Brendan Tully on Twitter: "Solving dem root causes of Amazon AWS abuse reports like a bawse https://t.co/pgcf6adcP8" / Twitter

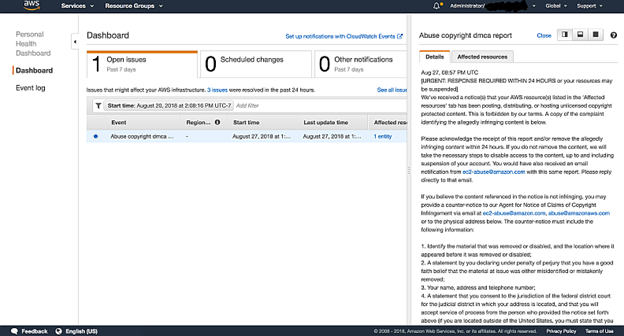
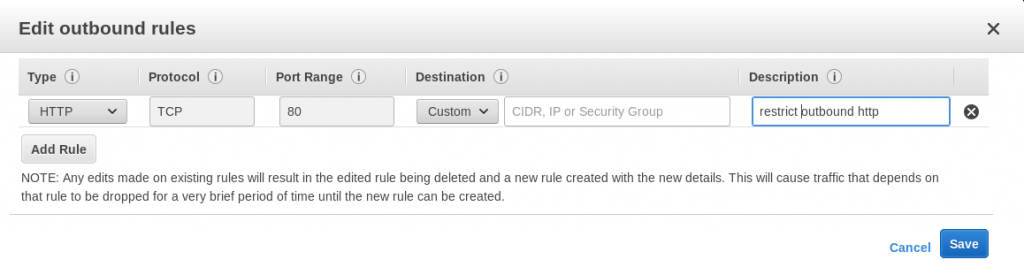
Incident Response in the Cloud (AWS)Part 1- Handling AWS Abuse Notifications | by Avik Chowdhury | Medium

Smartypants.com on Twitter: "Been receiving the latest batch of #jpmonfort "fiction states"/"DEFENSE MECHANISM" spam? You can thank @Issuu and Amazon @ AWS for facilitating that, by ignoring abuse complaints and knowingly continuing to