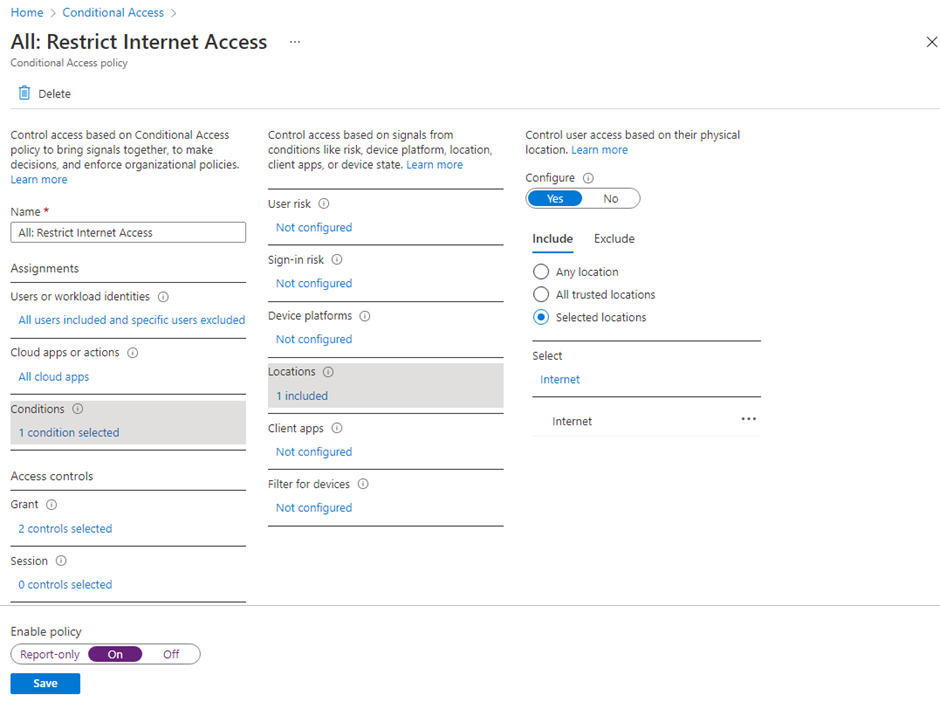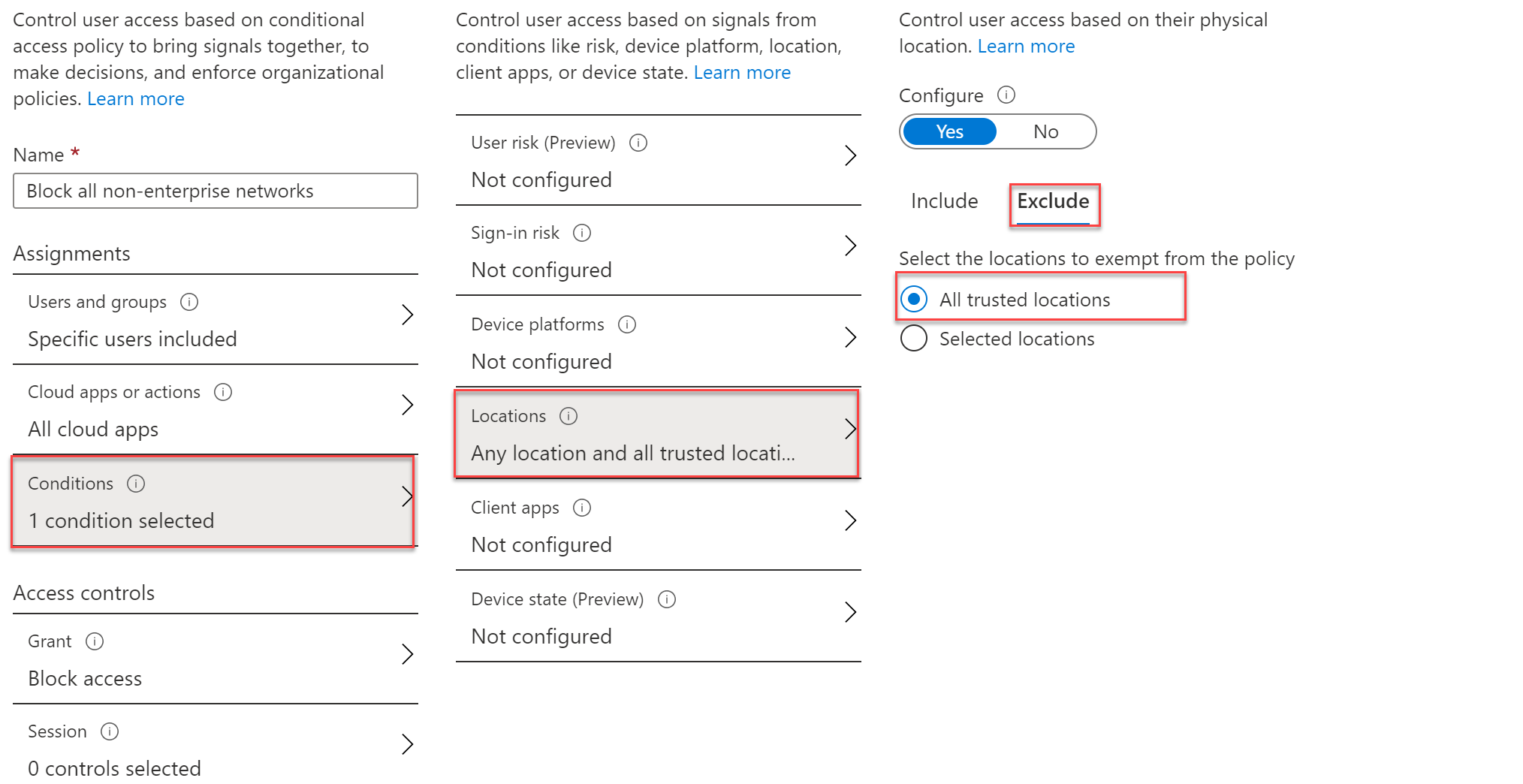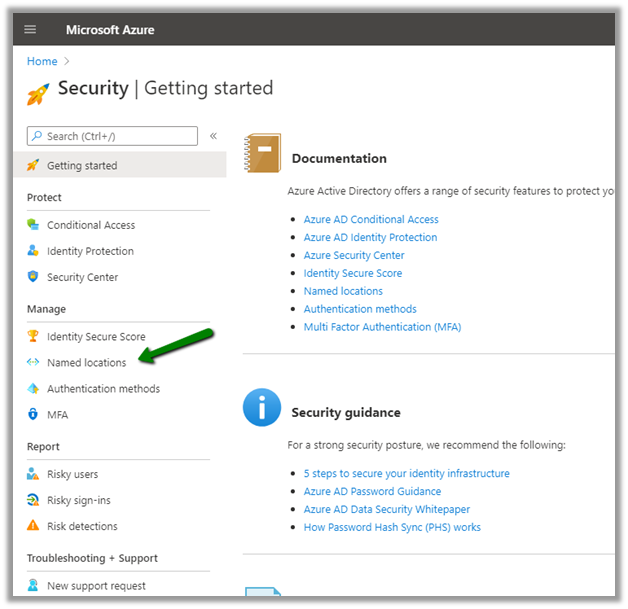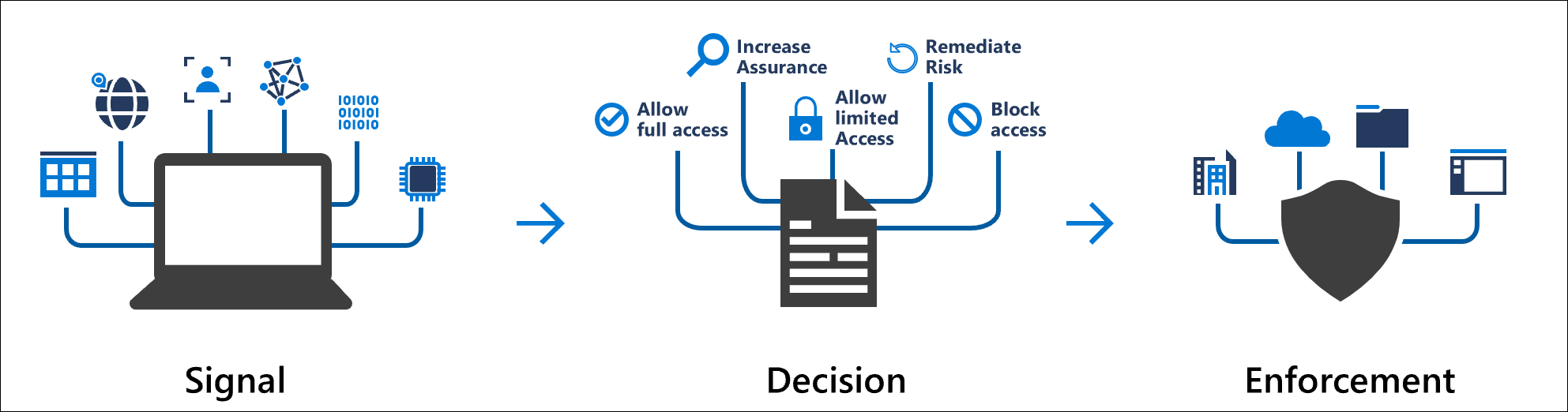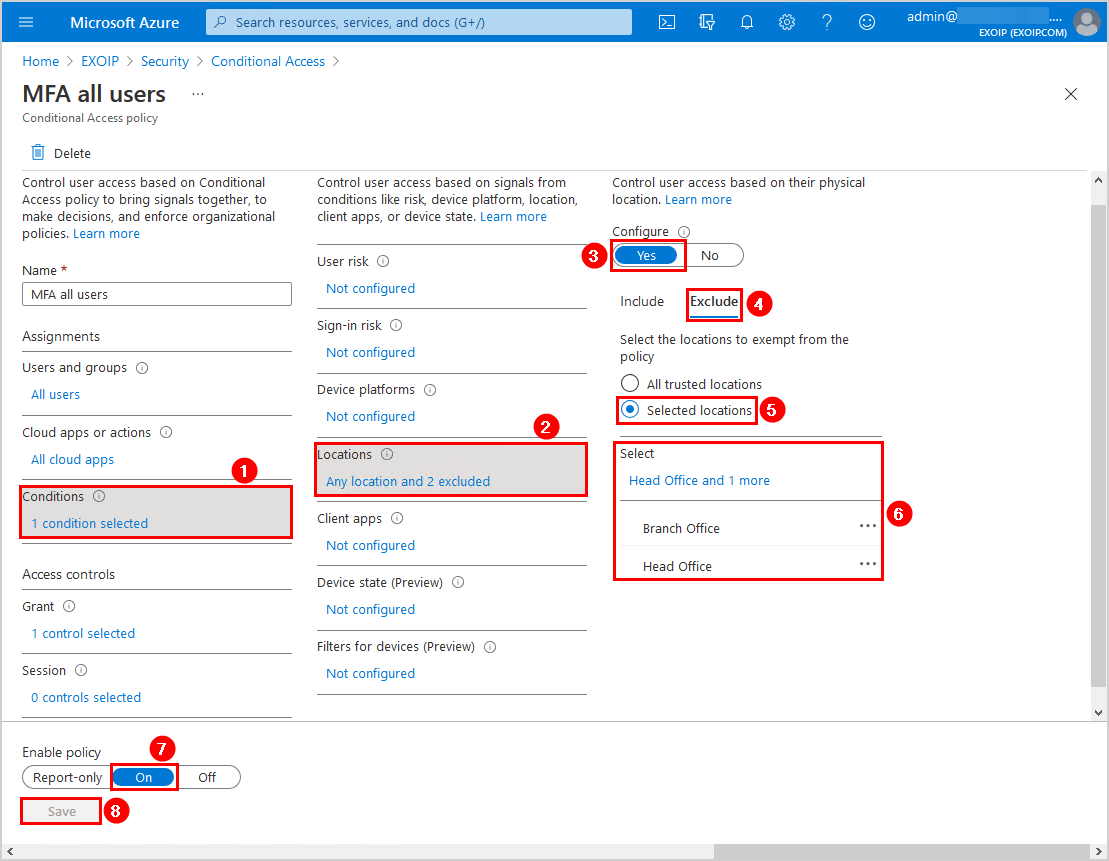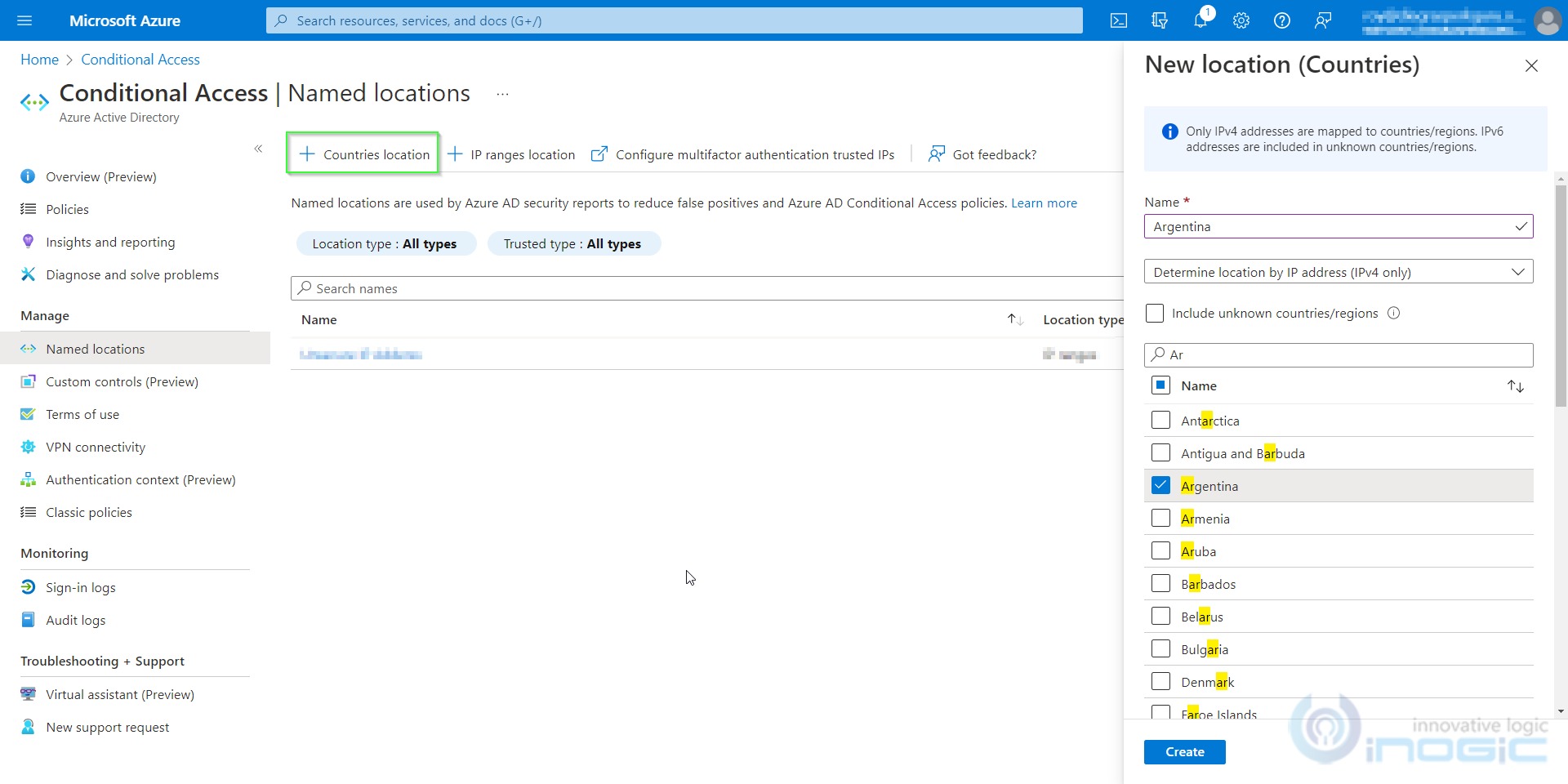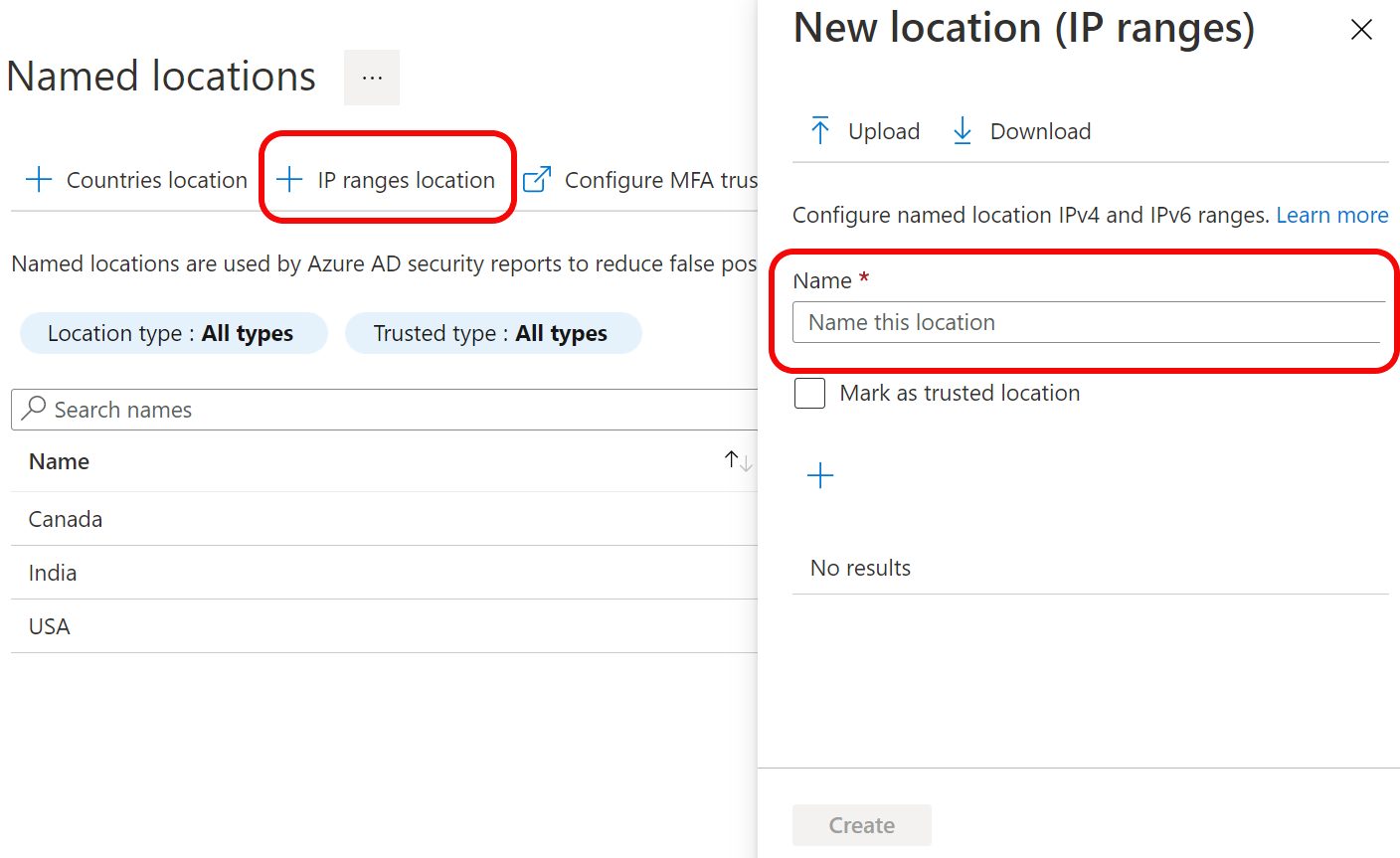
Configuring Conditional Access Policy to restrict access from specific IP or Location - Penthara Technologies
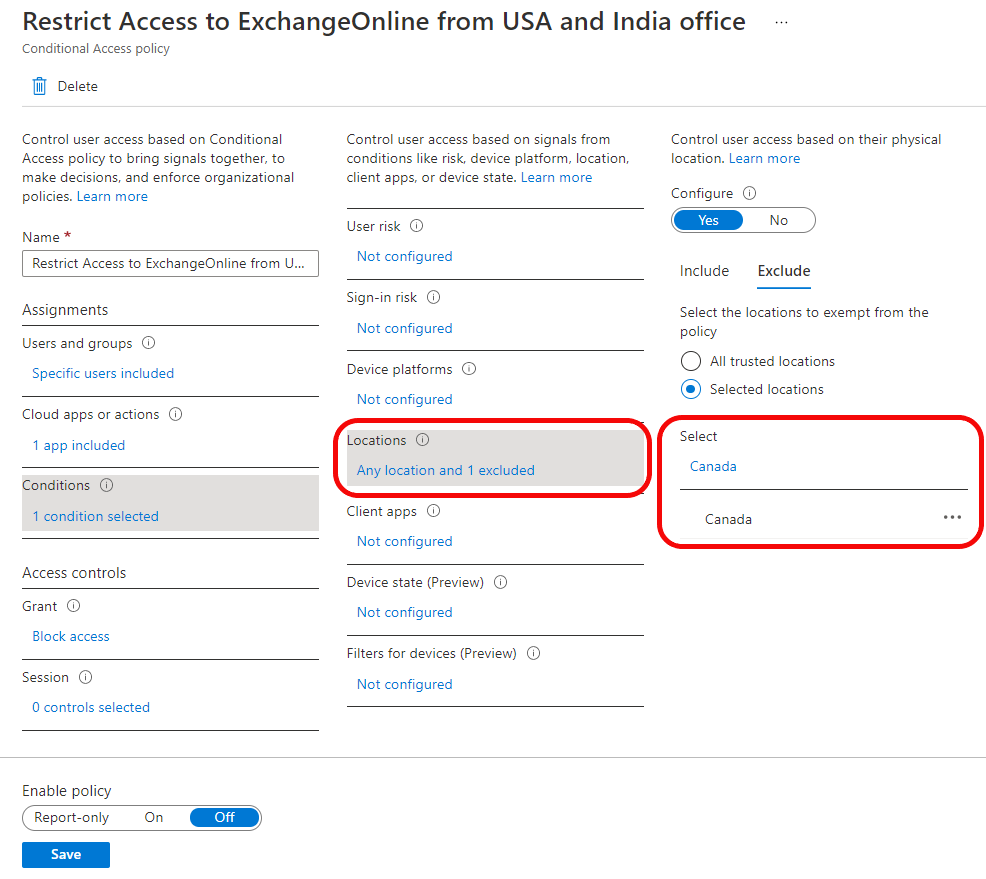
Configuring Conditional Access Policy to restrict access from specific IP or Location - Penthara Technologies
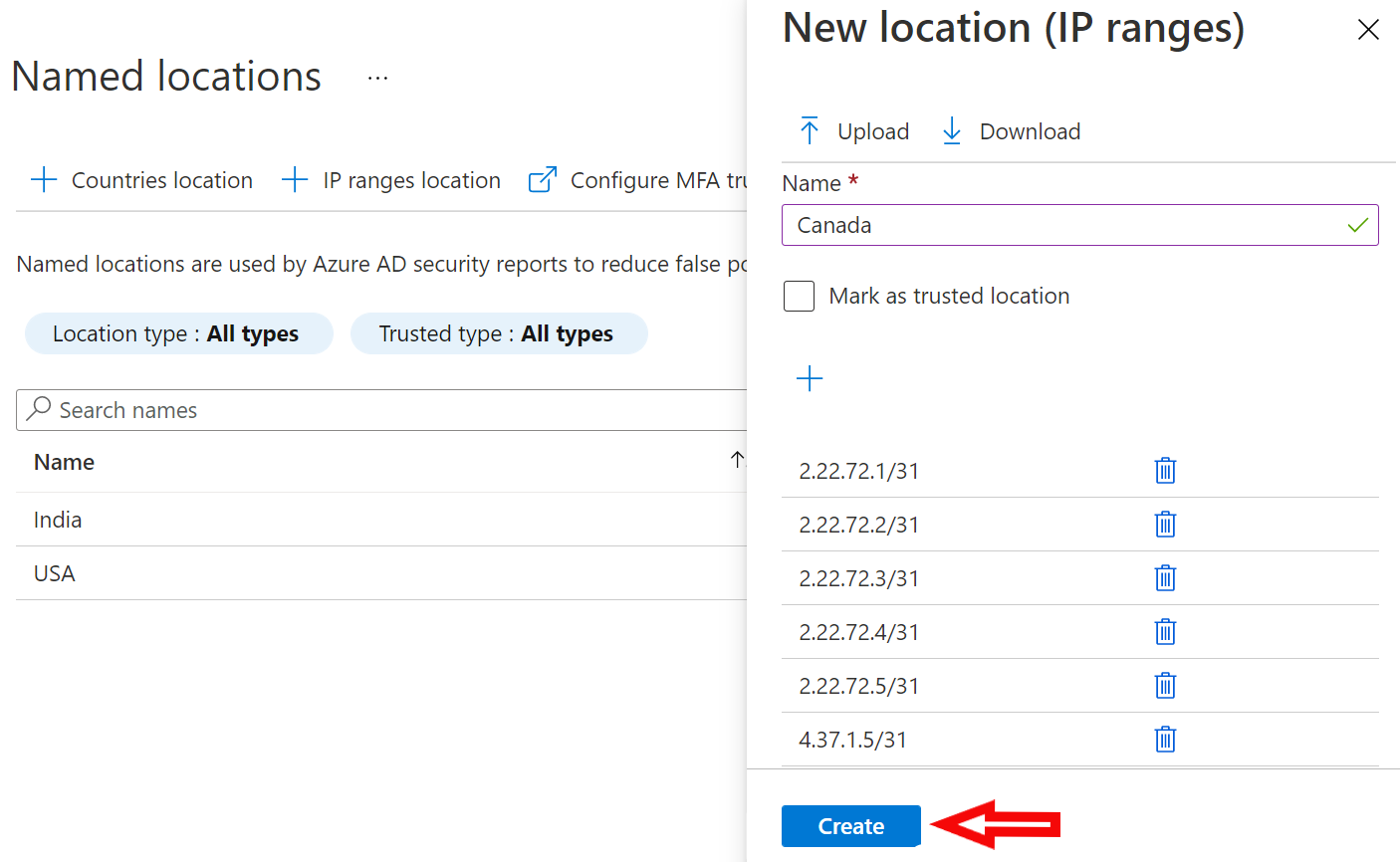
Configuring Conditional Access Policy to restrict access from specific IP or Location - Penthara Technologies

Step by Step How to Configuring Conditional Access Policy To Restrict Access From Specific Location in Office 365 – Just a Random Microsoft Azure and Computing Tech info