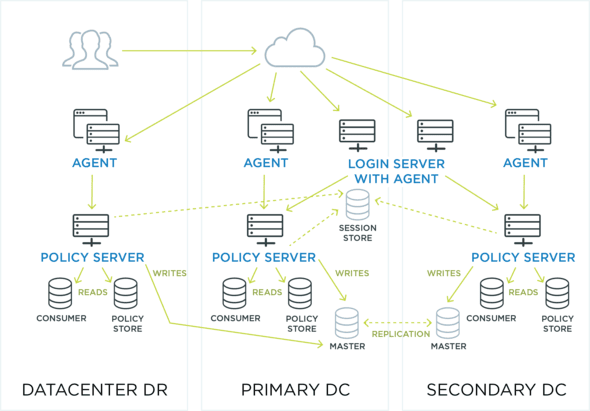
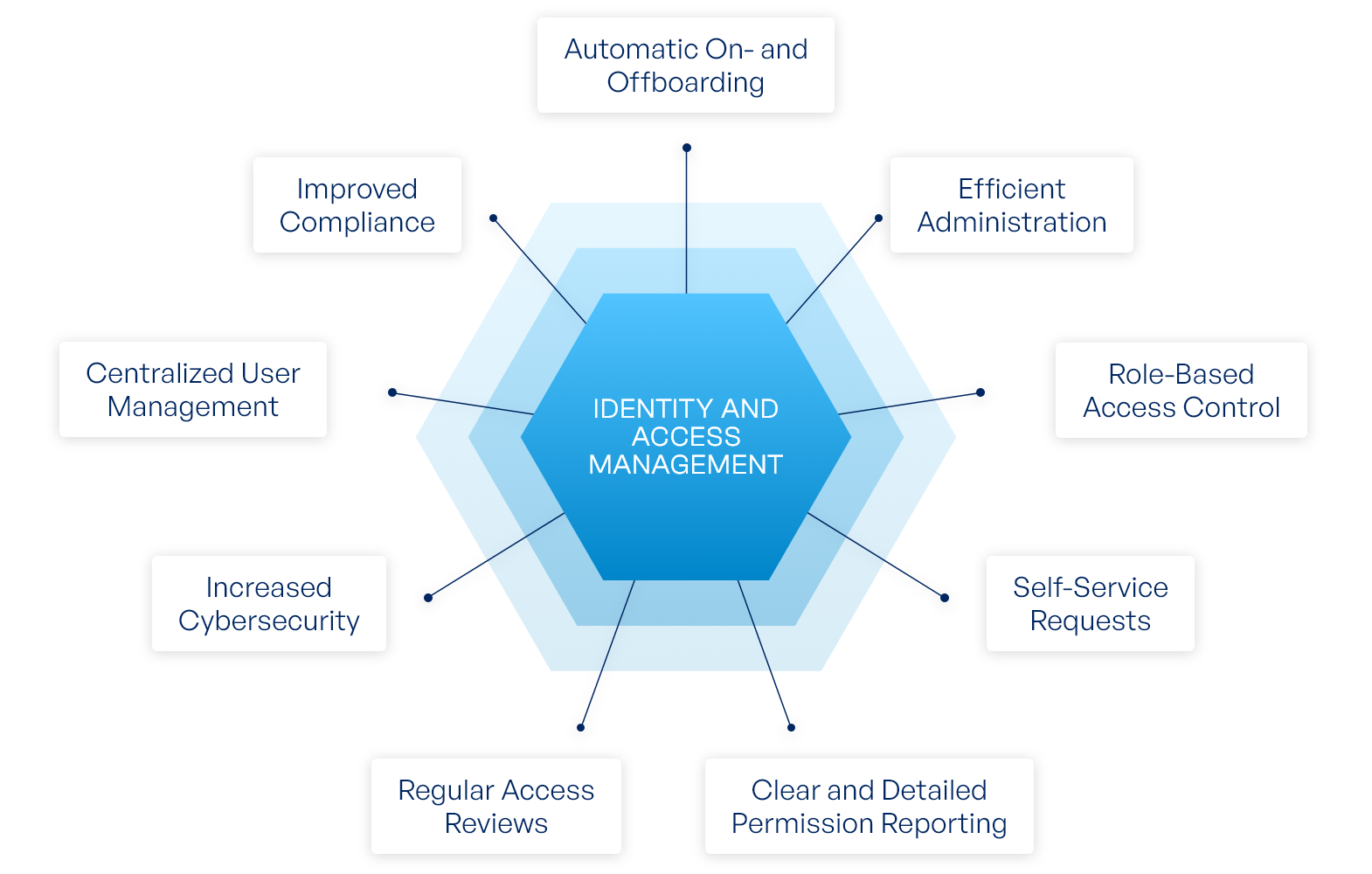
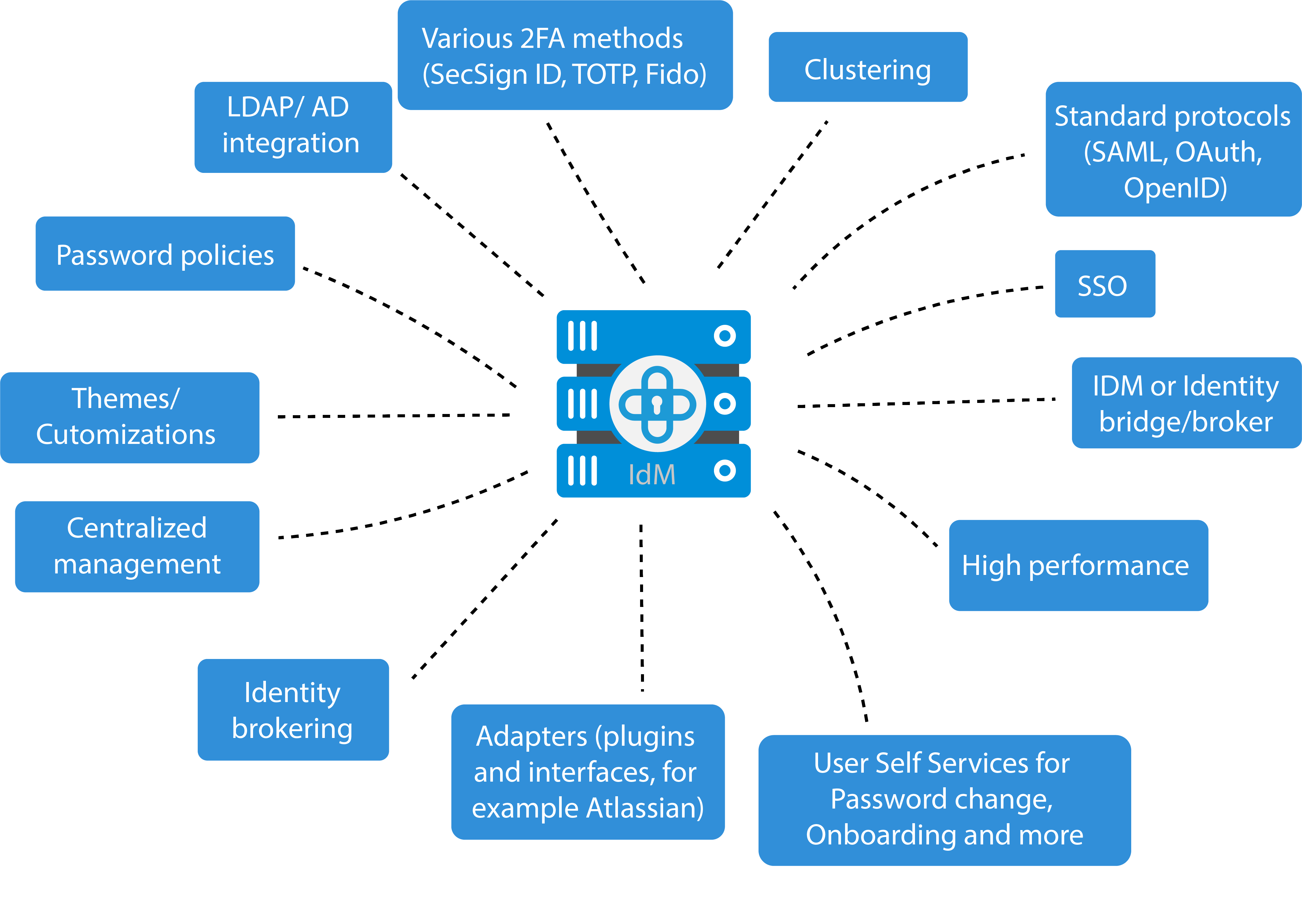
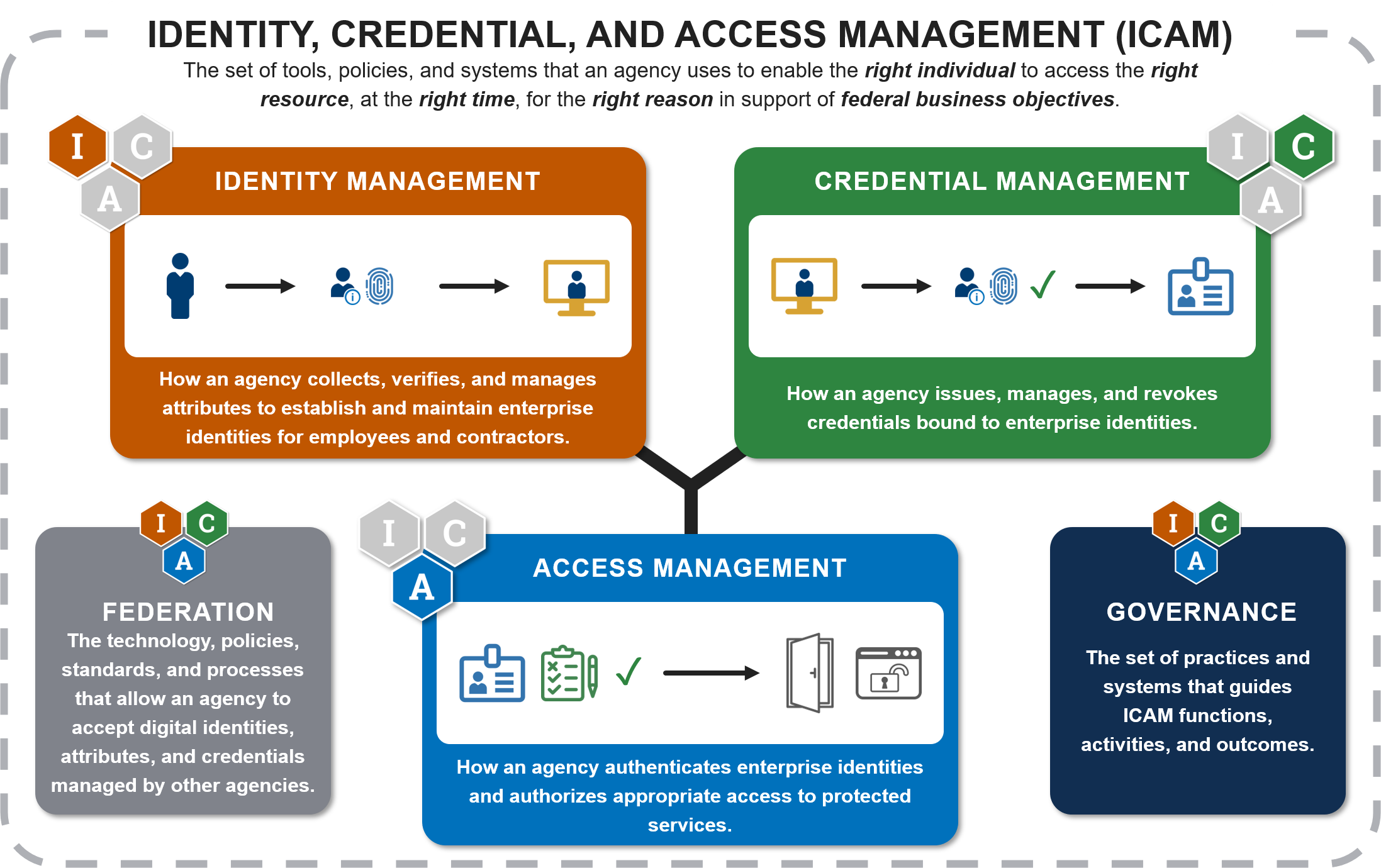
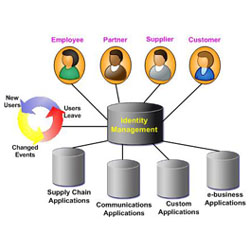
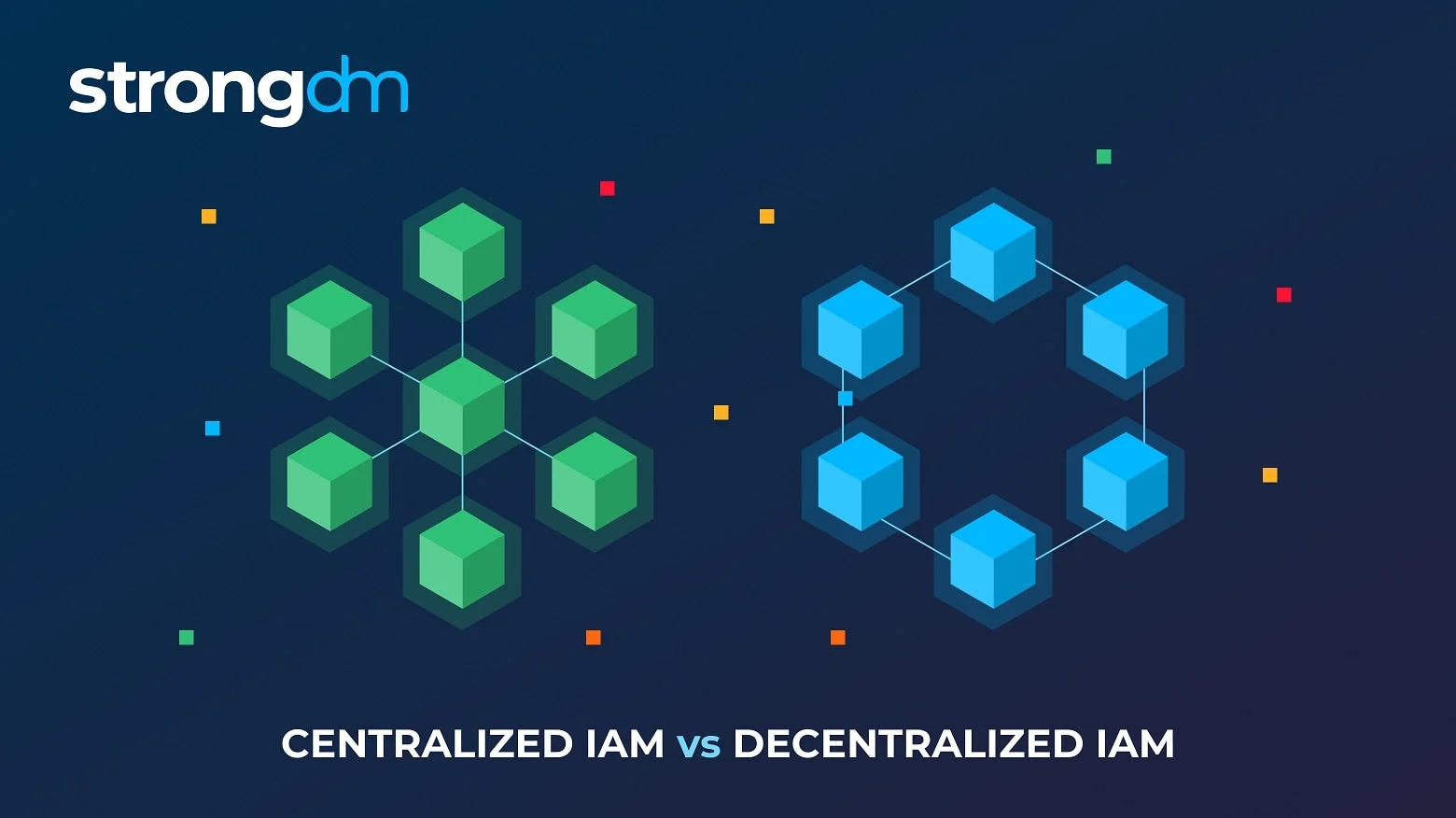
Access control approaches. (a) centralized model, (b) using Blockchain... | Download Scientific Diagram

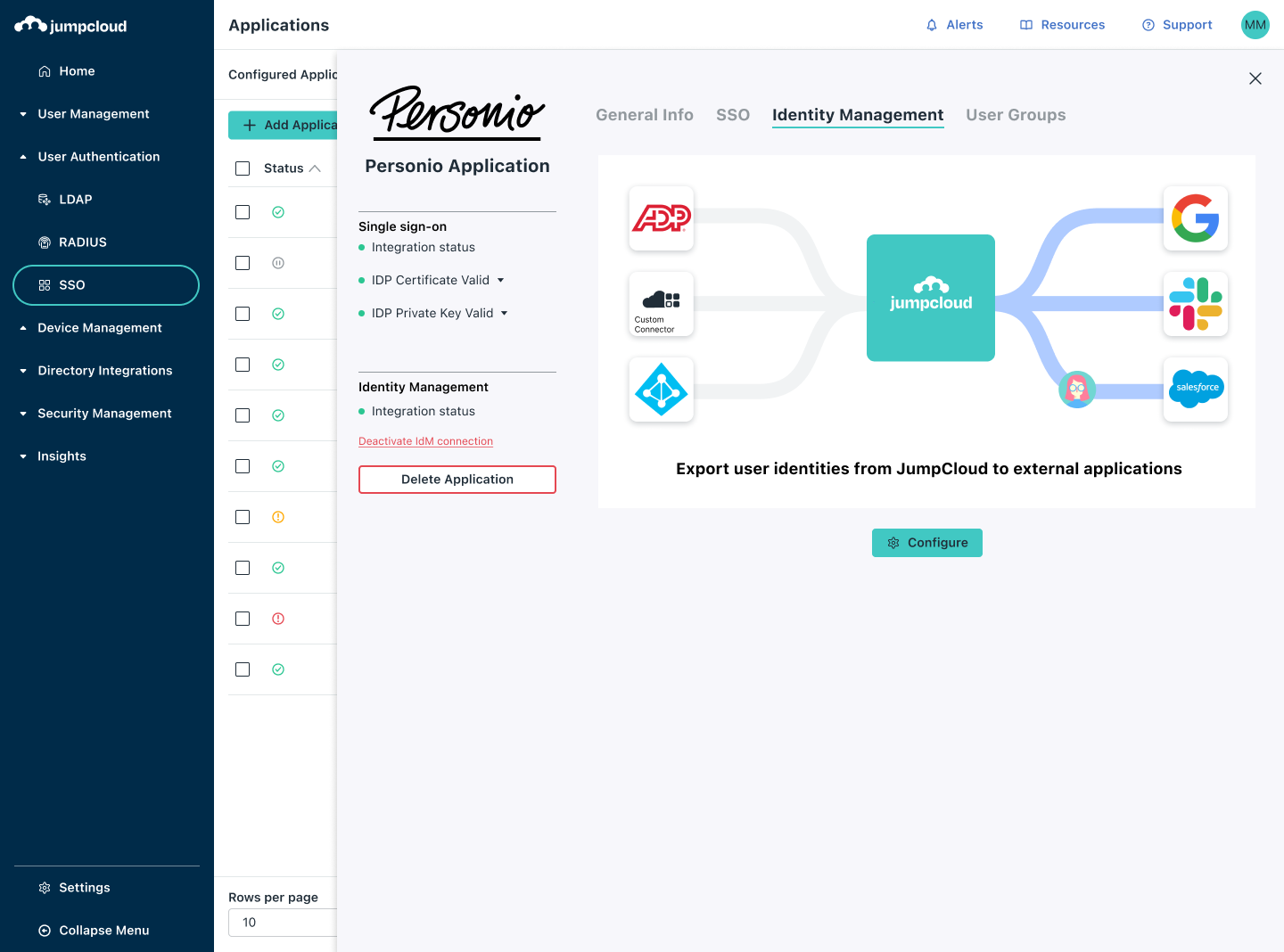
Centralized access control system with remote Management - KEYSAFE - OMNITEC SYSTEMS, S.L. - for hotel

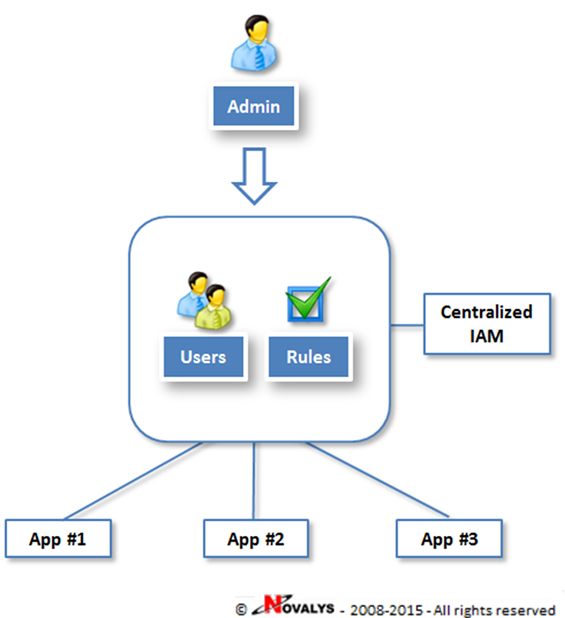
Explanation of implementing a system of centralized control of access. | Download Scientific Diagram
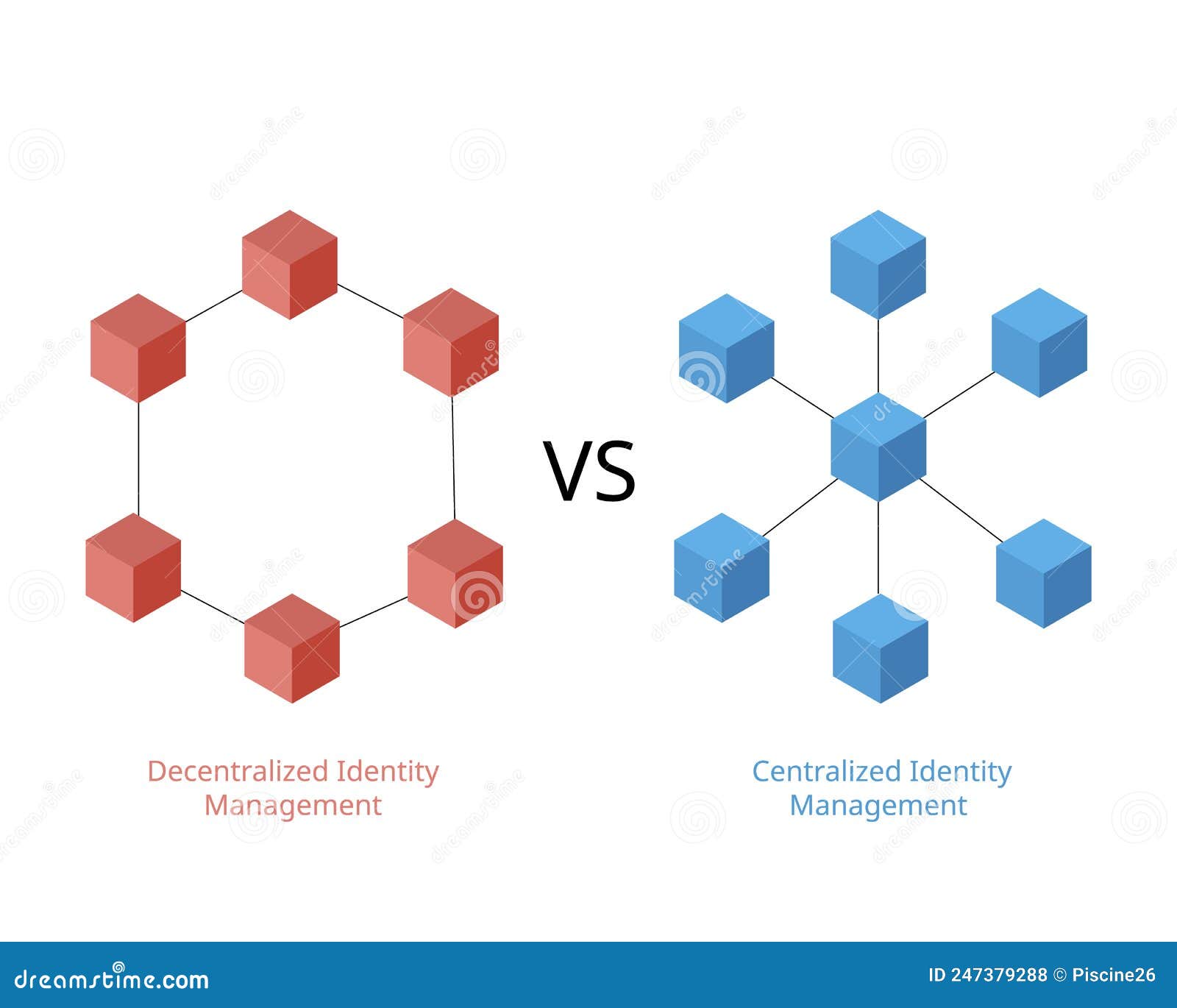
Centralized or Identity and Access Management and Decentralized Identity Management Stock Vector - Illustration of authentication, server: 247379288

Centralized or identity and access management and decentralized identity management 7742294 Vector Art at Vecteezy
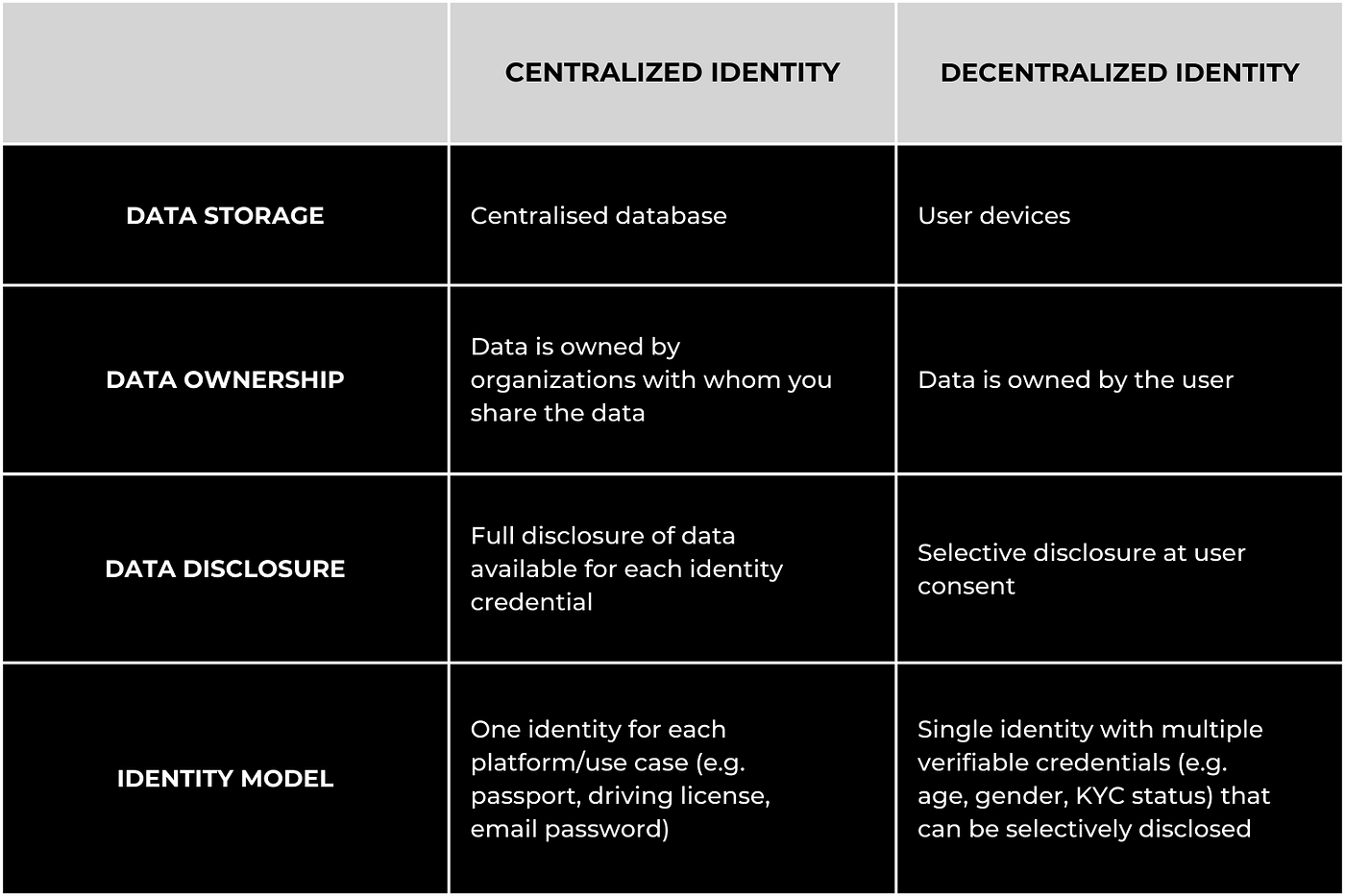
Centralized vs. Decentralized Identity Management In 2022 | by Alamira Jouman Hajjar | Fractal ID | Medium