Cyber Security. businessman using computer Network Login, Internet Security, Prevent Unauthorized Access, Personal Information, Authentication, Top Secret, Use the Internet Safely. Photos | Adobe Stock

Unauthorised Access: Physical Penetration Testing For IT Security Teams: Wil Allsopp, Kevin Mitnick: 9780470747612: Amazon.com: Books

Handwriting text writing Cyber Security. Concept meaning Protect a computer system against unauthorized access Stock Photo - Alamy

Free Vector | User verification. unauthorized access prevention, private account authentication, cyber security. people entering login and password, safety measures.

User verification. Unauthorized access prevention, private account authentication, cyber security. People entering login and password, safety measures. Vector isolated concept metaphor illustration Stock-Vektorgrafik | Adobe Stock

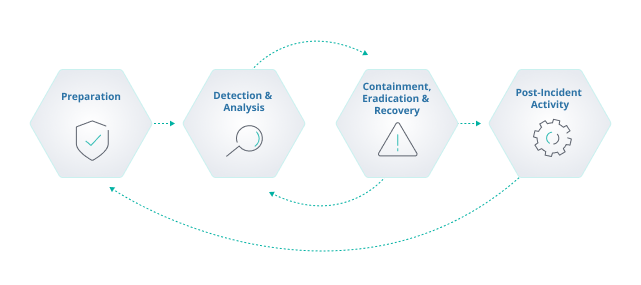
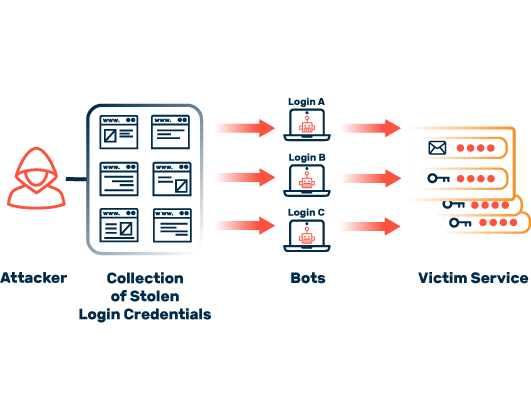
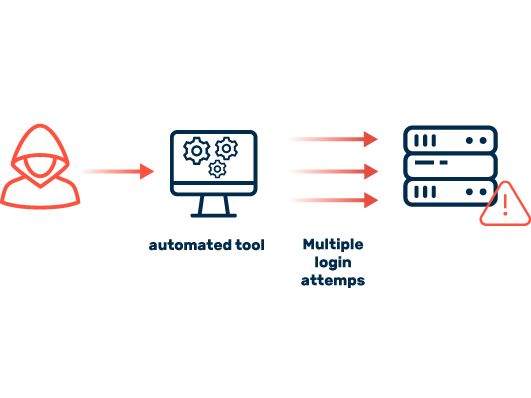
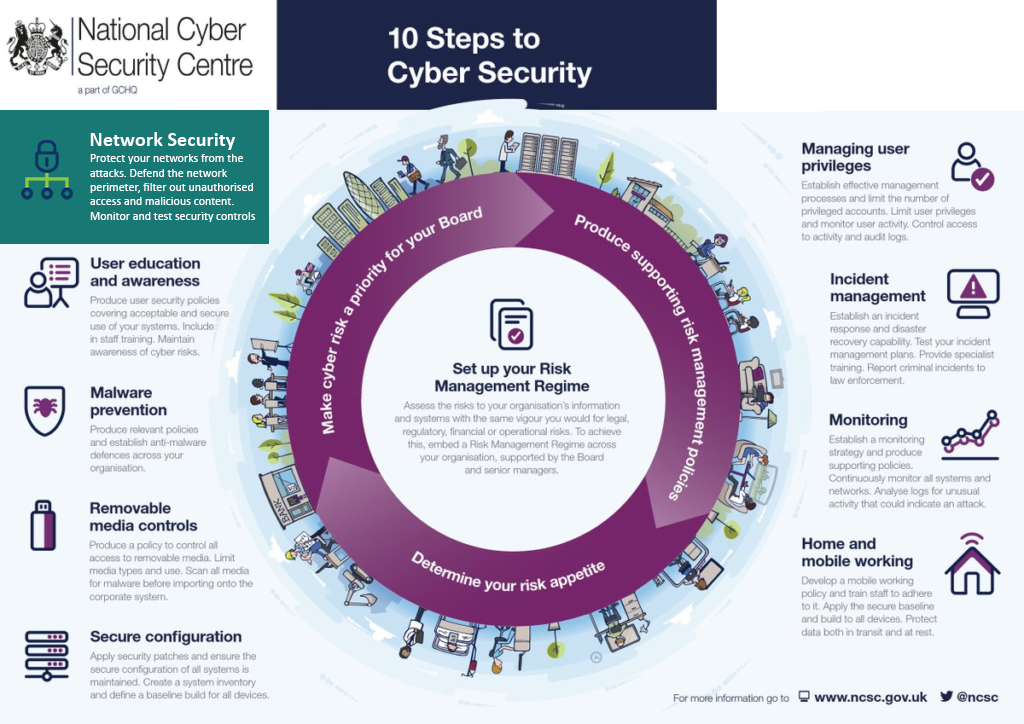
Cybersecurity Strategies: How to Prevent Unauthorized Access to Organizational Assets | ITsecurity Demand