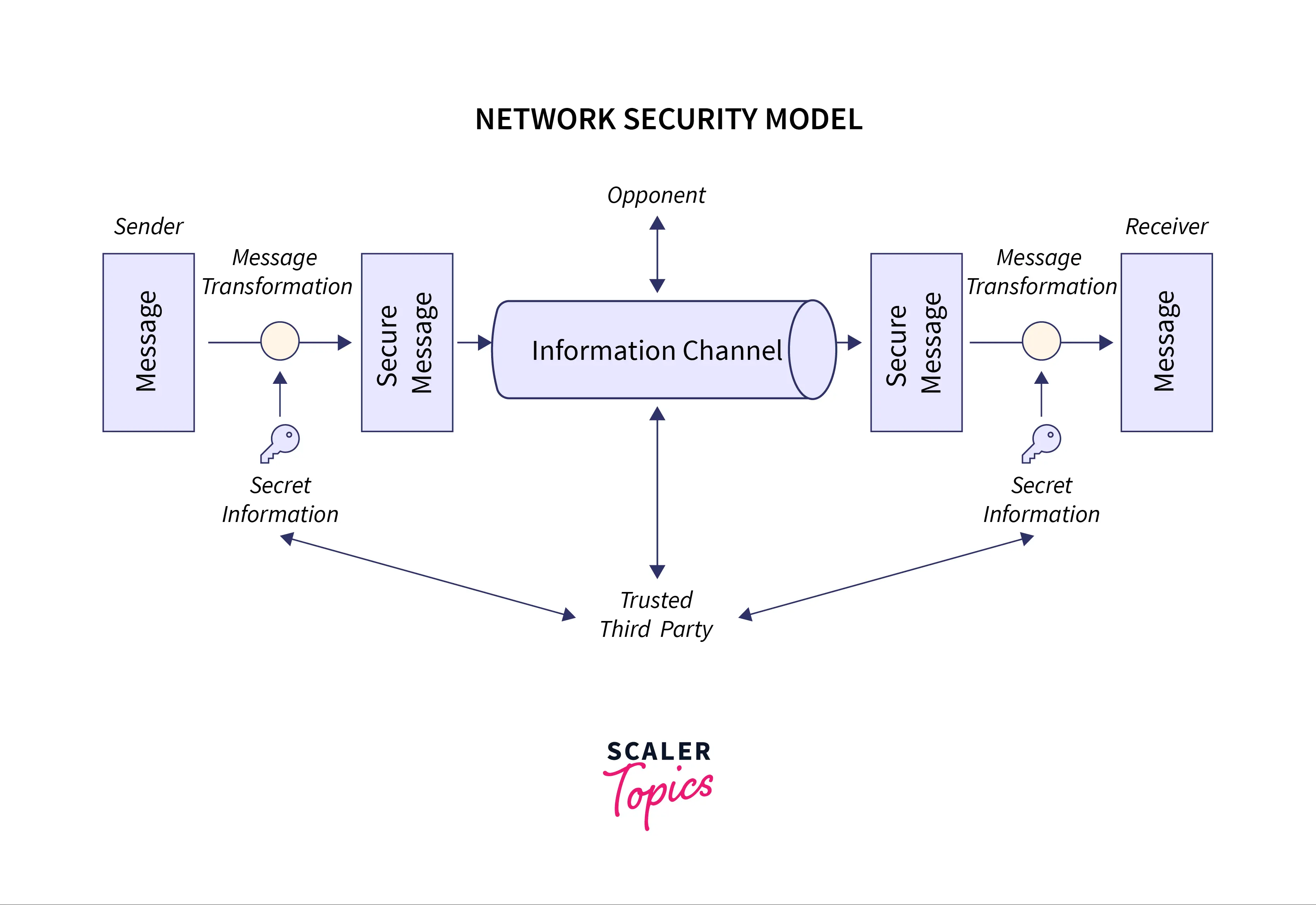
What is Cryptography in security? What are the different types of Cryptography? | Encryption Consulting

Online Course: OWASP Top 10: #1 Broken Access Control and #2 Cryptographic Failures from LinkedIn Learning | Class Central
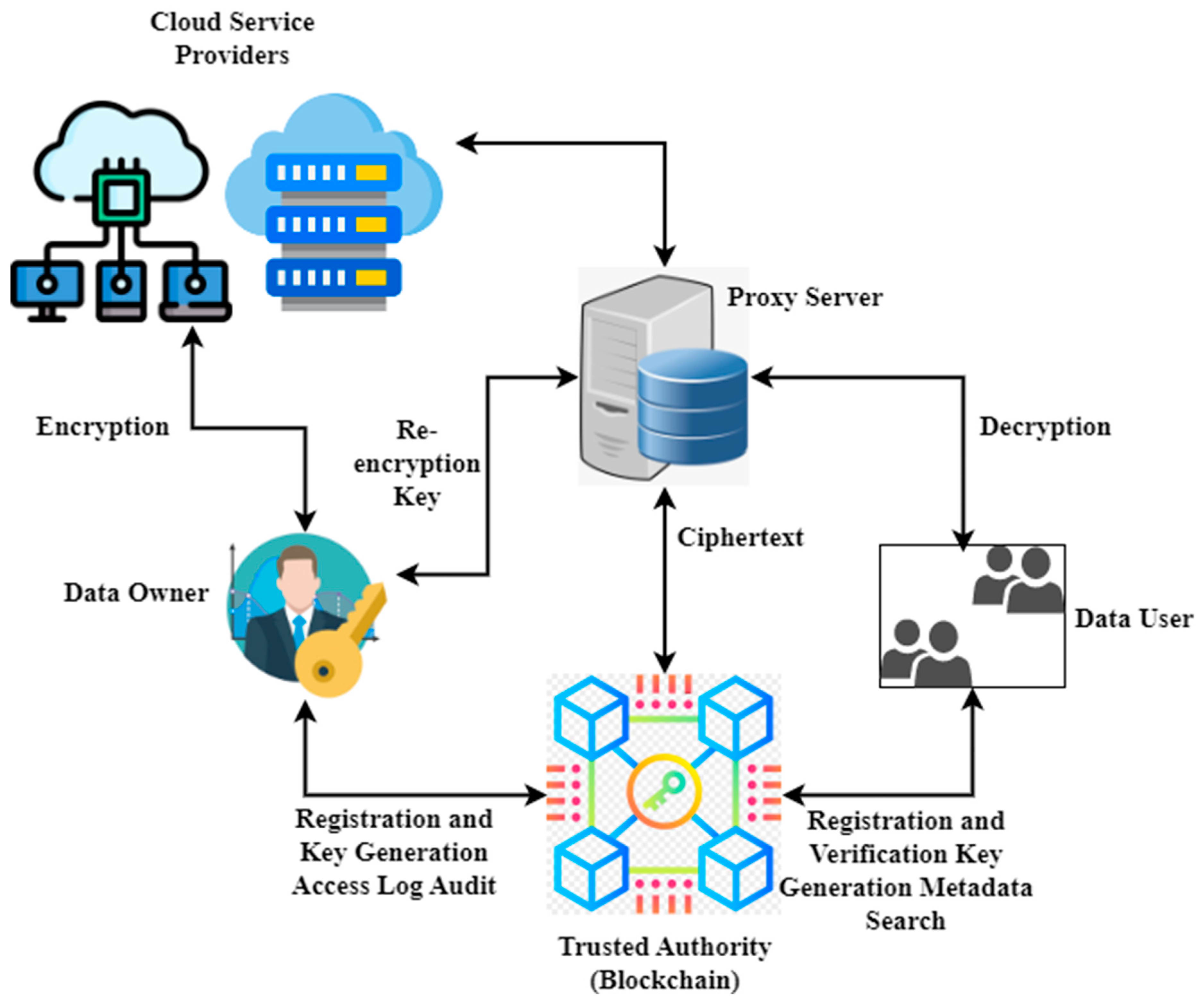
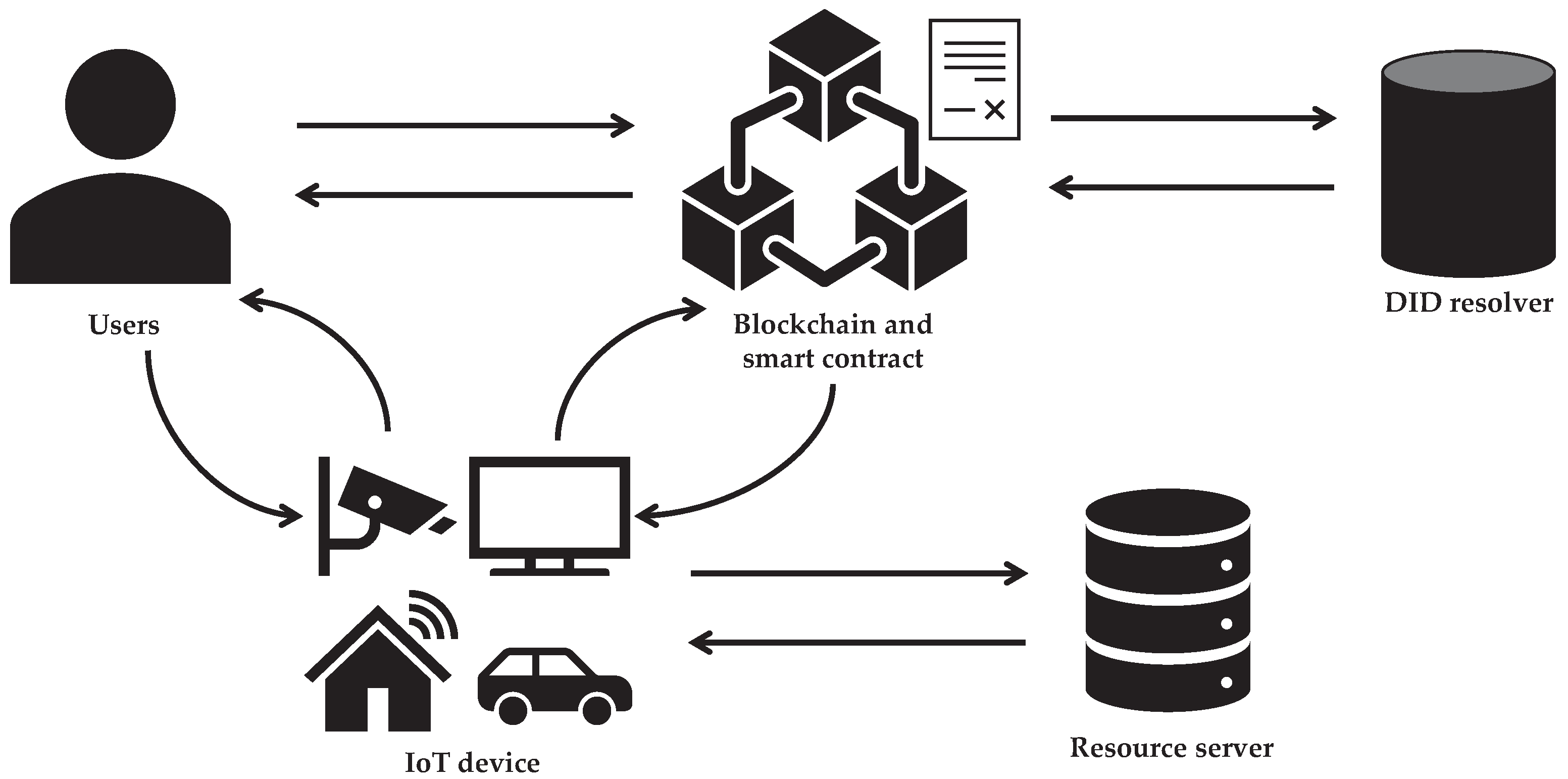
Sensors | Free Full-Text | Applying Access Control Enabled Blockchain (ACE-BC) Framework to Manage Data Security in the CIS System

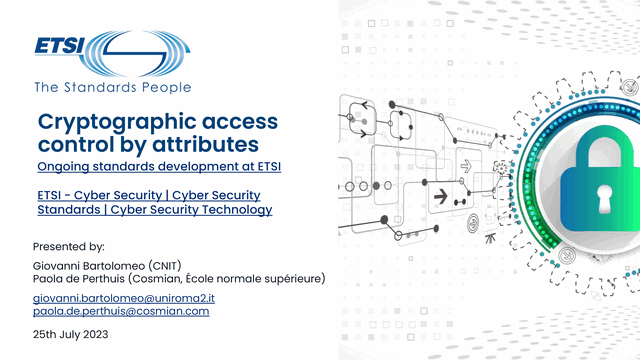
Cryptographic access control uses cryptographic techniques to protect data and control access to resources. | by Dale Clifford | Internet Stack | Jan, 2024 | Medium


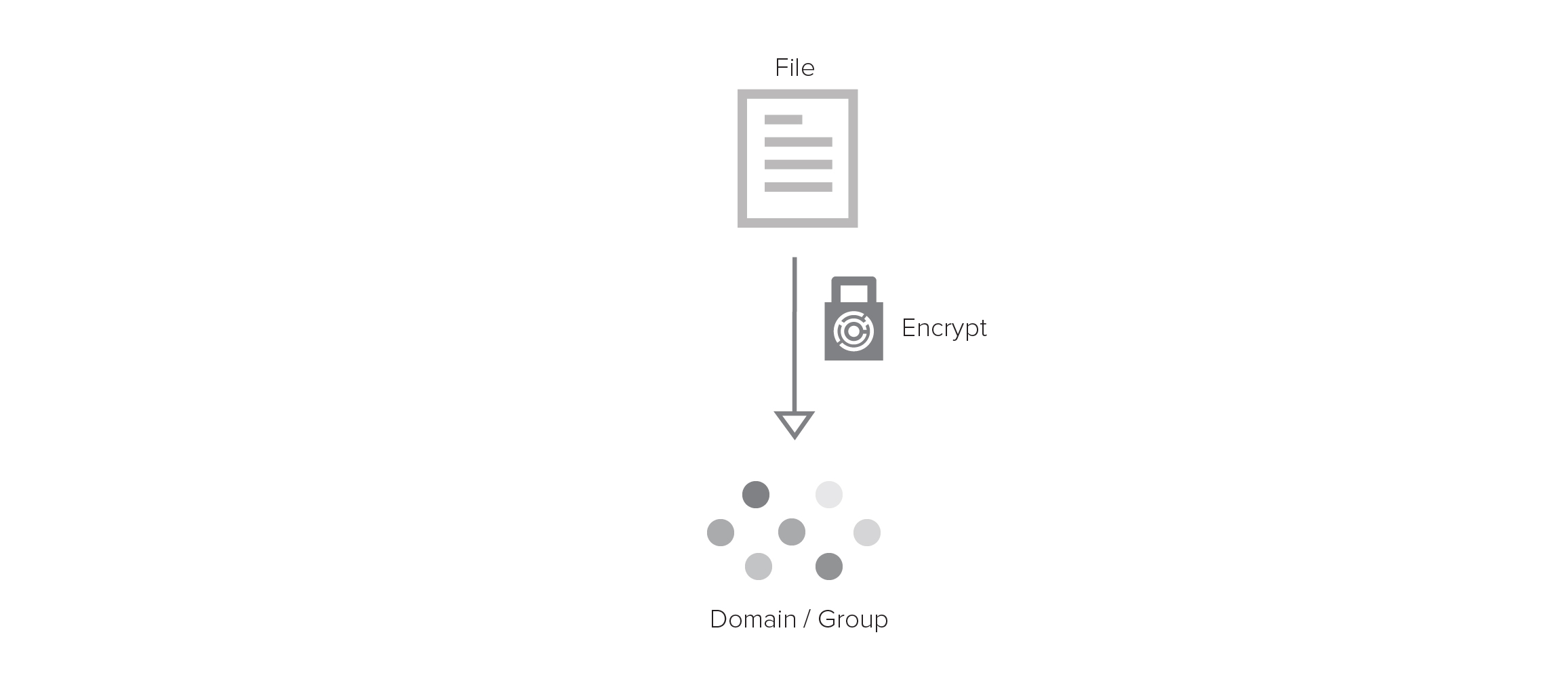

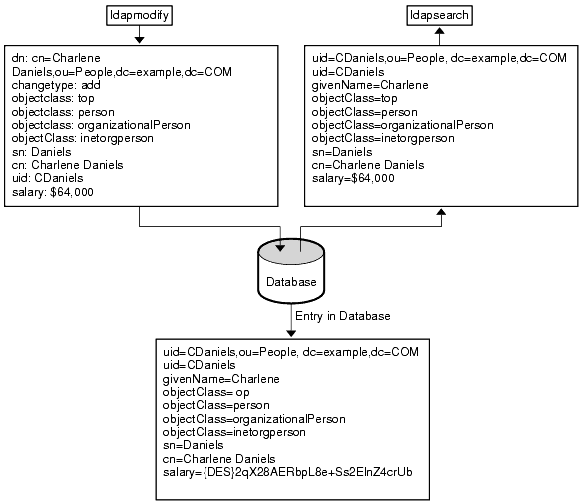
![MS-STOROD]: Encrypted File Access Control and Encryption | Microsoft Learn MS-STOROD]: Encrypted File Access Control and Encryption | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-storod/ms-storod_files/image007.png)

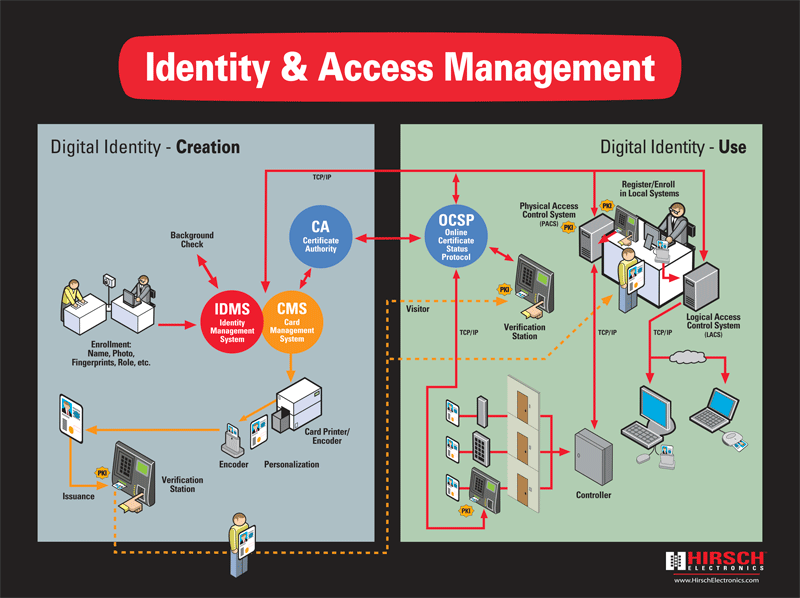





![PDF] Hybrid Cryptographic Access Control for Cloud-Based EHR Systems | Semantic Scholar PDF] Hybrid Cryptographic Access Control for Cloud-Based EHR Systems | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dffbb4fd8d05fa9a844c22f09ee85abb11e956aa/2-Figure1-1.png)
![PDF] Cryptographic access control in a distributed file system | Semantic Scholar PDF] Cryptographic access control in a distributed file system | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dcf7b8c6d44b2430925861bd80fe8b40567a066a/4-Figure1-1.png)