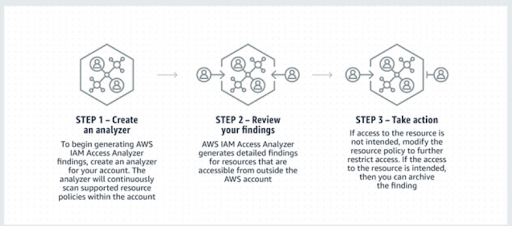
AWS IAM Access Analyzer: 101. Continuous Access monitoring to AWS… | by Vikas | AWS in Plain English

How to use AWS IAM Access Analyzer API to automate detection of public access to AWS KMS keys | AWS Security Blog

Identify Unintended Resource Access with AWS Identity and Access Management (IAM) Access Analyzer | AWS News Blog

IAM Access Analyzer flags unintended access to S3 buckets shared through access points | AWS Security Blog

Identify Unintended Resource Access with AWS Identity and Access Management (IAM) Access Analyzer | AWS News Blog

IAM Access Analyzer flags unintended access to S3 buckets shared through access points | AWS Security Blog

Identify Unintended Resource Access with AWS Identity and Access Management (IAM) Access Analyzer | AWS News Blog