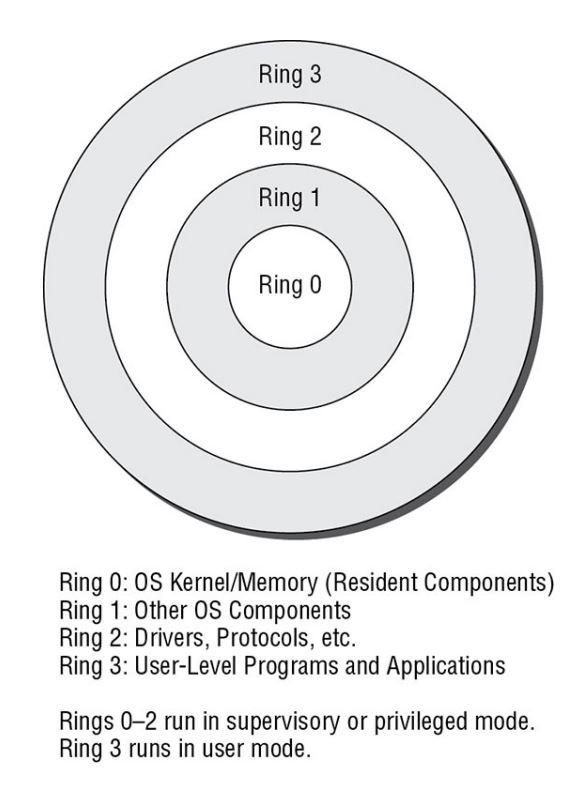
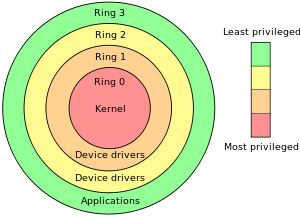
Modulare Architektur mit Subsystemen - So wird Ihr System besser: Geheimes Windows-Wissen für Profis - cio.de
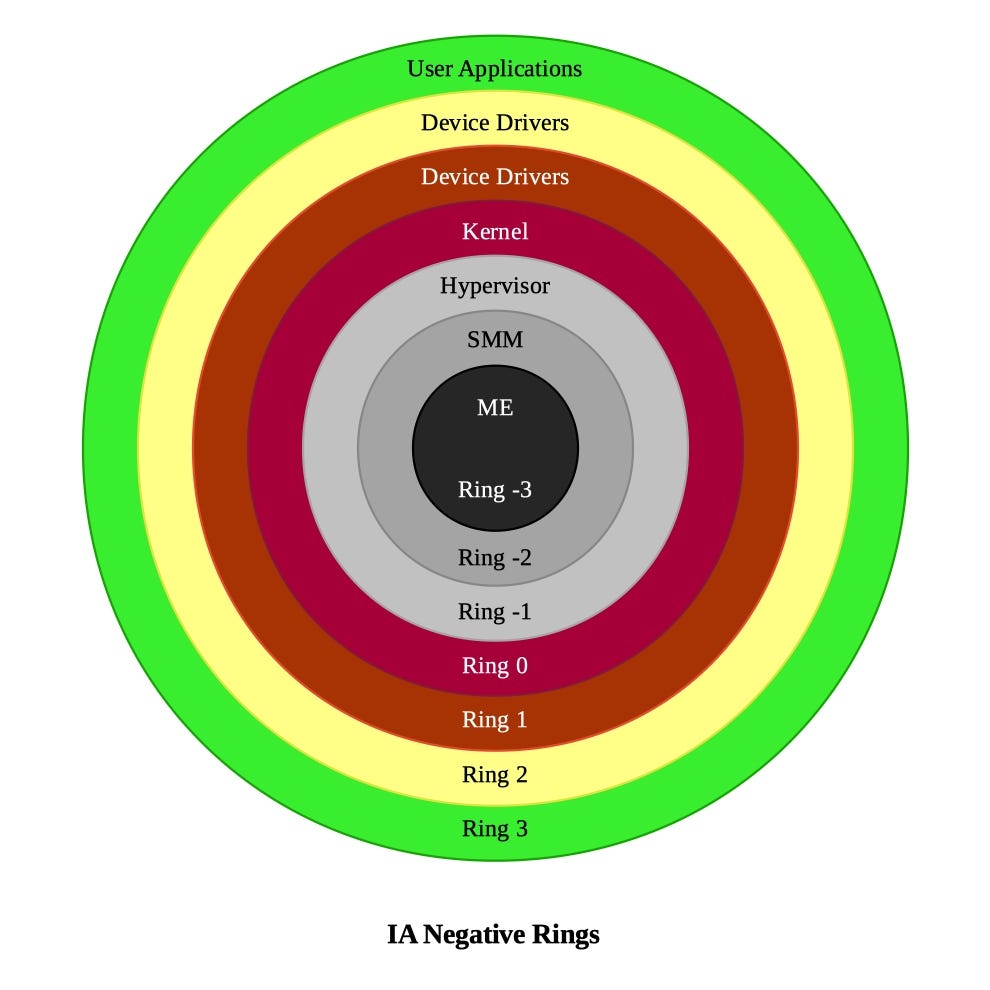
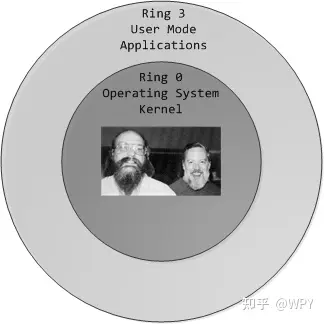
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium

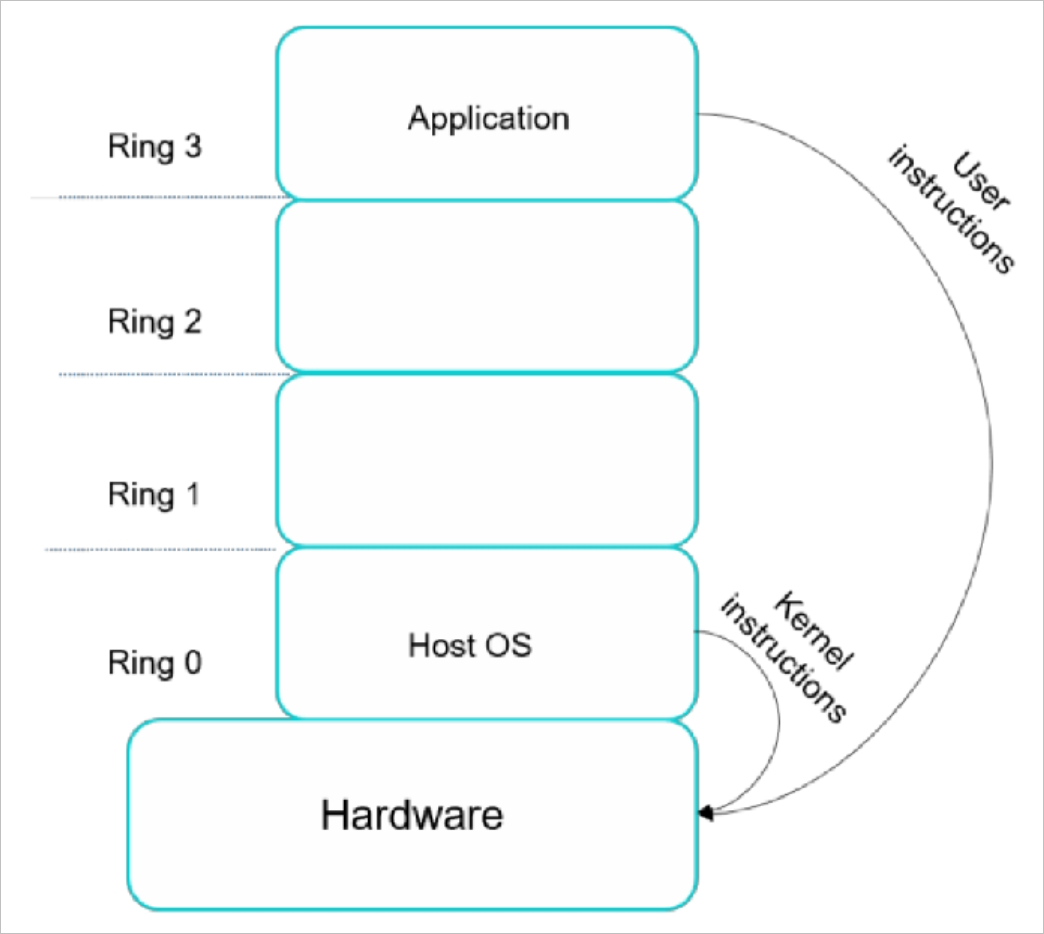
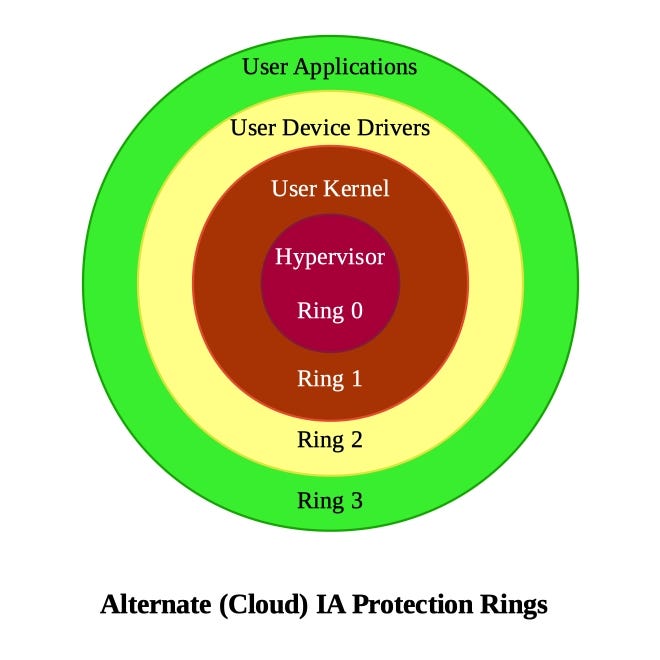
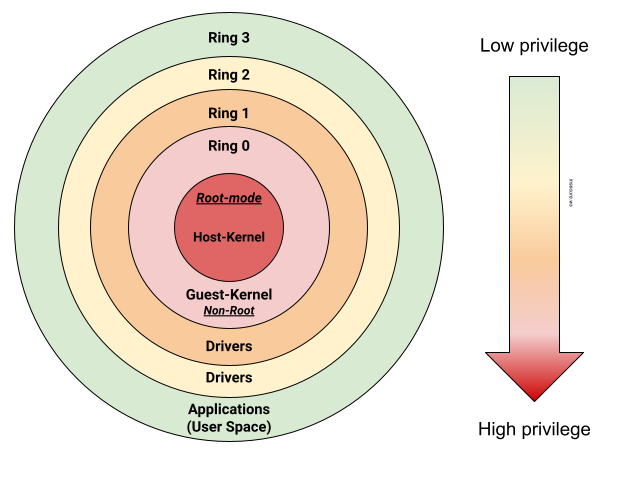
Intel/AMD virtualization isolation and containment :: Michiel Kalkman — Software | Security | Product | Design

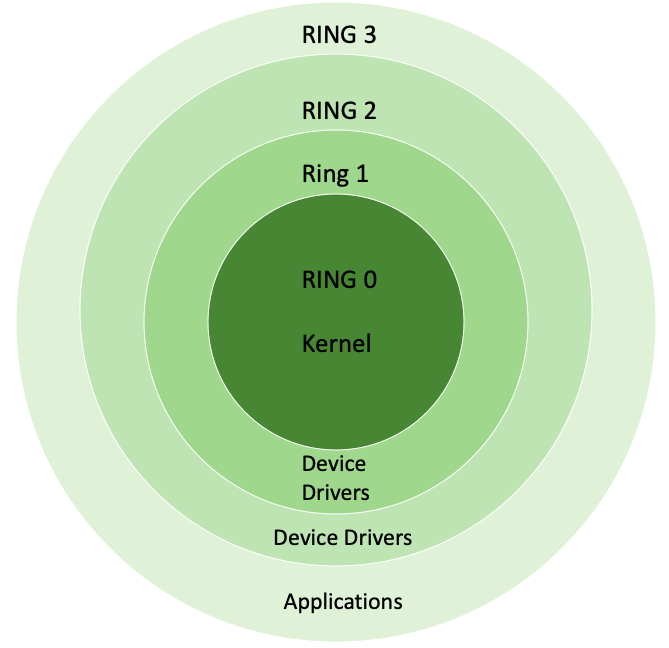
What is kernel rings in a system ? | kernel protection ring | cloudpradeep | by cloud pradeep | Medium
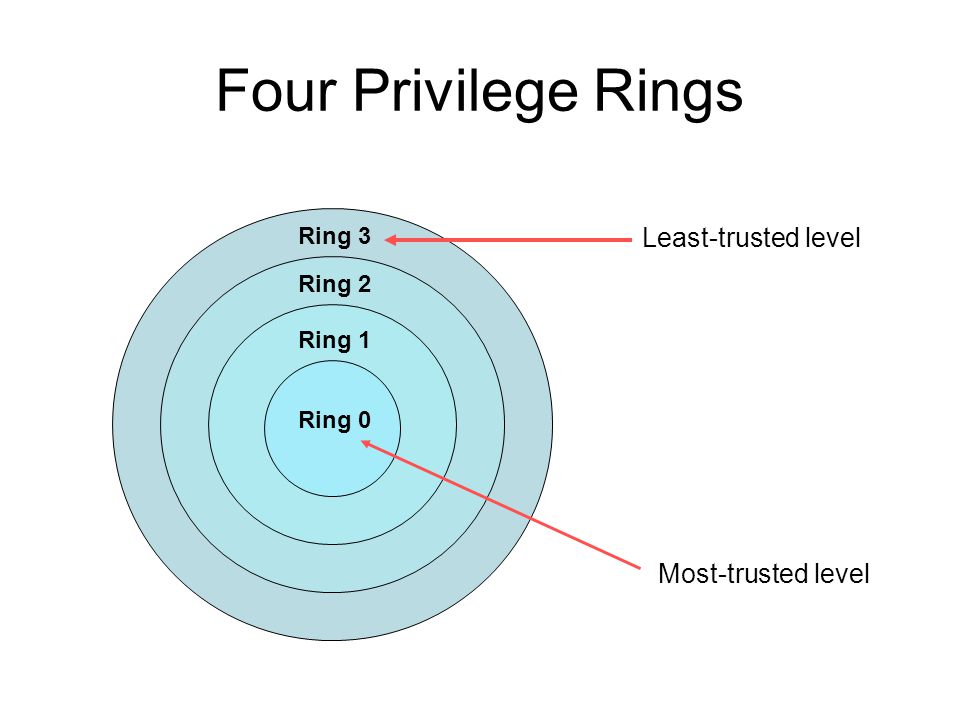
Ring-transitions for EM64T How the CPU can accomplish transitions among its differing privilege-levels in 64-bit mode. - ppt download
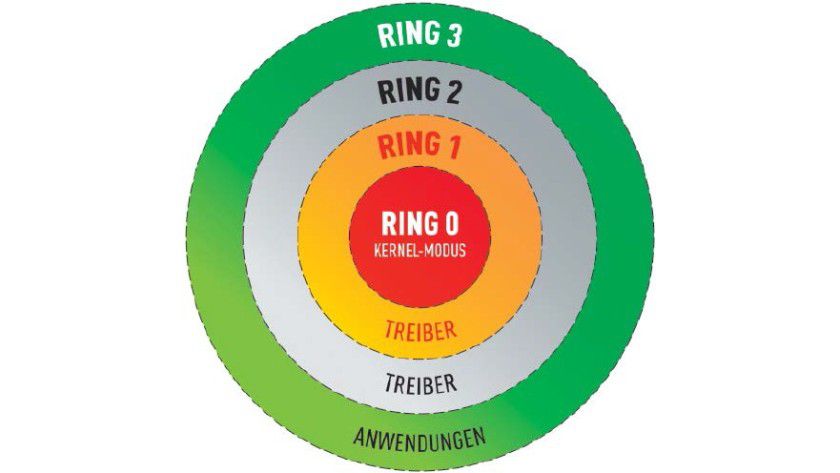
Prozessoren von AMD und Intel: Ringe regeln die Privilegien - Virtualbox, Vmware und Co.: Crashkurs: Wie funktionieren eigentlich virtuelle PCs? - TecChannel Workshop

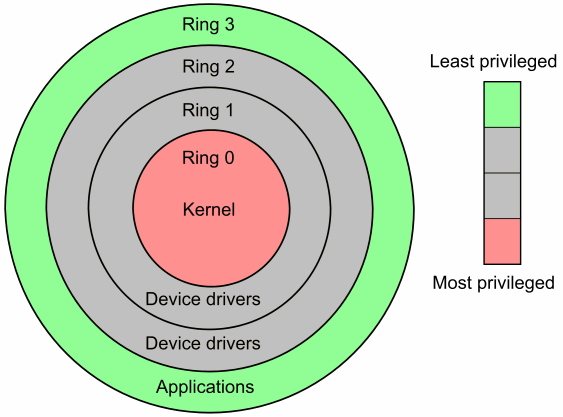



![Execution Rings for the x86 64 Architecture. See also [19] | Download Scientific Diagram Execution Rings for the x86 64 Architecture. See also [19] | Download Scientific Diagram](https://www.researchgate.net/profile/Roberto-Pietro/publication/326696873/figure/fig1/AS:655531282796567@1533302245961/Execution-Rings-for-the-x86-64-Architecture-See-also-19_Q320.jpg)