Cloud Data: Access files anywhere, any time, on any device (A³) while improving security — Mobile Mentor

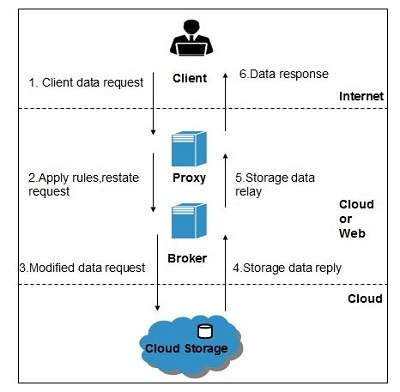
Two different system architecture options to offer server-based data... | Download Scientific Diagram

Enable Data Access on all levels with Gantner´s open GI.connectivity Features - messweb.de – das Netzwerk für Messtechnik und Sensorik

GCP Cloud Logging : How to Enable Data Access Audit For Selected Buckets | by Jerome Rajan | Google Cloud - Community | Medium

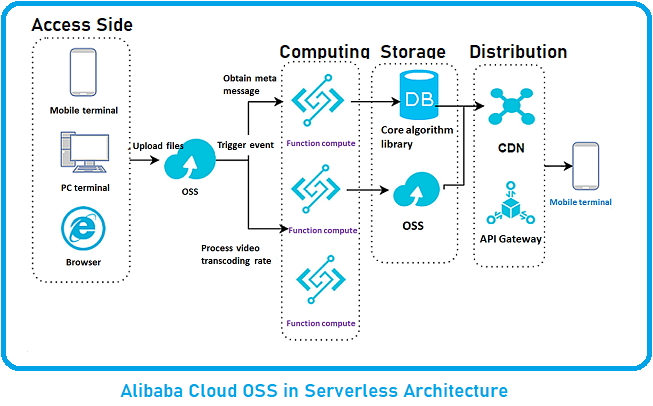
Multi-Authority Data Access Control For Cloud Storage System With Attribute-Based Encryption | Semantic Scholar

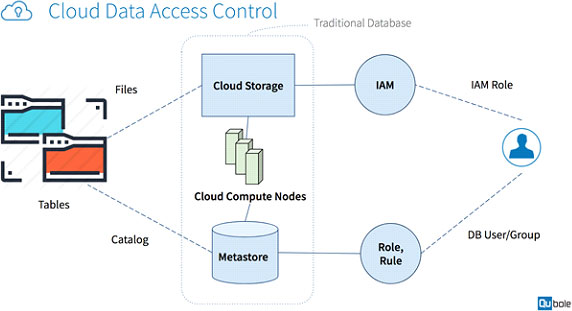
Enhanced security‐aware technique and ontology data access control in cloud computing - Kiran - 2020 - International Journal of Communication Systems - Wiley Online Library

Big-Data-Access-Analyse-Prozess und sichere Speicherung Internet-Sicherheit Technologien isometrisches Flussdiagramm hellblauer Hintergrund Vektordarstellung Stock-Vektorgrafik - Alamy
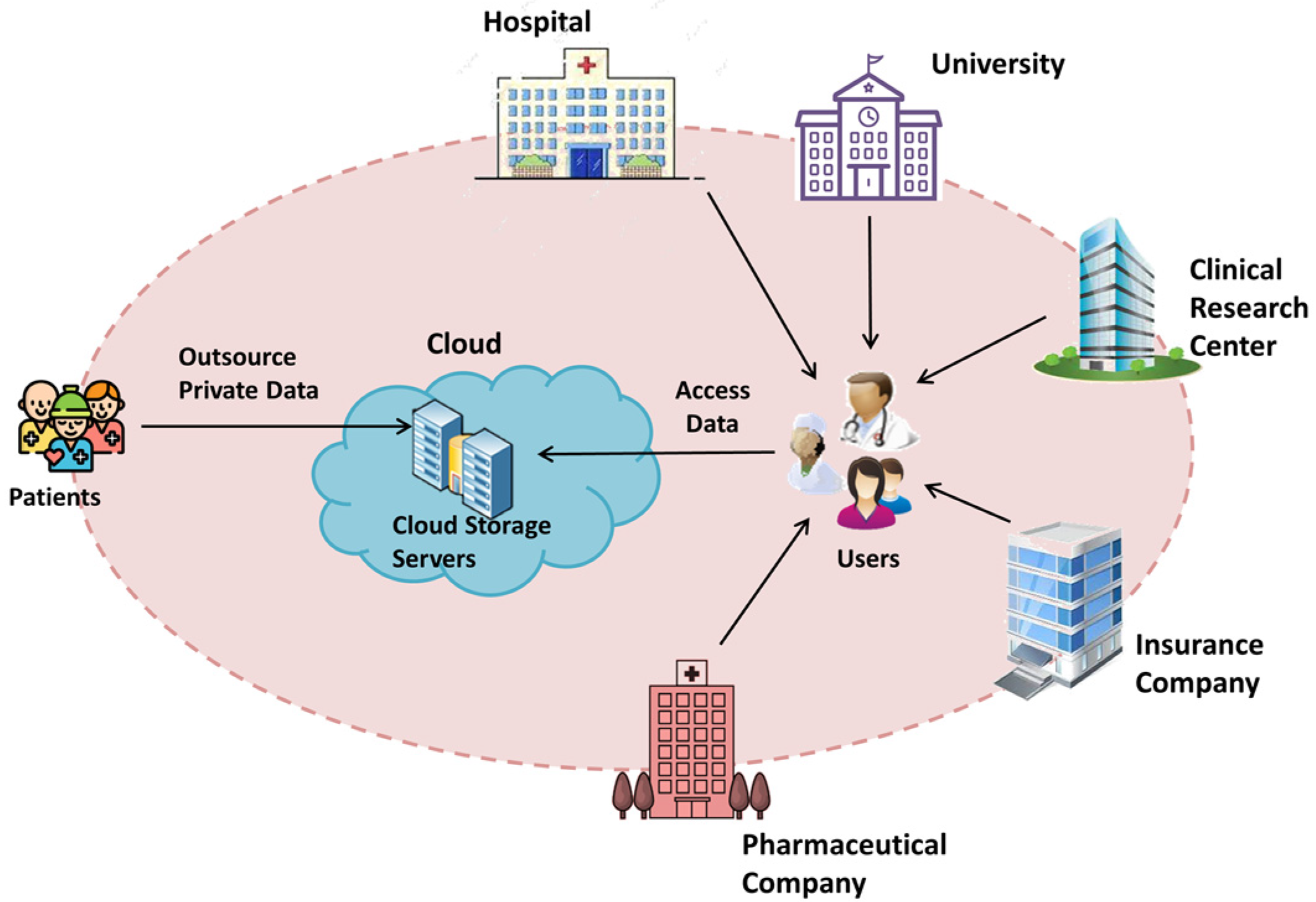
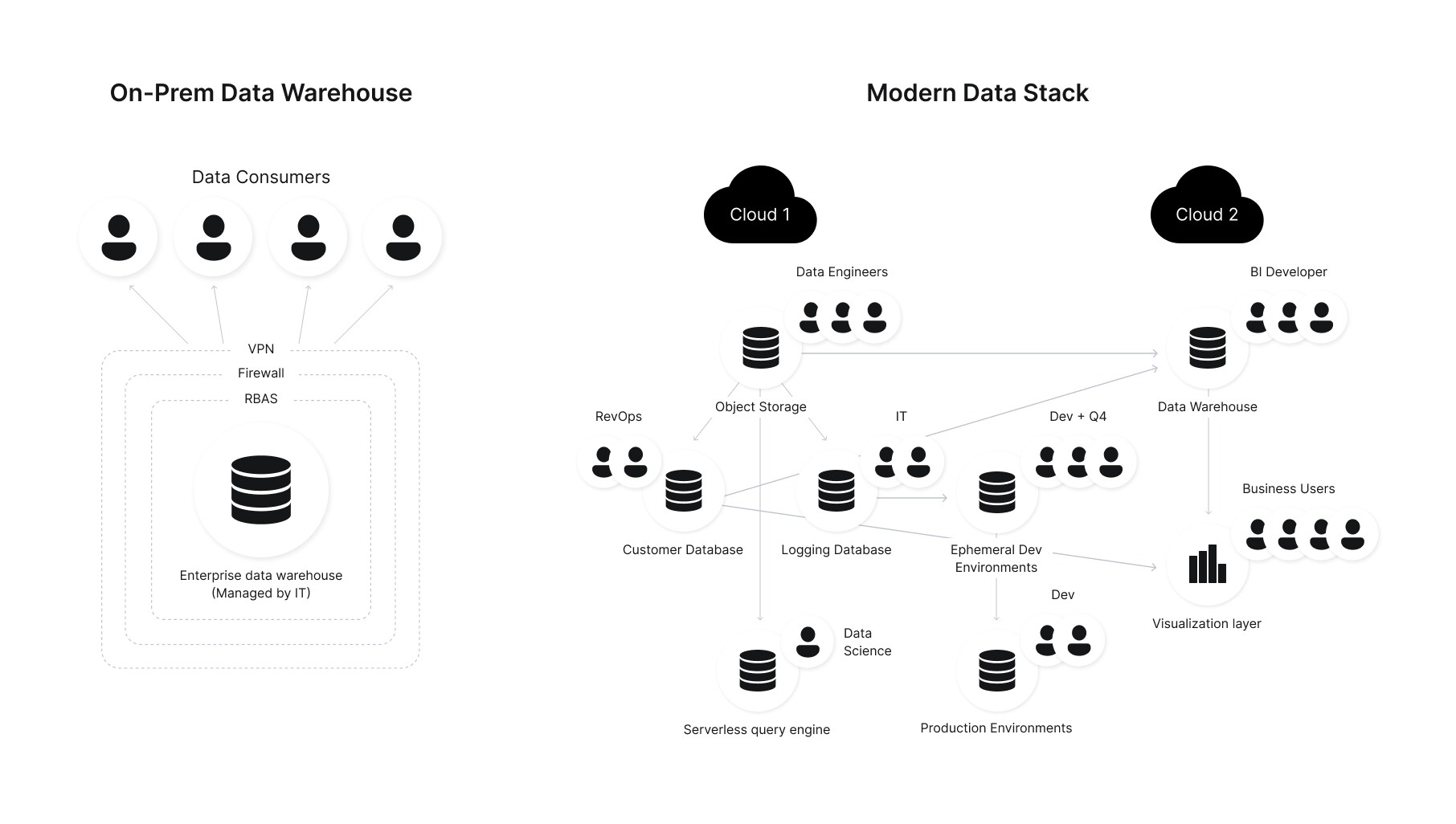
Sensors | Free Full-Text | Secured and Privacy-Preserving Multi-Authority Access Control System for Cloud-Based Healthcare Data Sharing