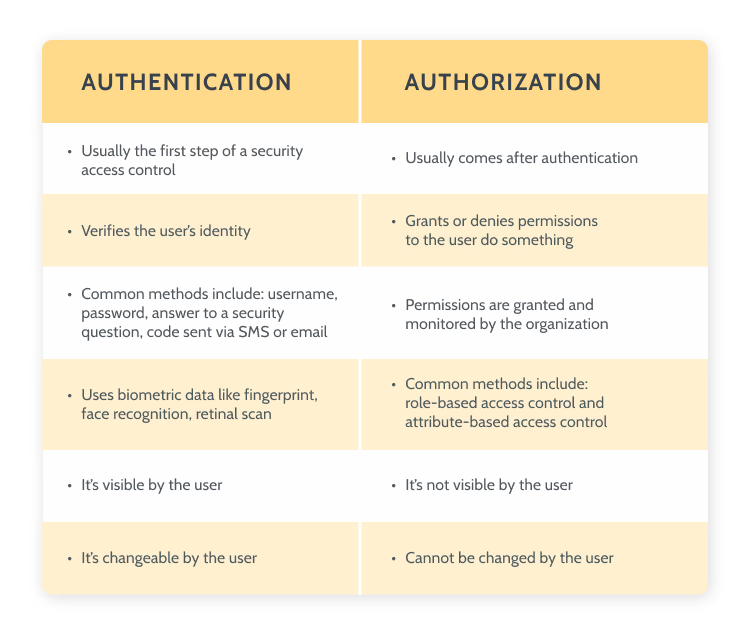
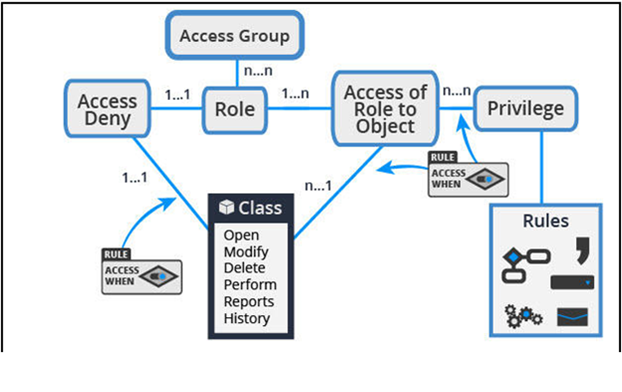
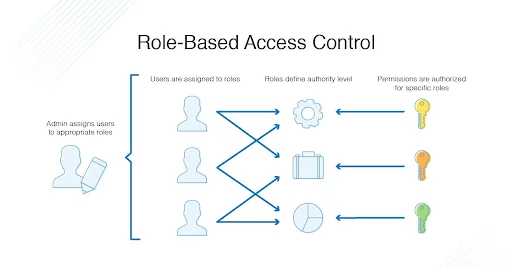
Authentication vs. Access Controls vs. Authorization | by CloudKnox Security Inc. | CloudKnox Security Inc. | Medium
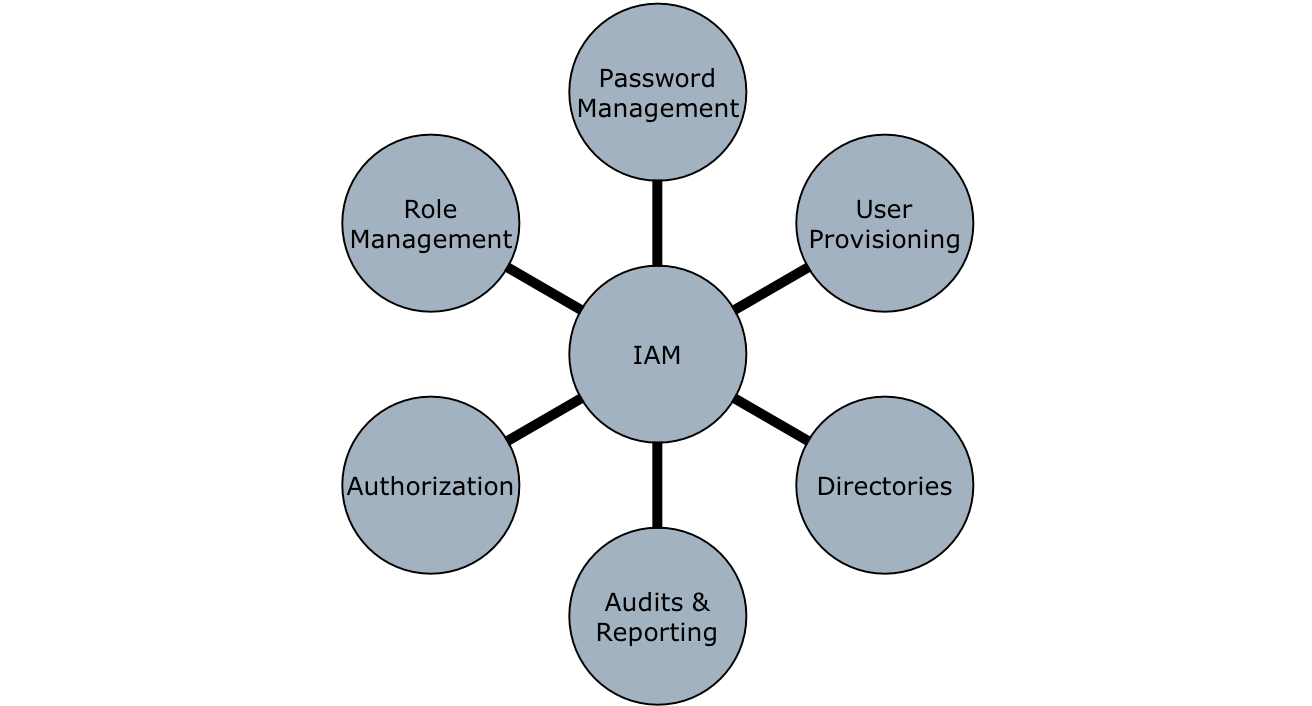
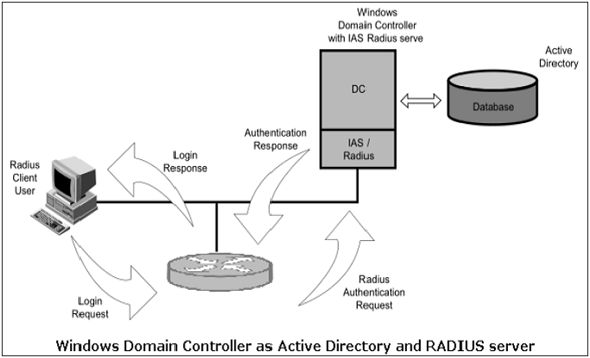
3 Basic A's of Identity and Access Management -Authentication, Authorization, and Accounting – Xorlogics

Understanding Identification, Authentication, and Authorization in Security | #informationsecurity - YouTube

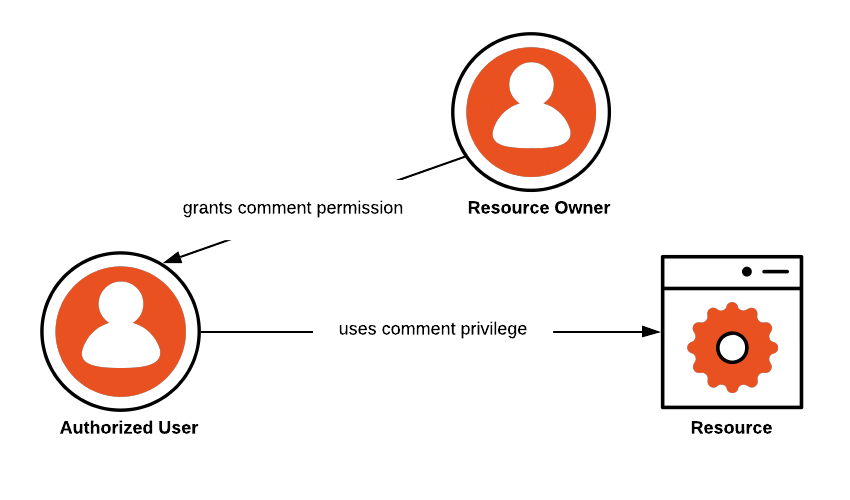
![User authorization | Elasticsearch Guide [8.12] | Elastic User authorization | Elasticsearch Guide [8.12] | Elastic](https://www.elastic.co/guide/en/elasticsearch/reference/current/security/authorization/images/authorization.png)



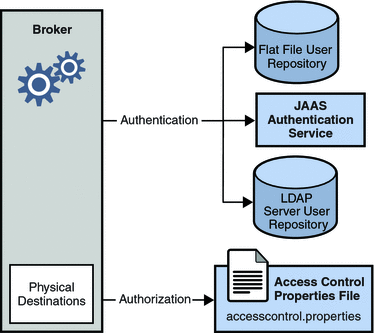

![Access Control Process - Access Control and Identity Management, 3rd Edition [Book] Access Control Process - Access Control and Identity Management, 3rd Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781284198362/files/images/9781284198355_CH01_FIGF01.png)