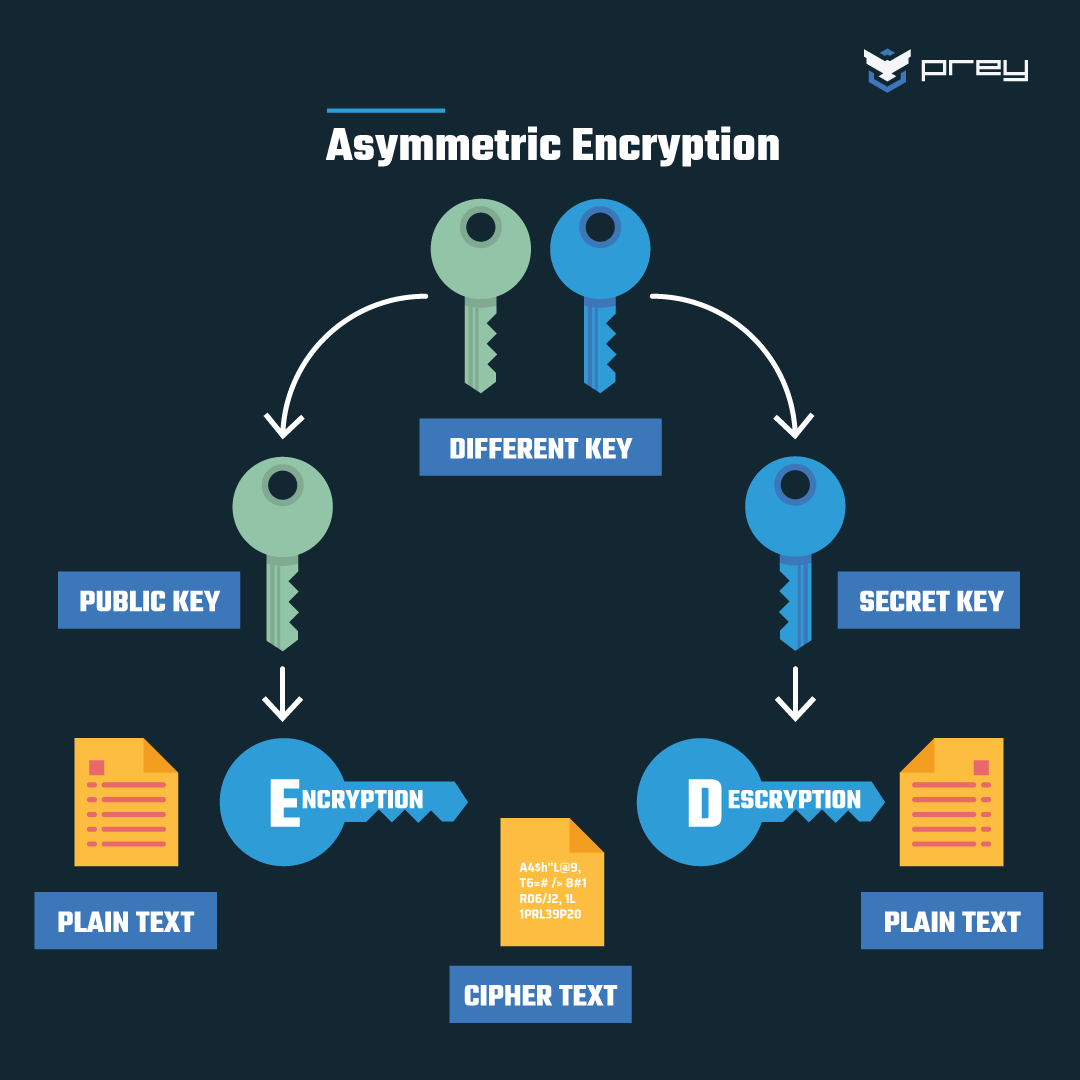
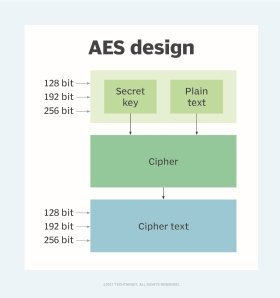
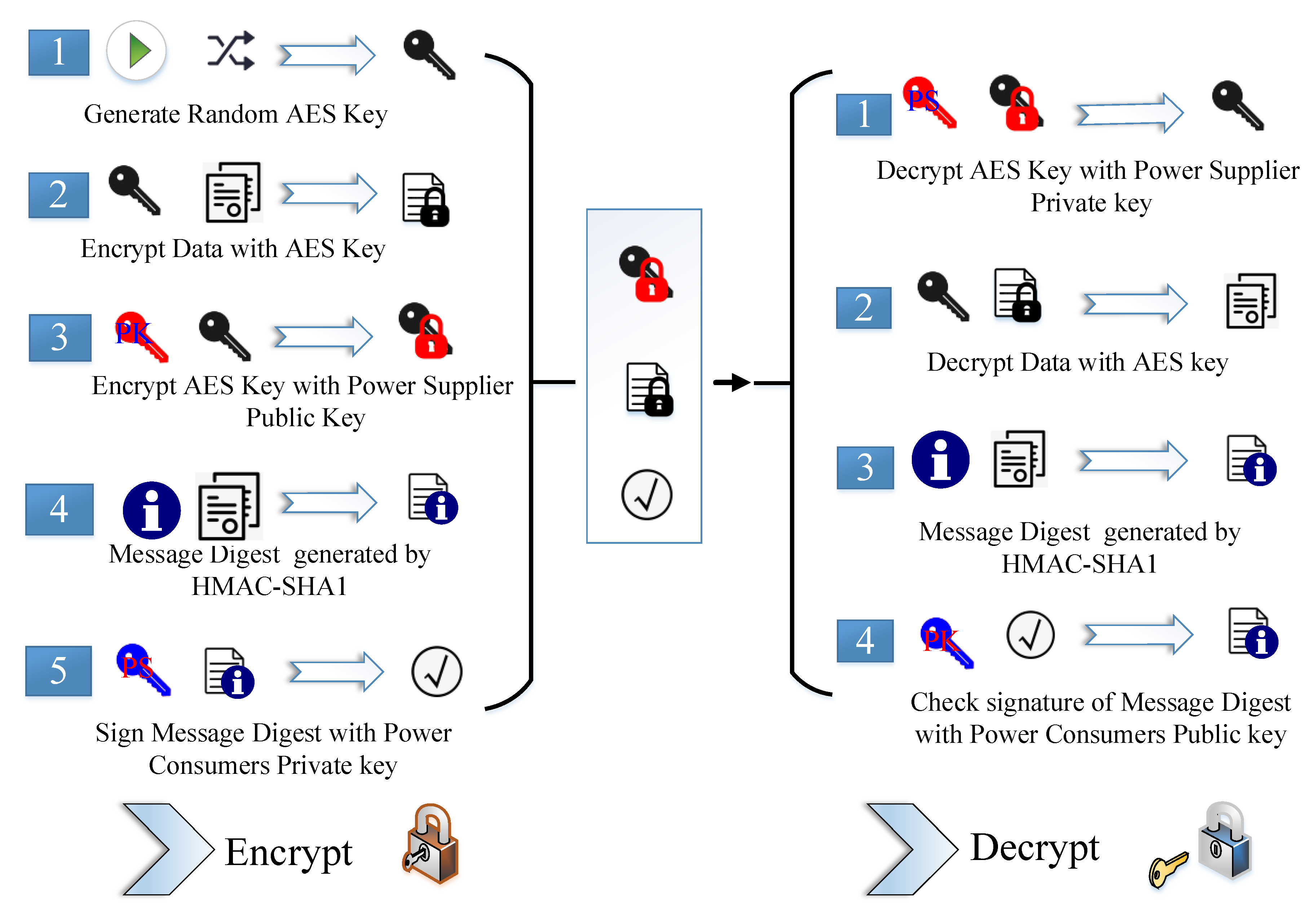
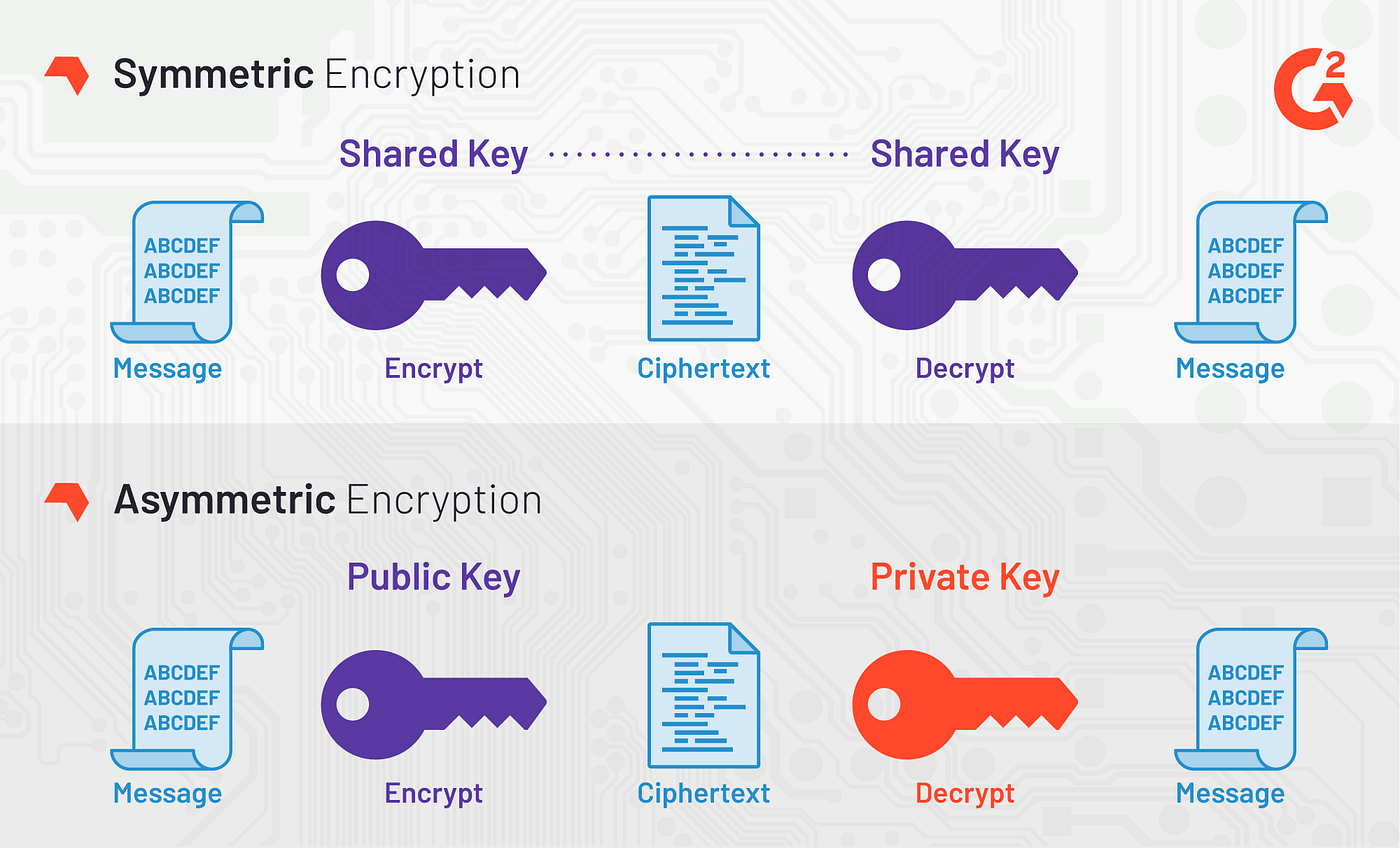
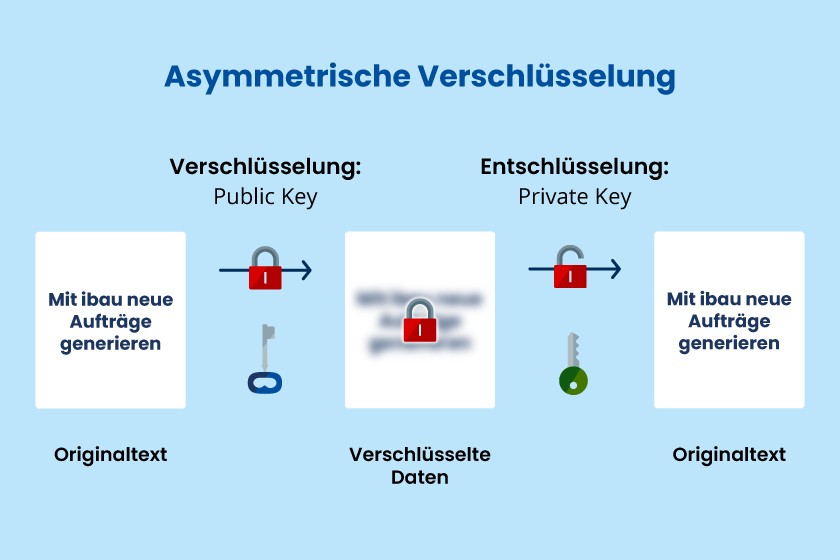
Encrypted client-server communication (protection of privacy and integrity with AES and RSA in details) | by Weblab Technology | WebLab Technology — A company blog

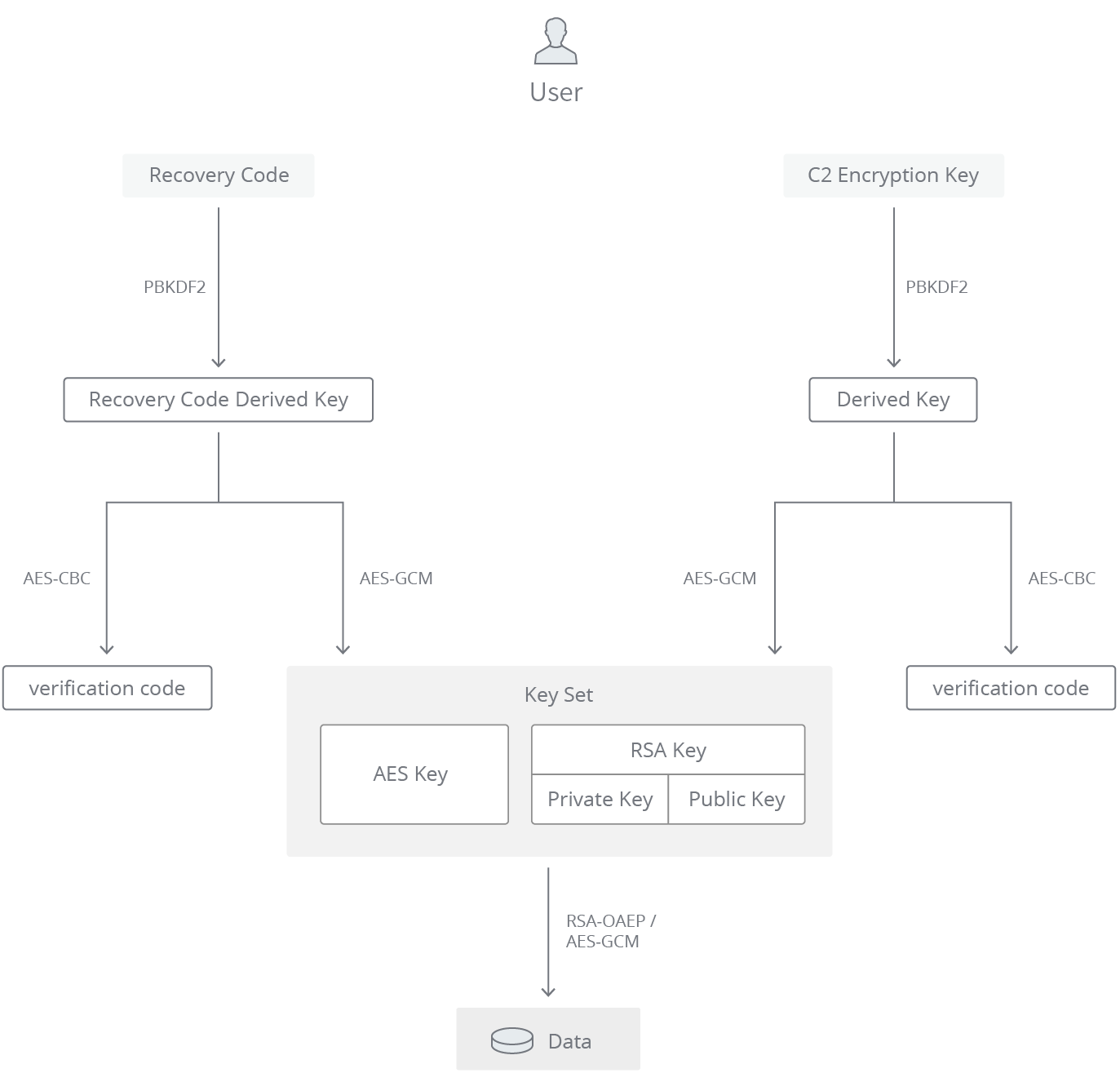
Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)