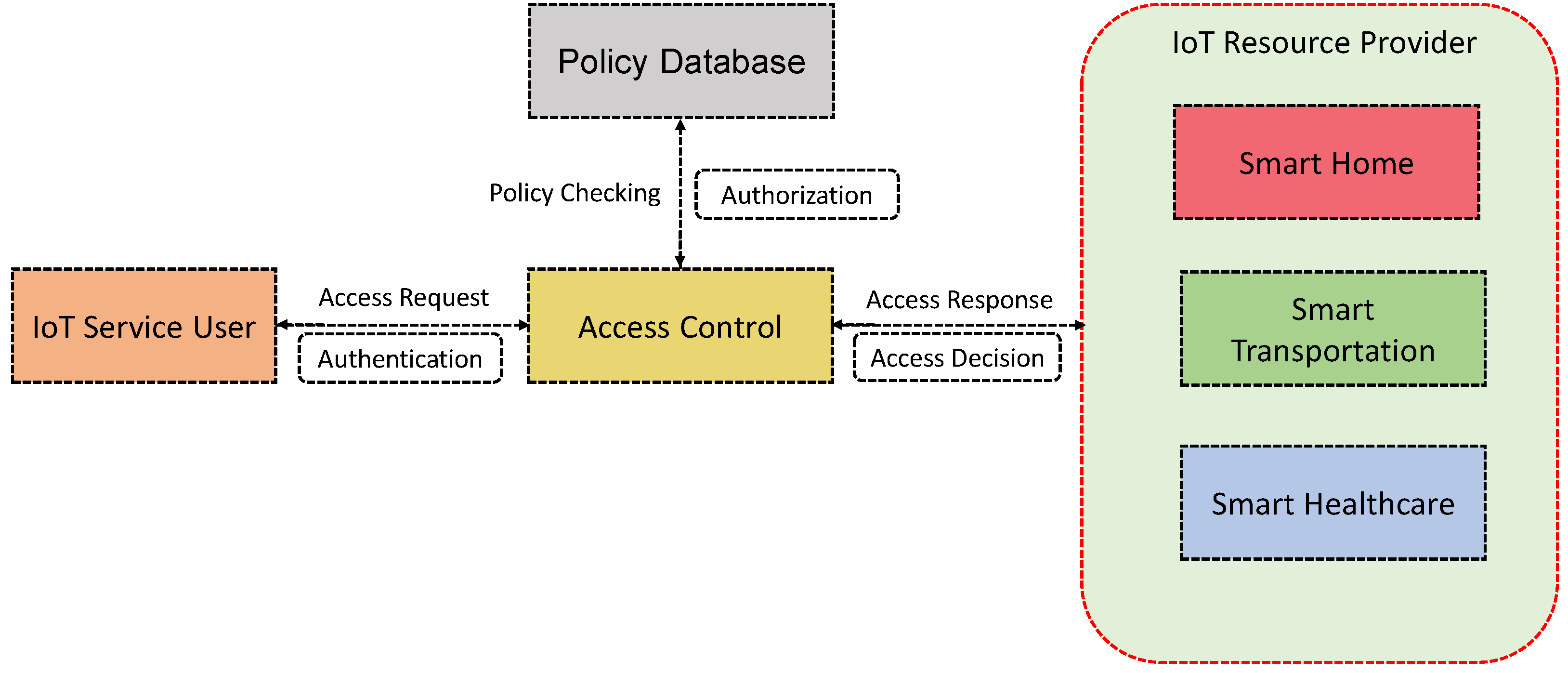
Sensors | Free Full-Text | Protocol-Based and Hybrid Access Control for the IoT: Approaches and Research Opportunities

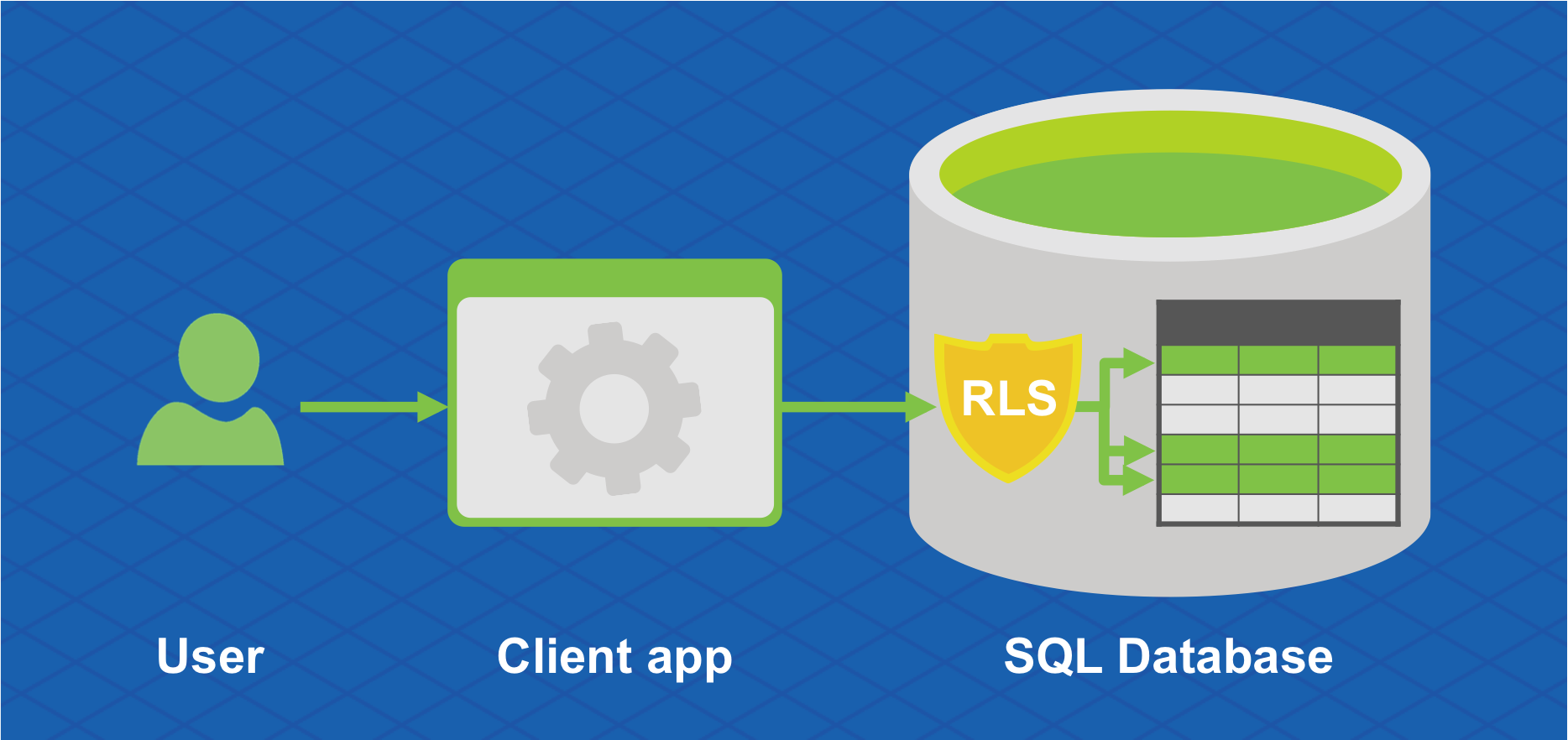
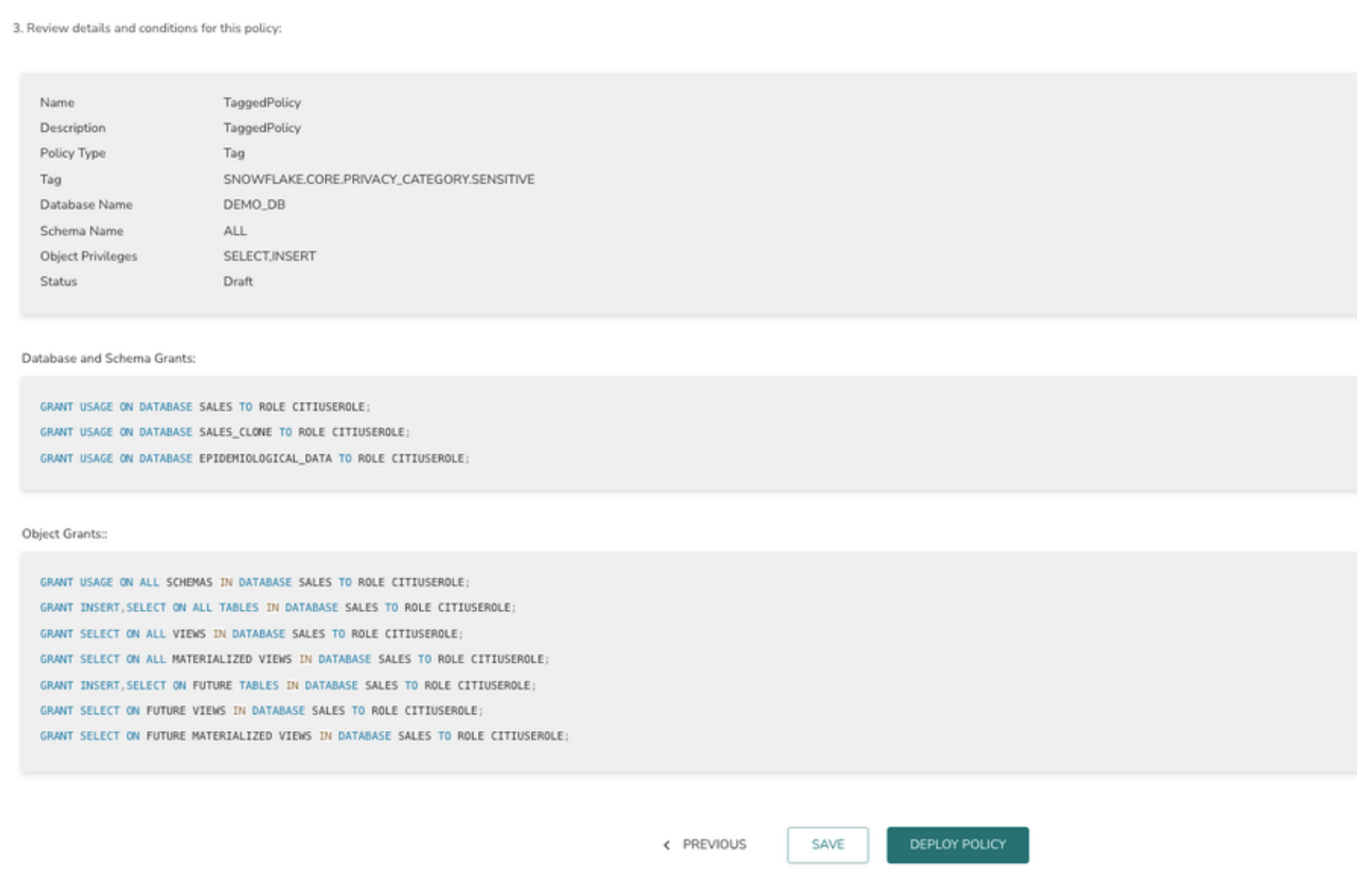
Private Preview: controlling access to Azure SQL at scale with policies in Purview - Microsoft Community Hub

Managing attribute-based access control policies in a unified framework using data warehousing and in-memory database - ScienceDirect

1 Data Access Control, Password Policy and Authentication Methods for Online Bank Md. Mahbubur Rahman Alam B. Sc. (Statistics) Dhaka University M. Sc. - ppt download
GDPR personal data protection and security, vector icons. GDPR General Data Protection Regulation on information database access, digital security, legal or financial personal data confidential policy Stock-Vektorgrafik | Adobe Stock
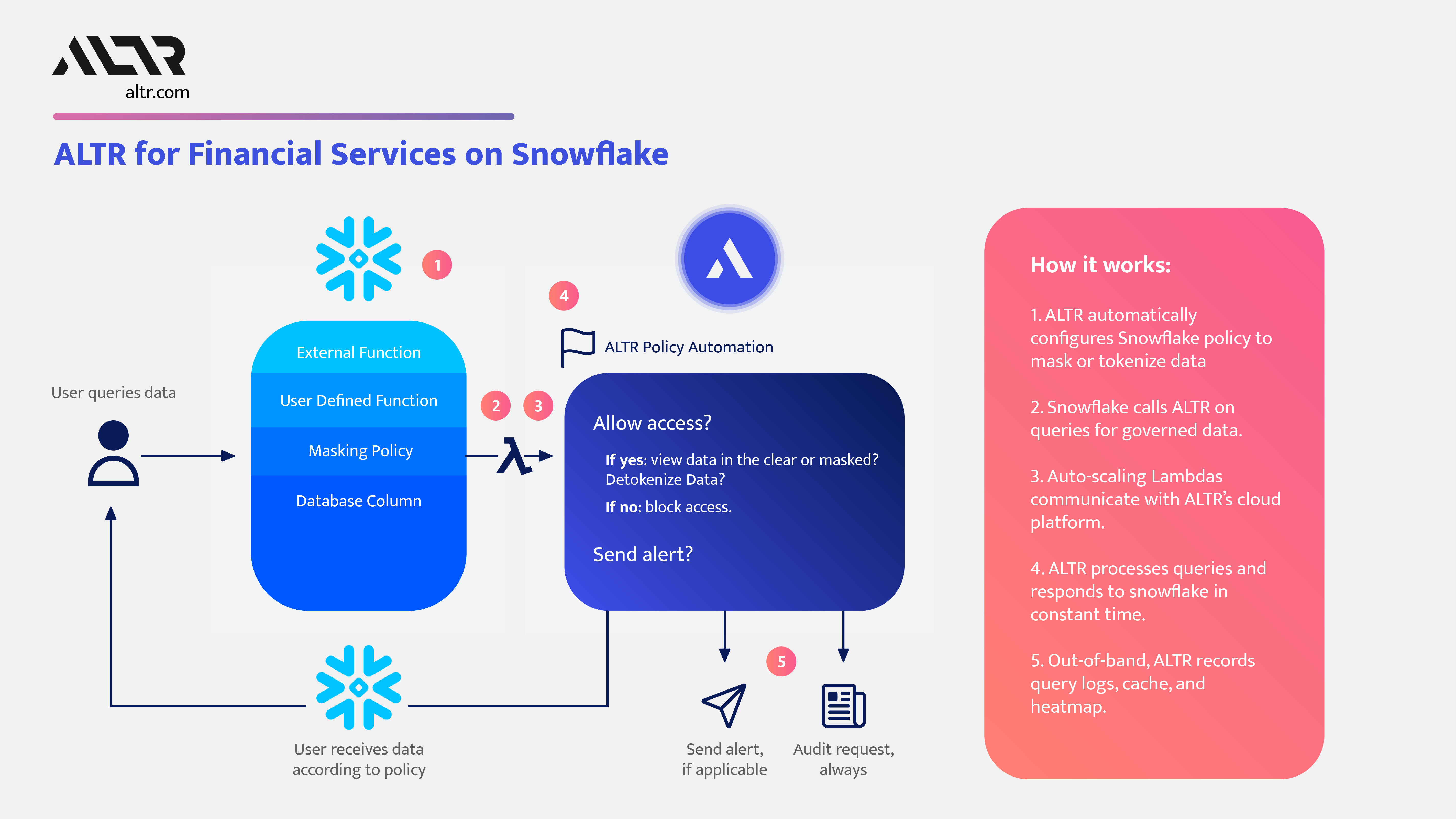
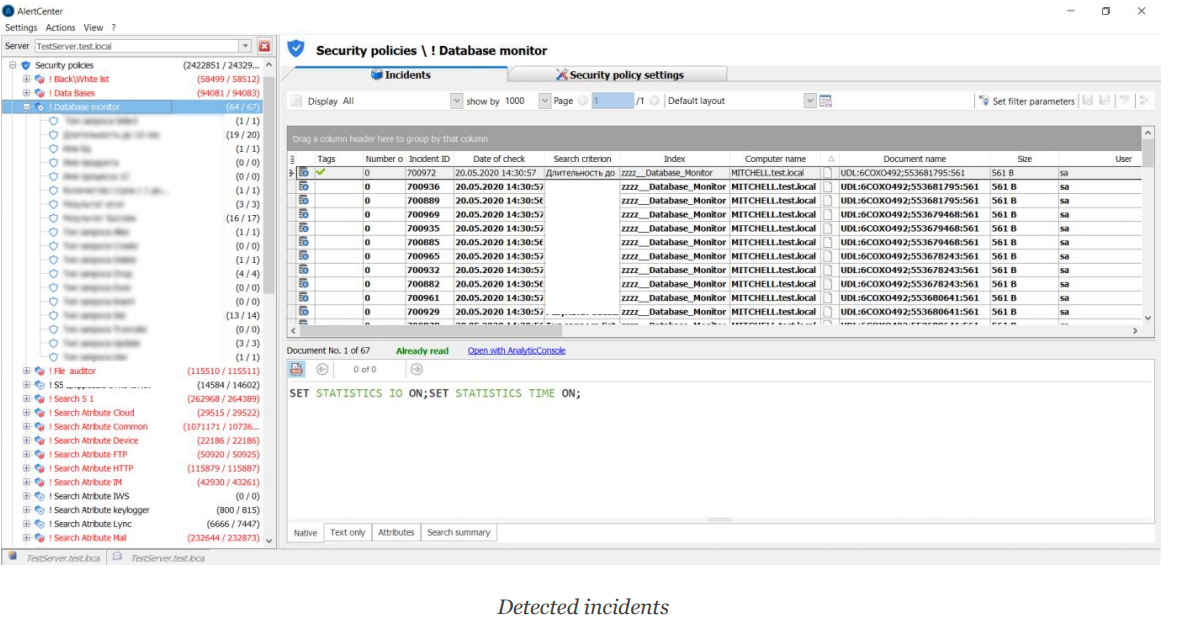

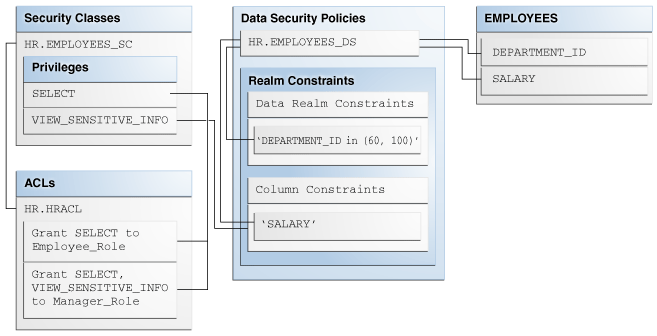
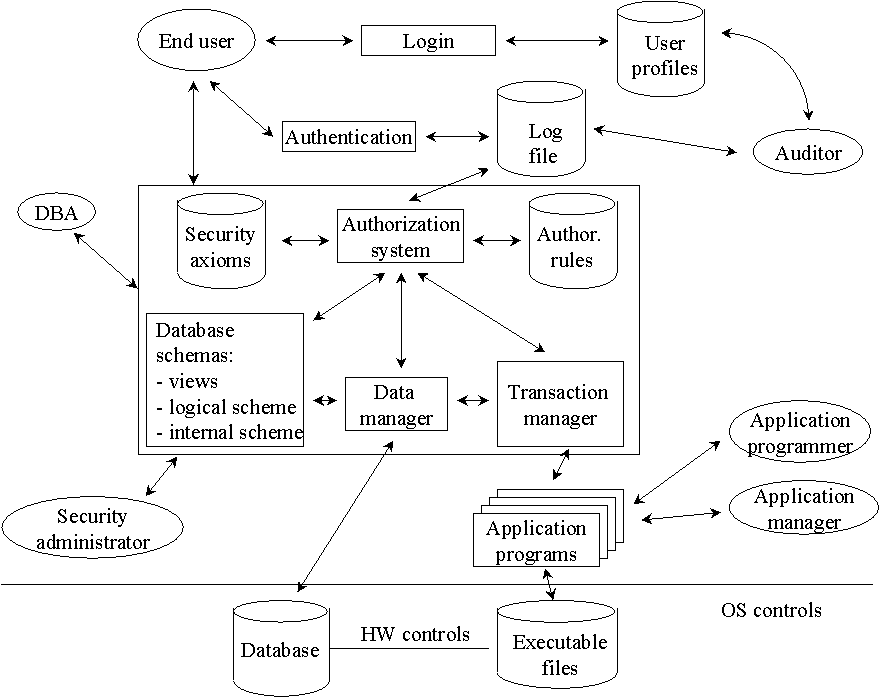
![PDF] Database Access Control Policies | Semantic Scholar PDF] Database Access Control Policies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bfd4c8c86b964e3843b853d311181a12267c5633/2-Figure1-1.png)
![PDF] Database Access Control Policies | Semantic Scholar PDF] Database Access Control Policies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bfd4c8c86b964e3843b853d311181a12267c5633/4-Figure5-1.png)
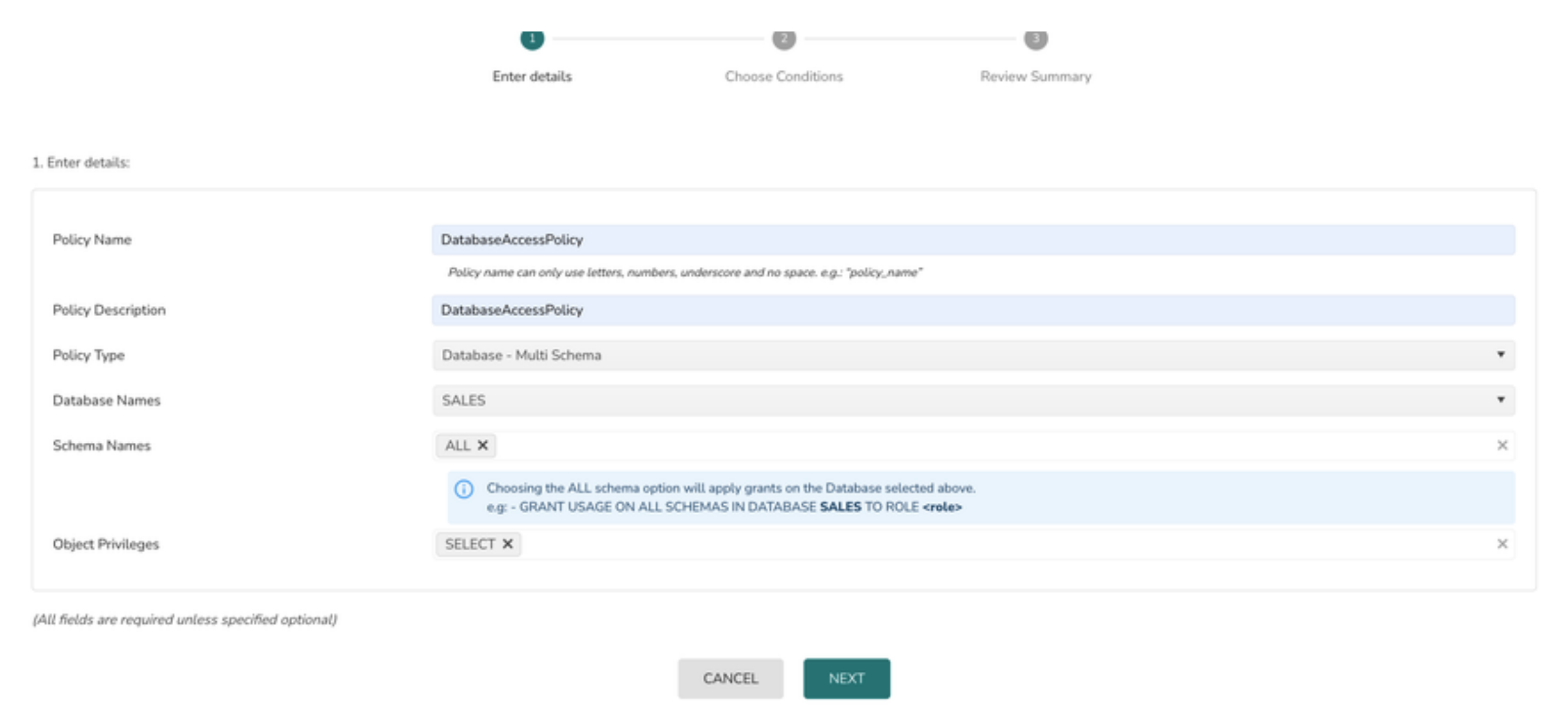

![PDF] Database Access Control Policies | Semantic Scholar PDF] Database Access Control Policies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bfd4c8c86b964e3843b853d311181a12267c5633/3-Figure4-1.png)