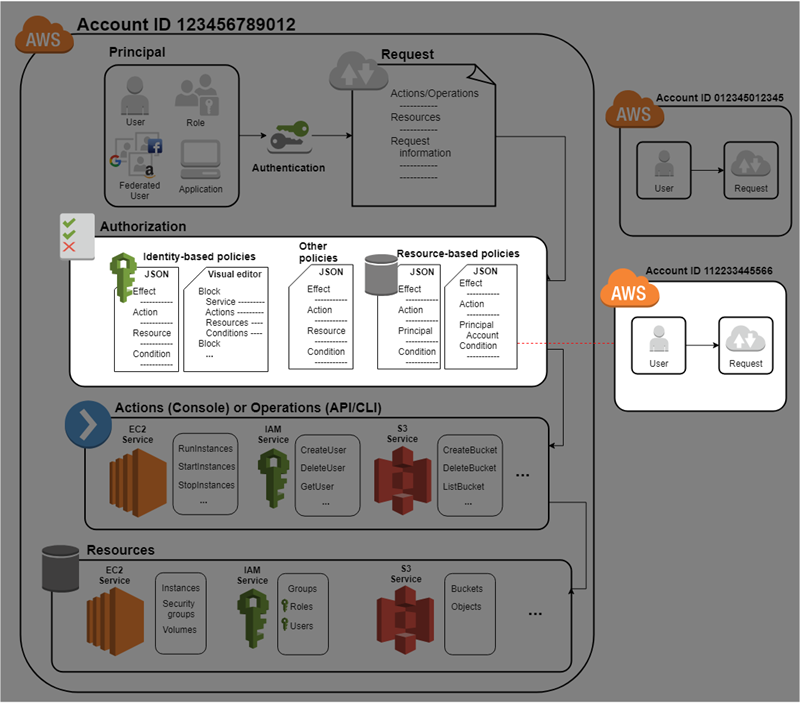
Increase visibility and governance on cloud with AWS Cloud Operations services – Part 1 | AWS Cloud Operations & Migrations Blog

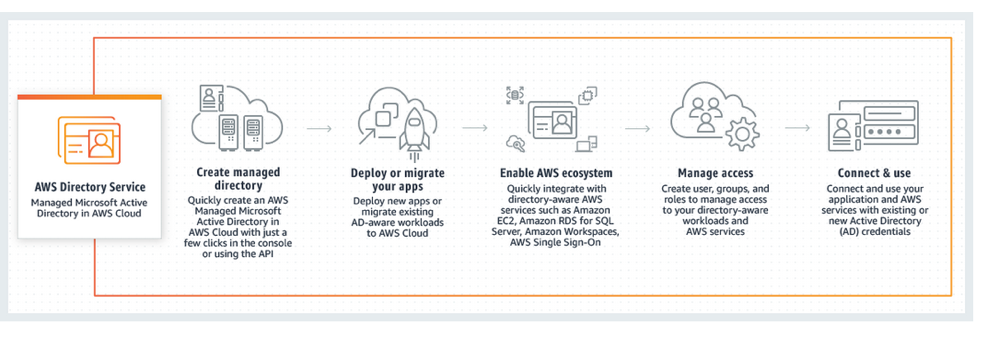
Übersicht – Anwenden von Zero Trust-Prinzipien auf IaaS-Anwendungen in Amazon Web Services (AWS) | Microsoft Learn

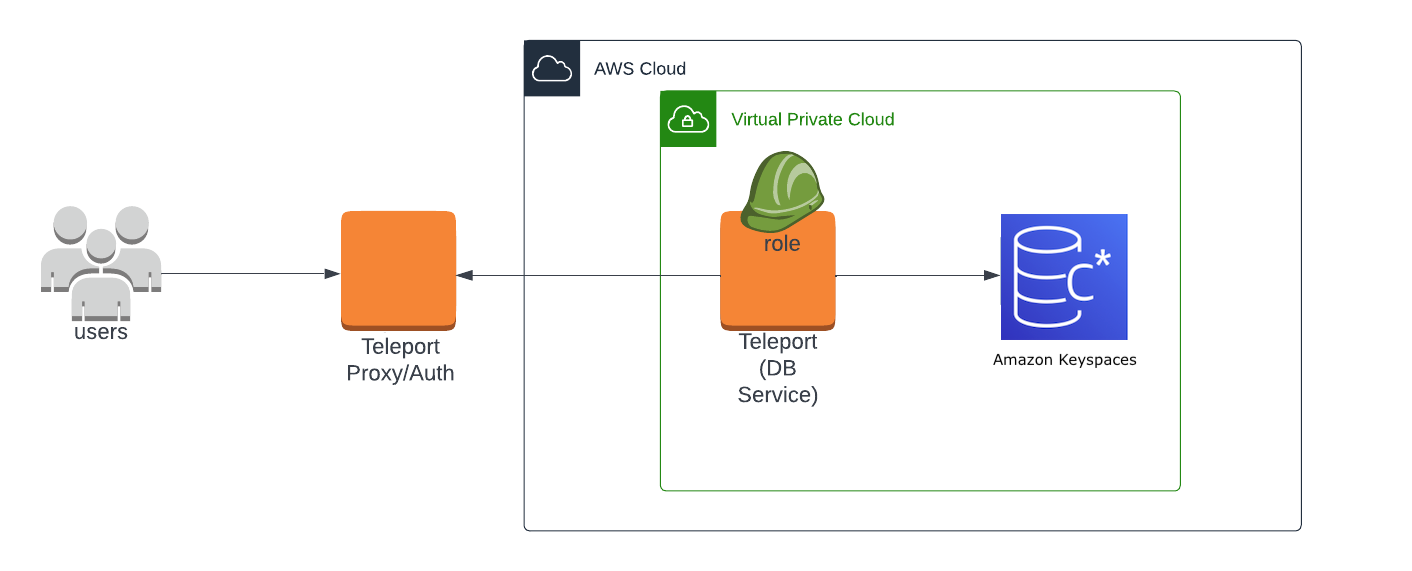
How to Access the AWS Management Console Using AWS Microsoft AD and Your On-Premises Credentials | AWS Security Blog