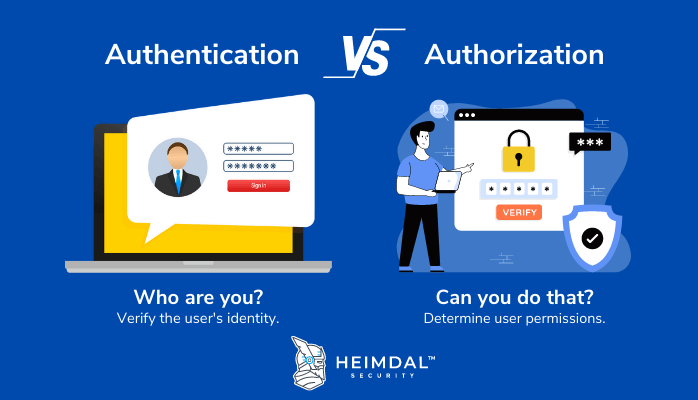
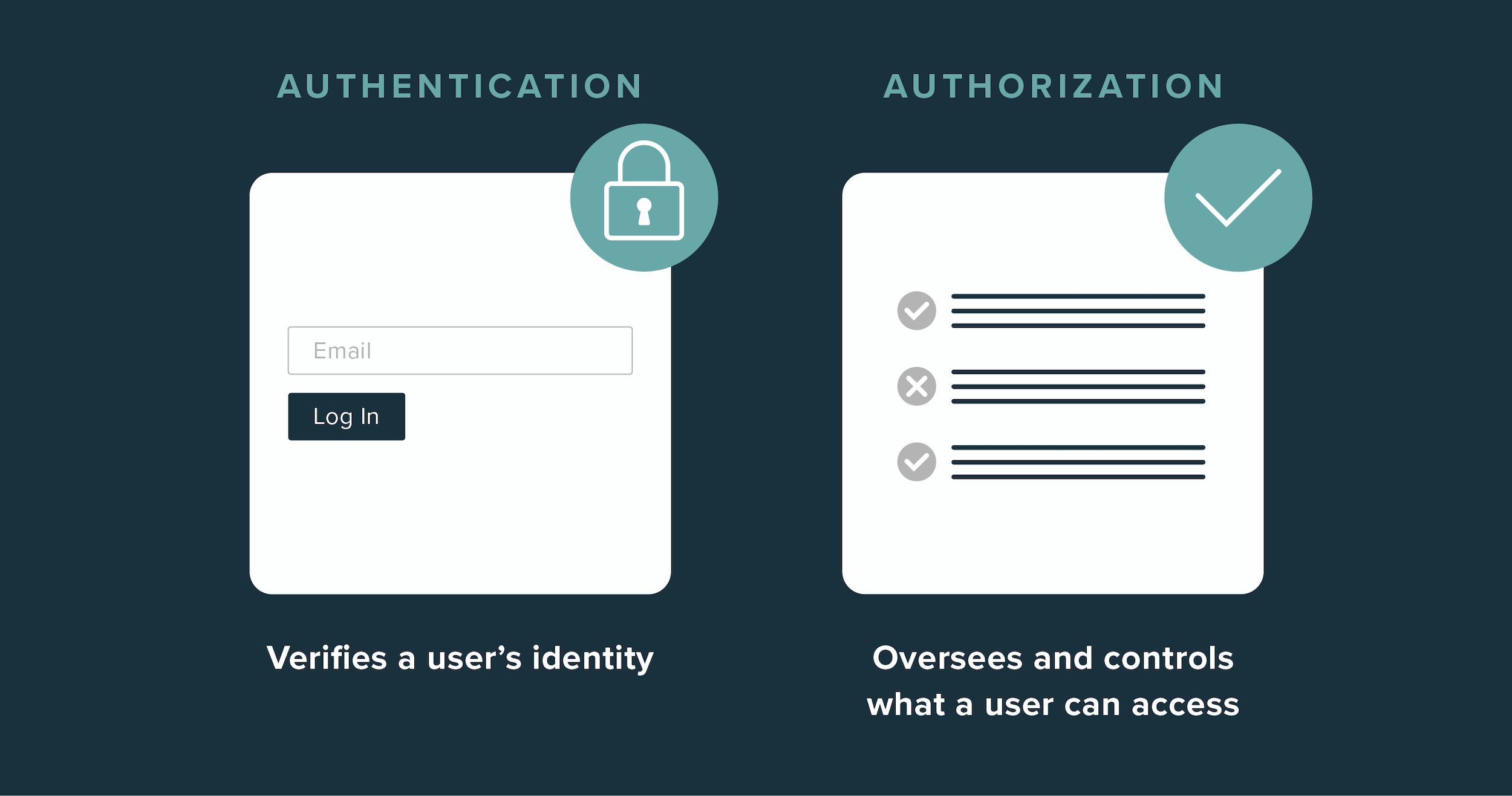
Understanding Identification, Authentication, and Authorization in Security | #informationsecurity - YouTube
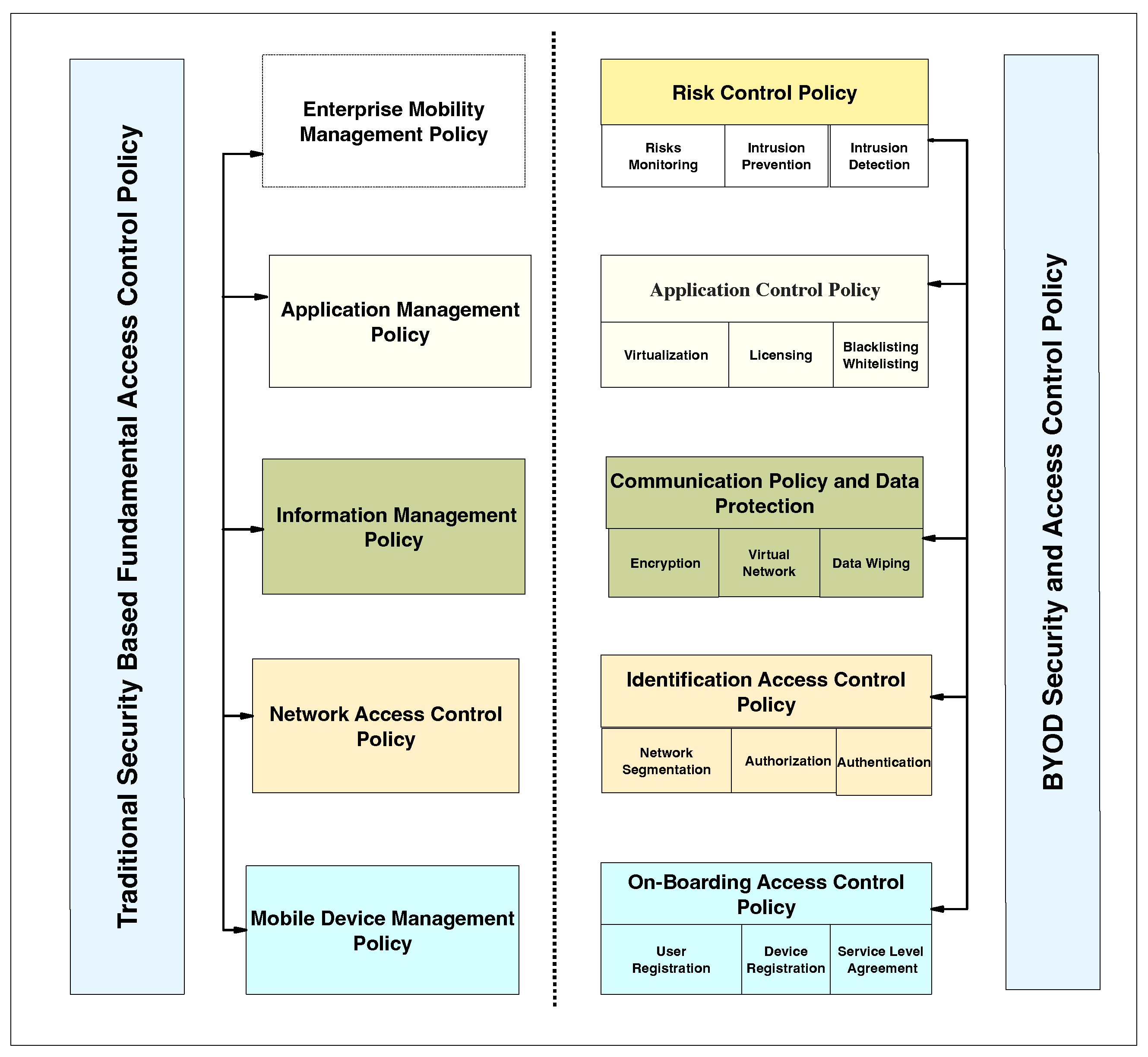
Applied Sciences | Free Full-Text | Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions
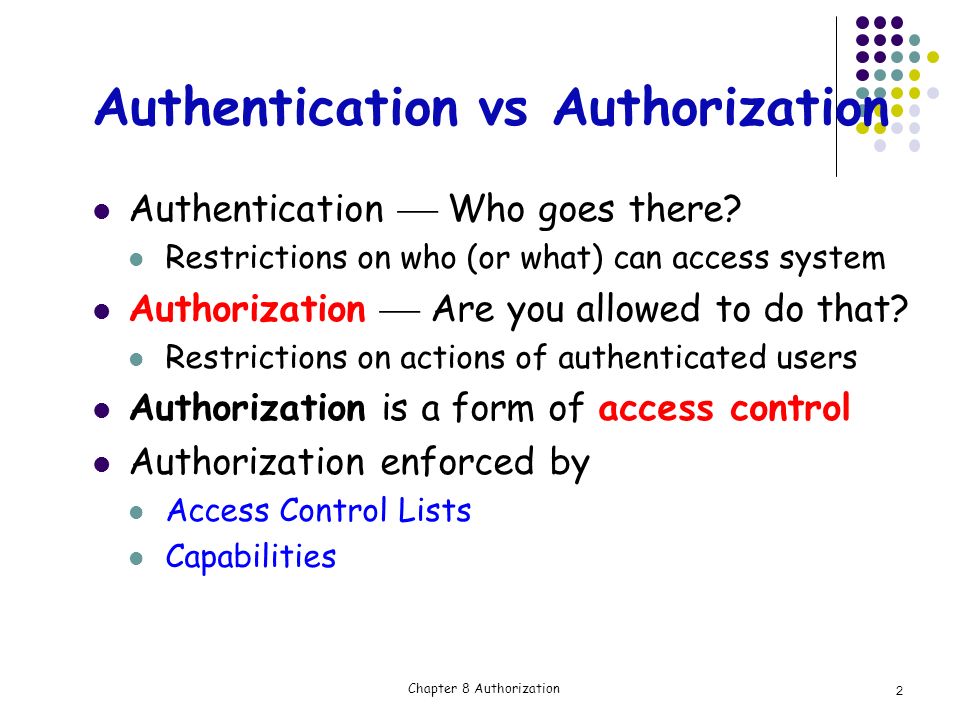
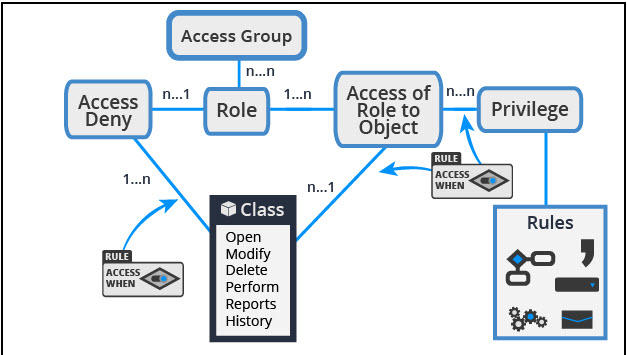
Chapter 8 Authorization Access control matrix Multilevel Security Multilateral security Covert channel Inference control CAPTCHA Firewalls IDS. - ppt download

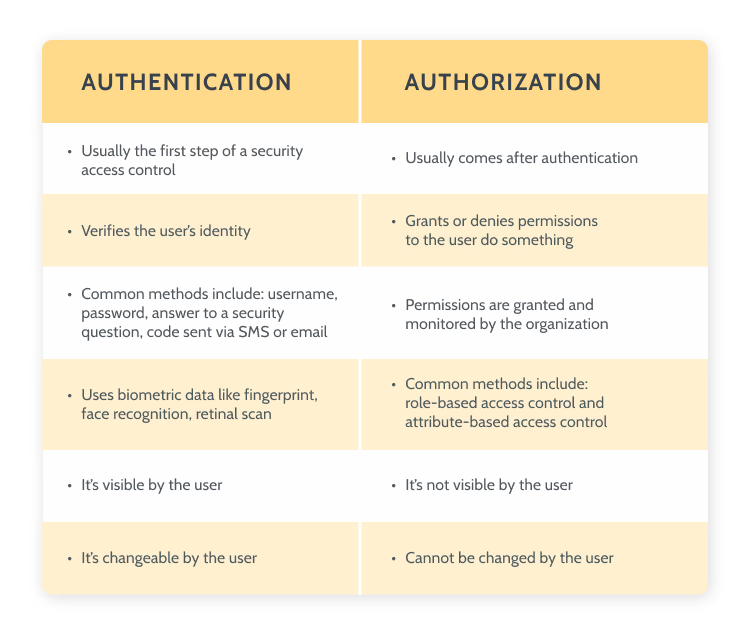


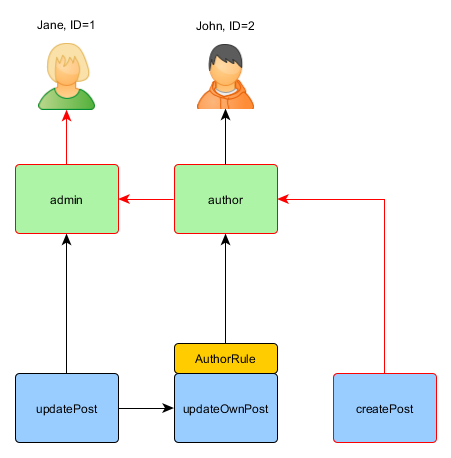
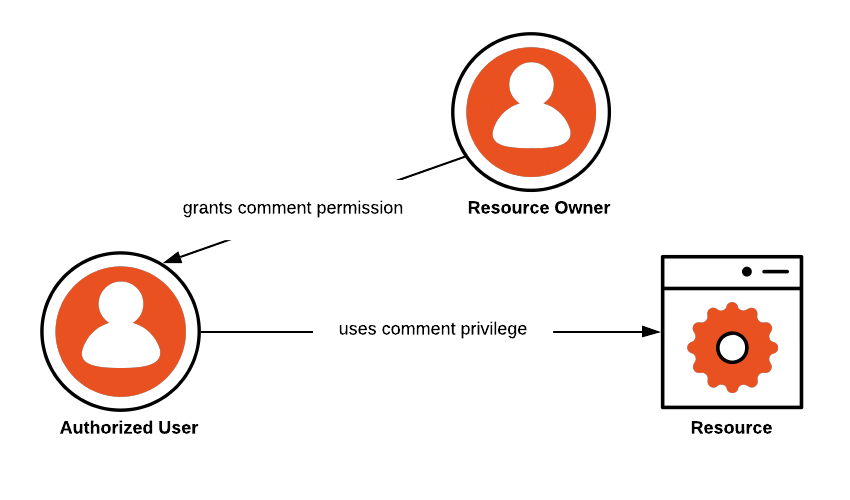
![User authorization | Elasticsearch Guide [8.12] | Elastic User authorization | Elasticsearch Guide [8.12] | Elastic](https://www.elastic.co/guide/en/elasticsearch/reference/current/security/authorization/images/authorization.png)