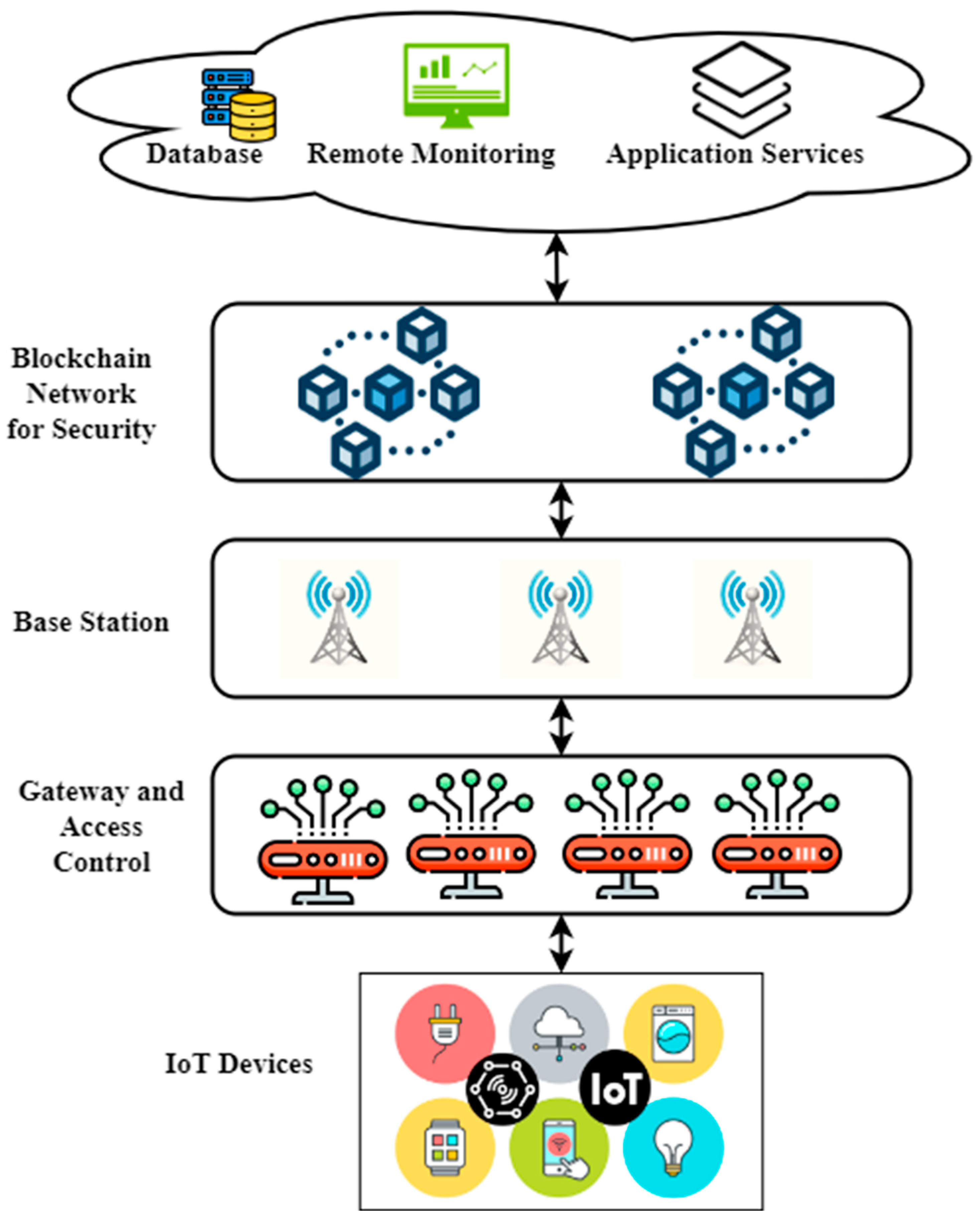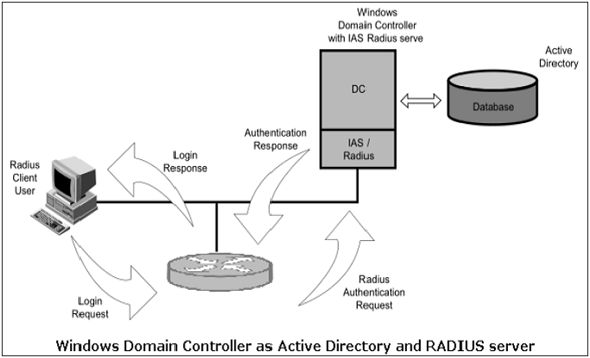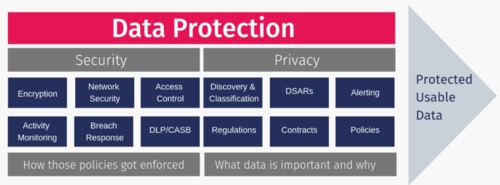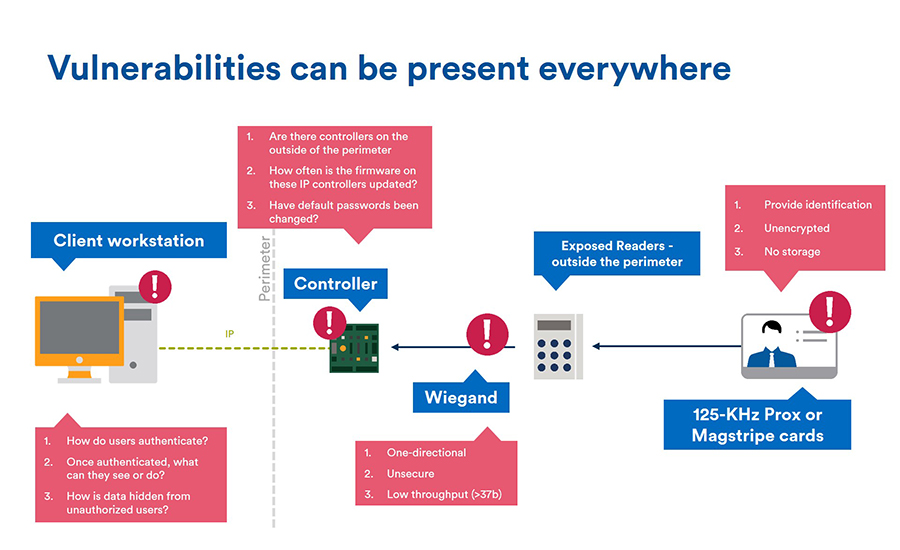
Sensors | Free Full-Text | Applying Access Control Enabled Blockchain (ACE-BC) Framework to Manage Data Security in the CIS System

Cyber security vector illustration concept with characters. Data security, protected access control, privacy data protection. Modern flat style for landing page, web banner, infographics, hero images Stock-Vektorgrafik | Adobe Stock