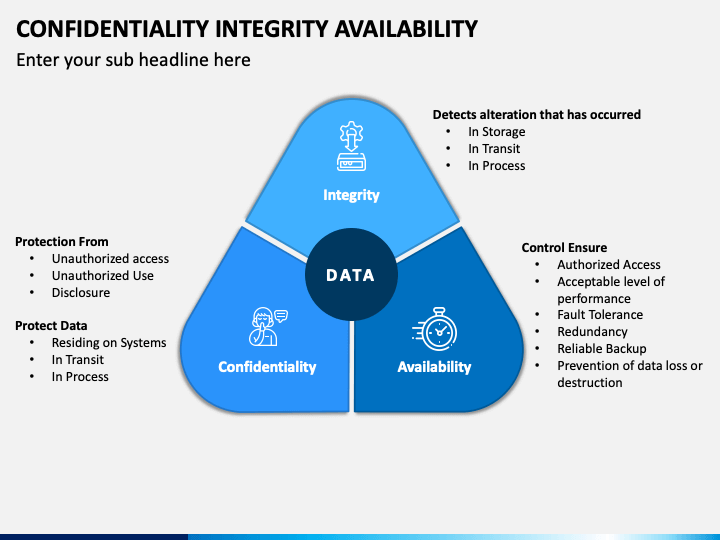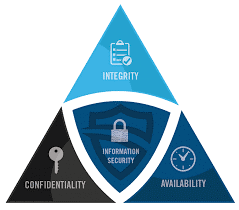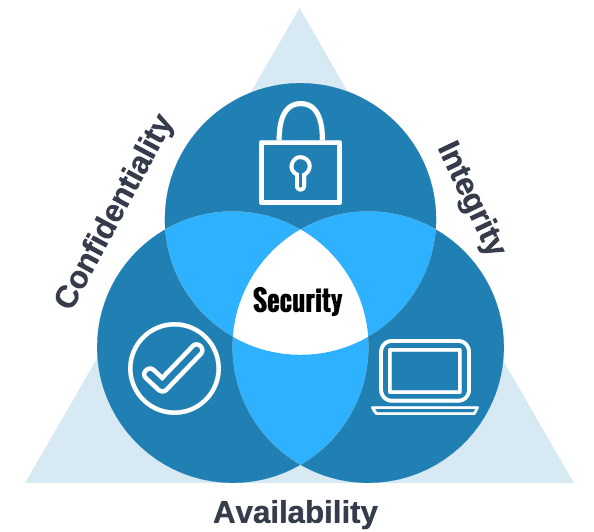
Ensure Confidentiality, Integrity and Availability of corporate data in a distributed workforce - ManageEngine Mobile Device Manager Plus

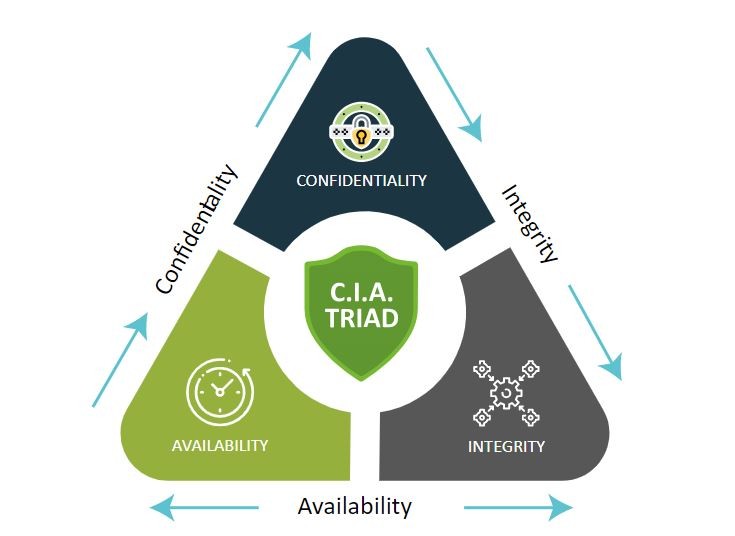
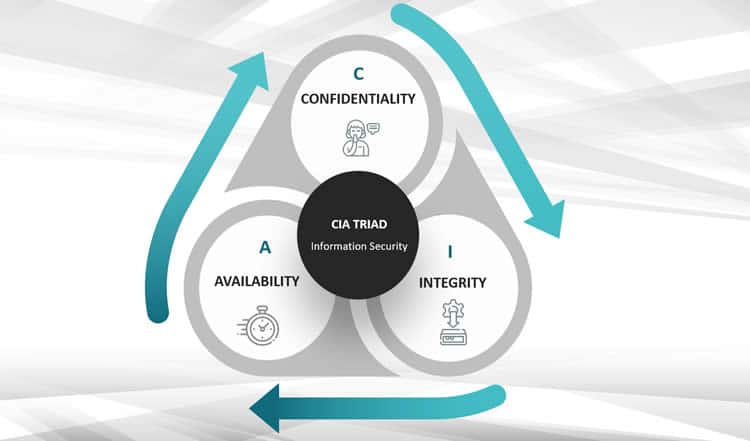
Confidentiality, Integrity & Availability Concerns | CompTIA IT Fundamentals FC0-U61 | 6.1 – Technology Gee
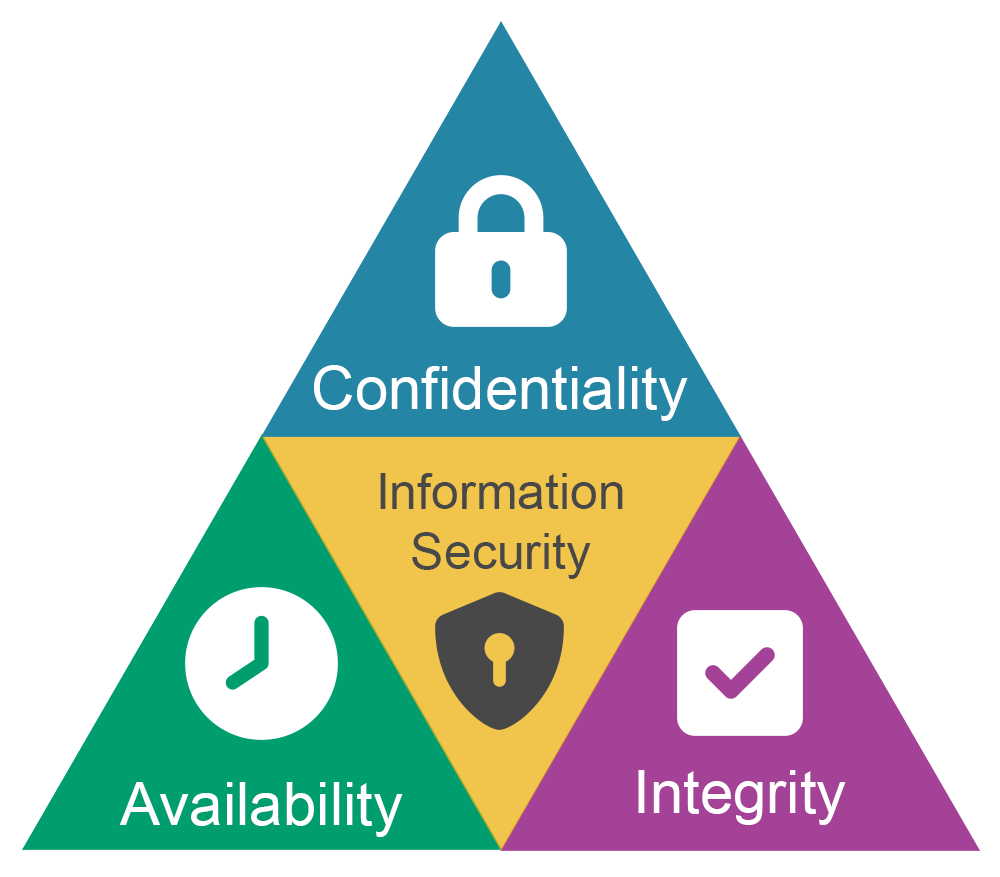
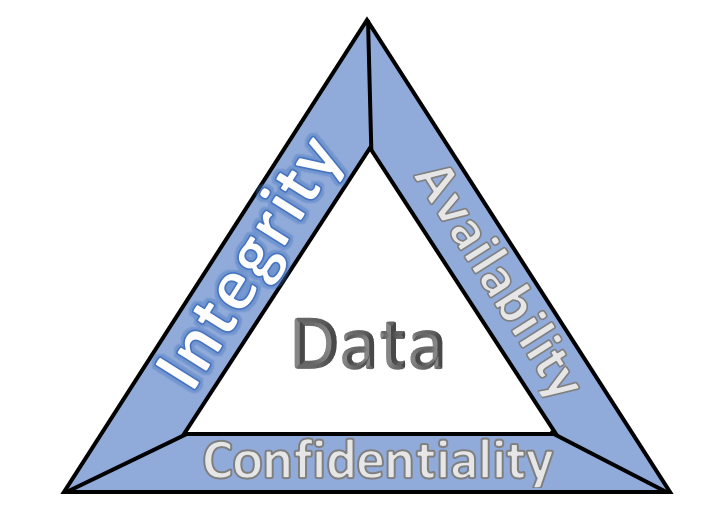
Demystifying the Security CIA Triangle: Understanding Confidentiality, Integrity, and Availability in Information Security | by Dmitrii Zavalei | Medium
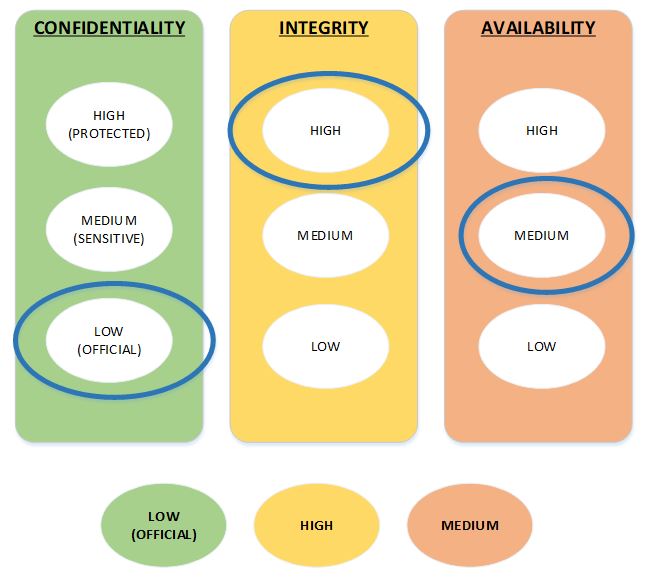
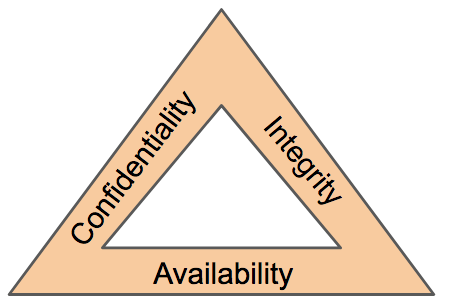
![PDF] The Confidentiality – Integrity – Accessibility Triad into the Knowledge Security. A Reassessment from the Point of View of the Knowledge Contribution to Innovation | Semantic Scholar PDF] The Confidentiality – Integrity – Accessibility Triad into the Knowledge Security. A Reassessment from the Point of View of the Knowledge Contribution to Innovation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0ee802e67b3ccf3cd0e9bb432c54822c5172e599/4-Figure1-1.png)
PDF] The Confidentiality – Integrity – Accessibility Triad into the Knowledge Security. A Reassessment from the Point of View of the Knowledge Contribution to Innovation | Semantic Scholar
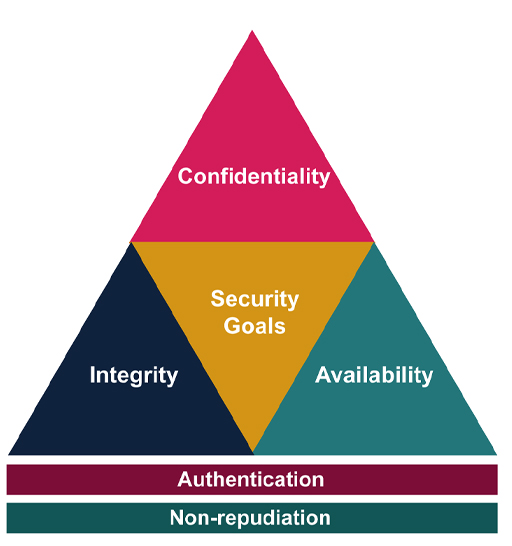
Gamified Intelligent Cyber Aptitude and Skills Training (GICAST): Week 1: 1.1 | OpenLearn - Open University

Gamified Intelligent Cyber Aptitude and Skills Training (GICAST): Week 1: 1.1 | OpenLearn - Open University