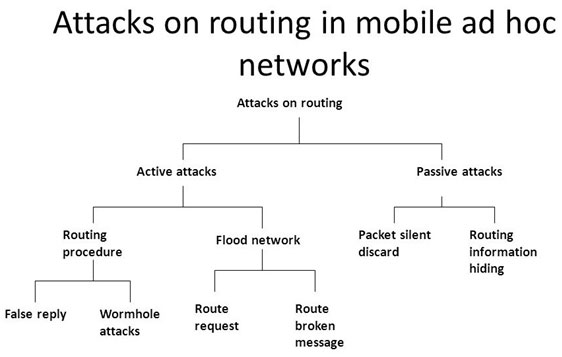





![PDF] Different types of attacks in Mobile ADHOC Network | Semantic Scholar PDF] Different types of attacks in Mobile ADHOC Network | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1c4a1bd9ba77d0198c0c94a446d8705725255741/2-Figure1-1.png)