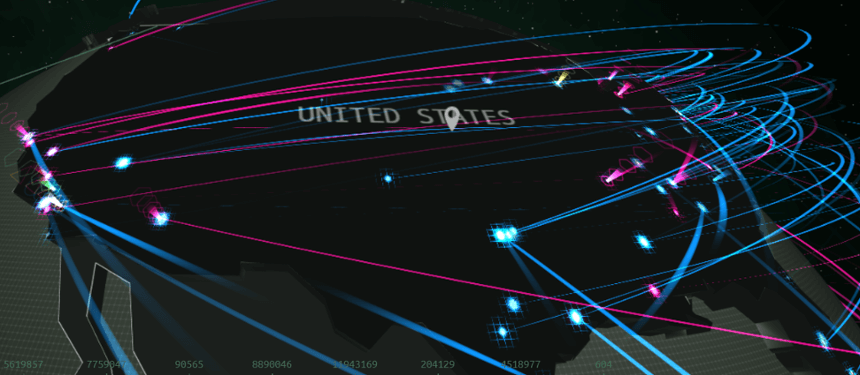
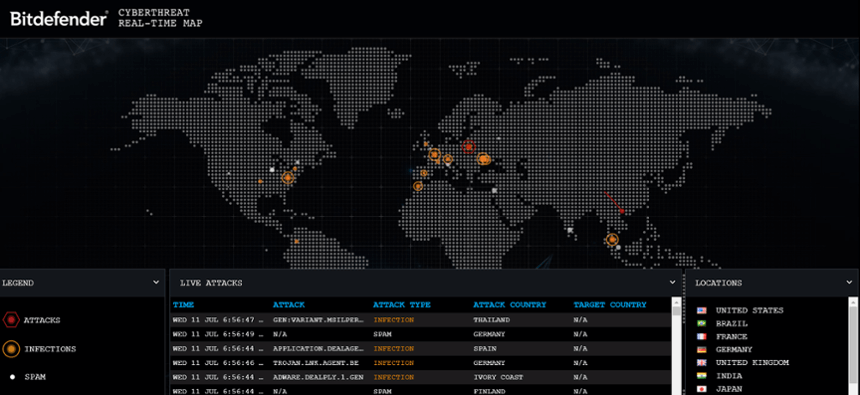
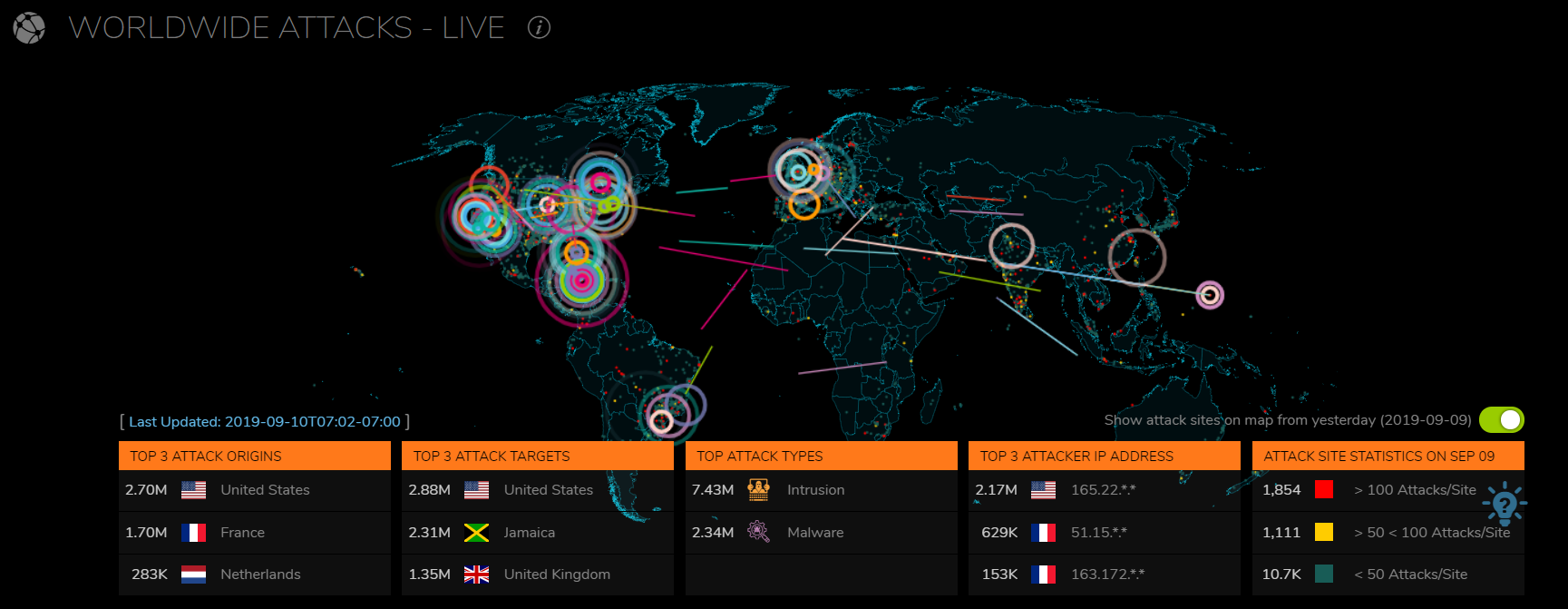
Virus in Computer. Skull on Monitor. Cyber Attack for Pc Stock Vector - Illustration of leak, antivirus: 107973654
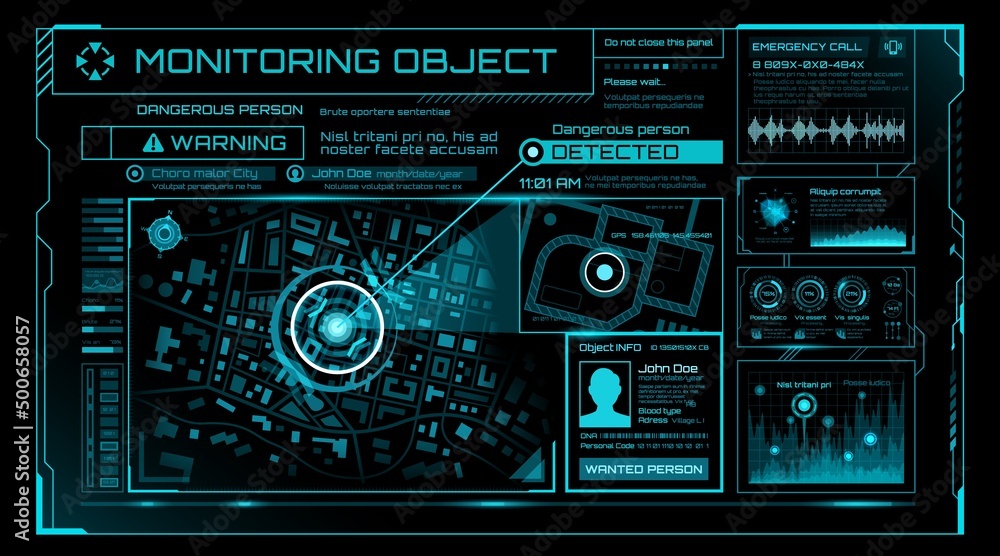
HUD security monitoring system technology, digital interface screen, vector UI. HUD cyber security monitor, target location detection or positioning and spy surveillance in global cybersecurity system Stock-Vektorgrafik | Adobe Stock

Industrial Cybersecurity: Efficiently monitor the cybersecurity posture of your ICS environment : Ackerman, Pascal: Amazon.de: Books

Virus im Computer. Schädel auf dem Monitor. Cyber Attack für pc. Tod Informationen. Blockiert Prozessor Daten funktioniert nicht. Vector Illustration Stock-Vektorgrafik - Alamy

AttackMapper - the price of cybersecurity services in Ukraine, protection against ddos attacks from the IIT Distribution company