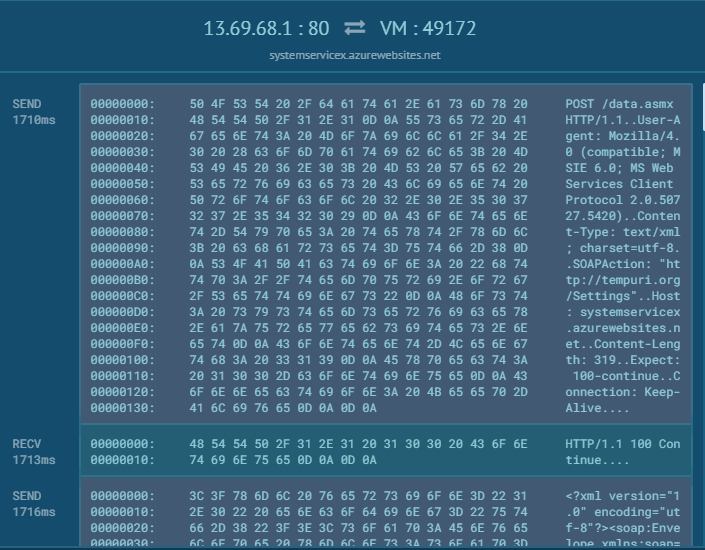
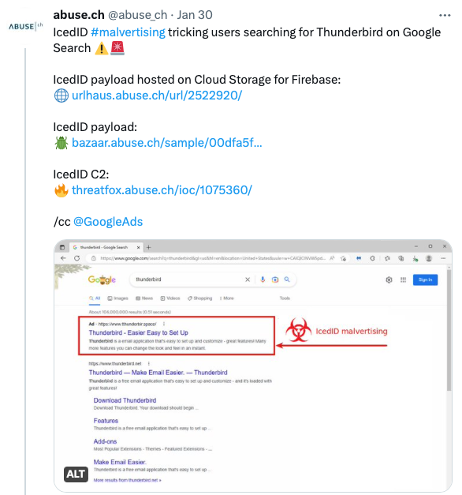
abuse.ch on X: "Fresh, active Emotet botnet C2 servers are now being pushed to Feodo Tracker 💪🛡️ 👉 https://t.co/TvIJyqHYVs We urge you to *BLOCK* these C2 servers and regularly update your block

Full article: The Relationship Between Childhood Abuse and Adult Attachment Styles: The Mediator Role of Sensory Over-Responsivity
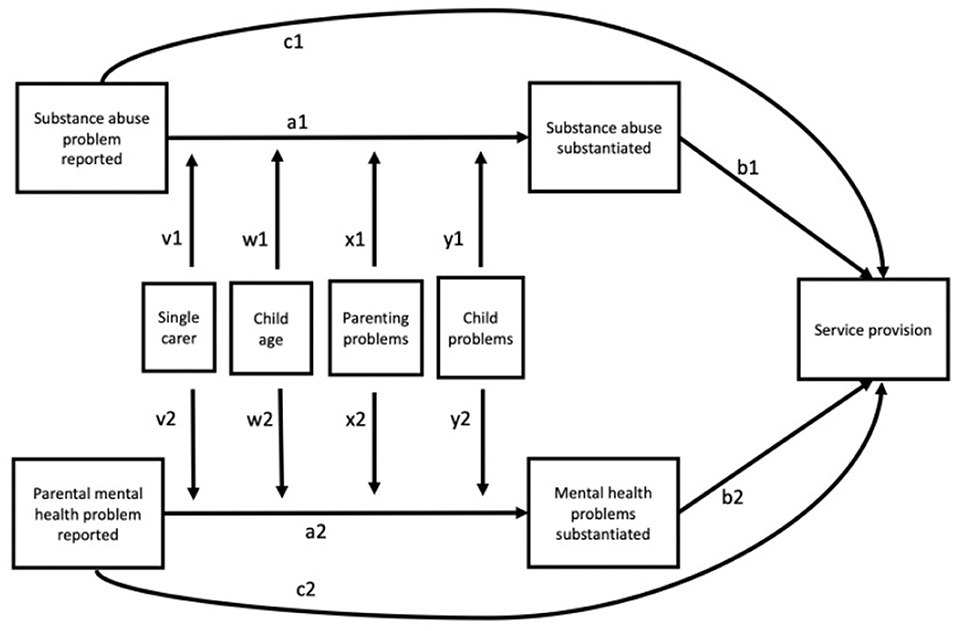
Frontiers | Concerns of Parental Substance Abuse and Mental Health Problems Reported to Child Welfare Services—Testing a Moderated Mediation Model for Paths From Reports to Substantiated Concern and Service Provision
Rate and severity of radiological features of physical abuse in children during the first UK-wide COVID-19 enforced national lockdown

The origin of maltreatment: An exploratory study on the intergenerational transmission of child abuse typologies
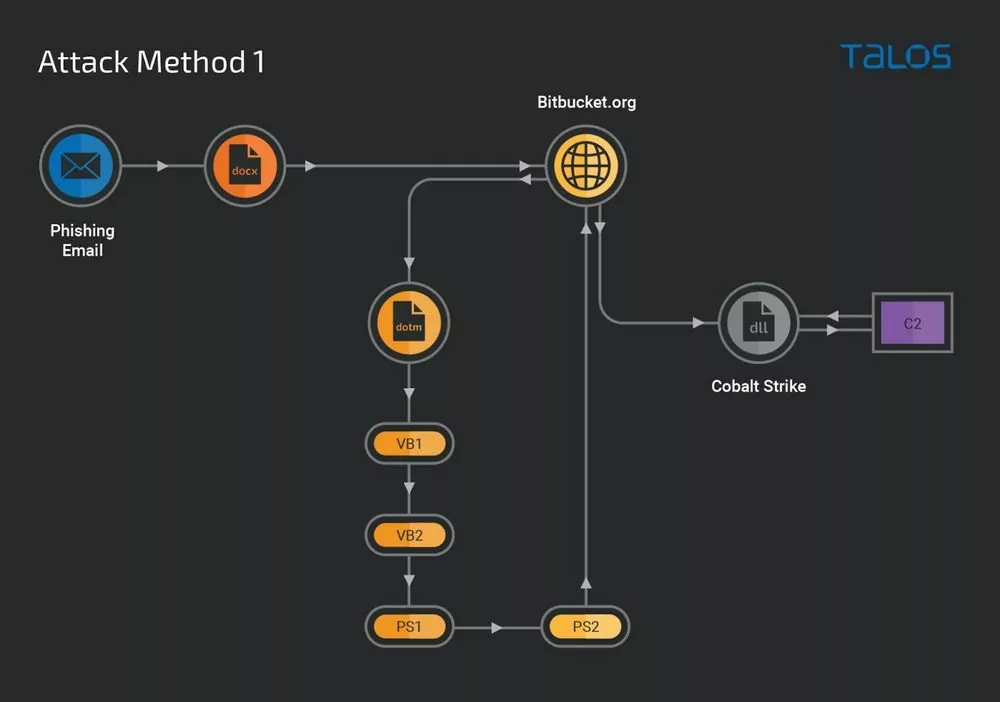
The Wolf in Sheep's Clothing: How Cybercriminals Abuse Legitimate Software - Malware News - Malware Analysis, News and Indicators