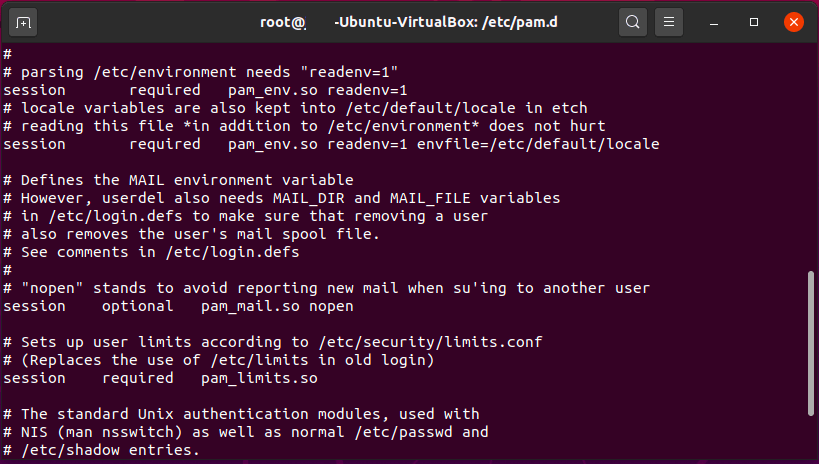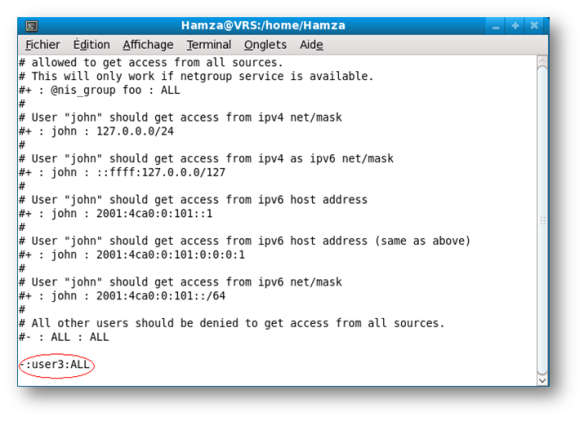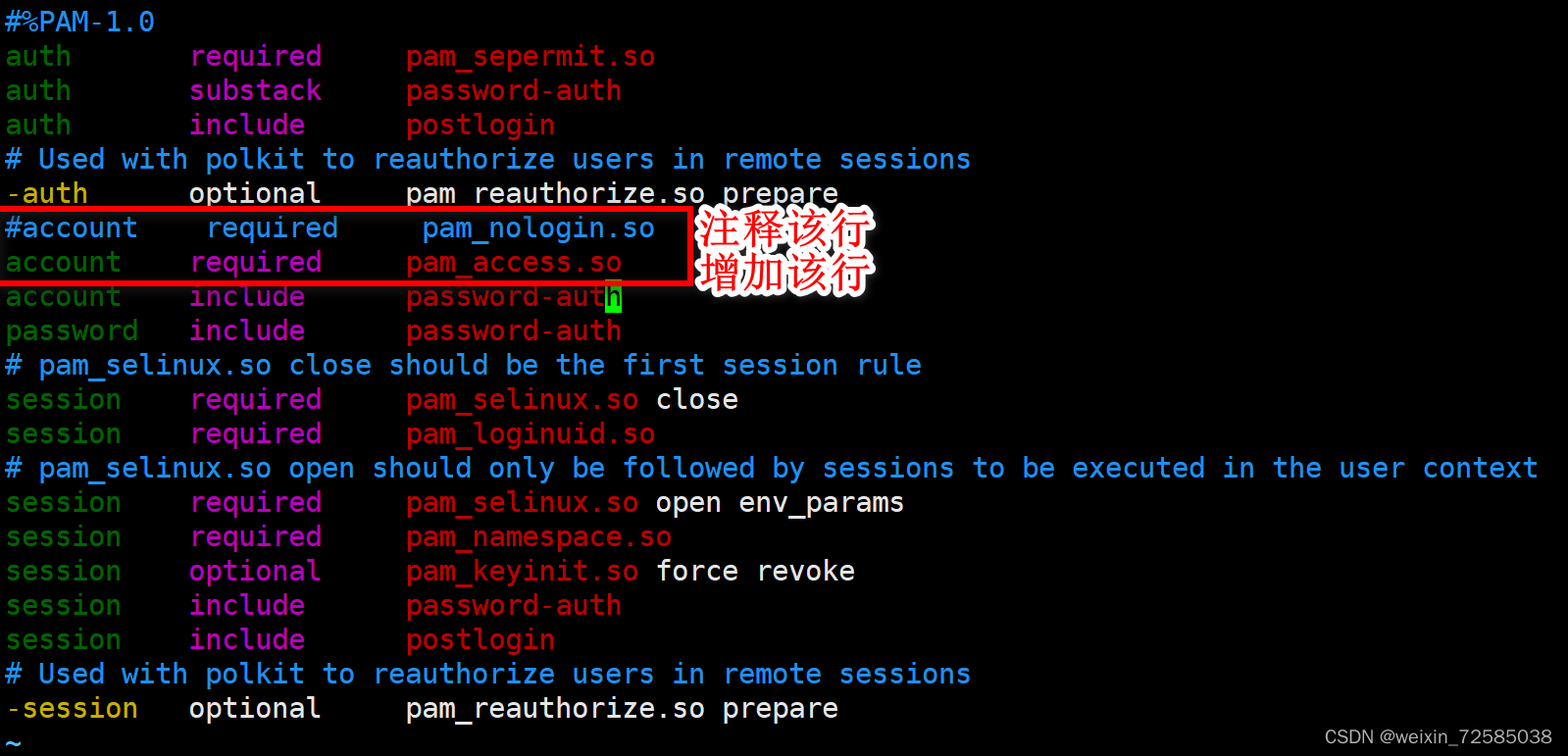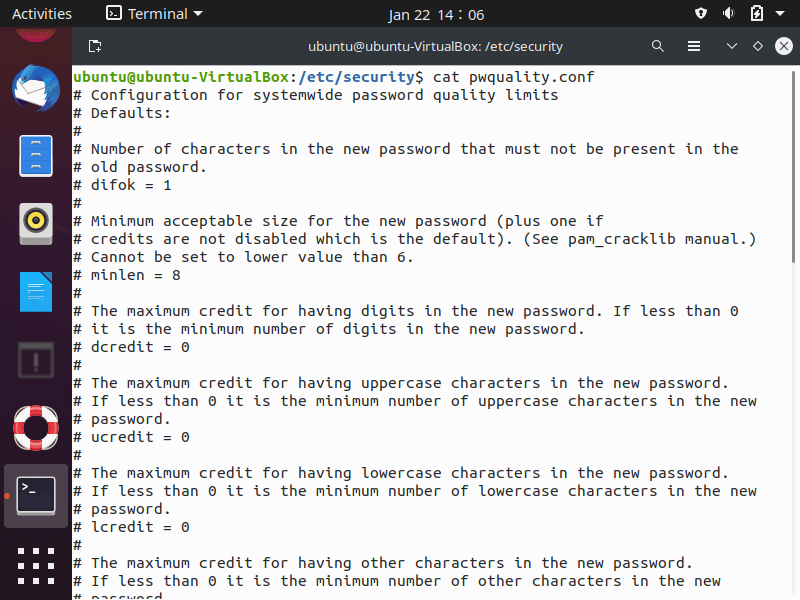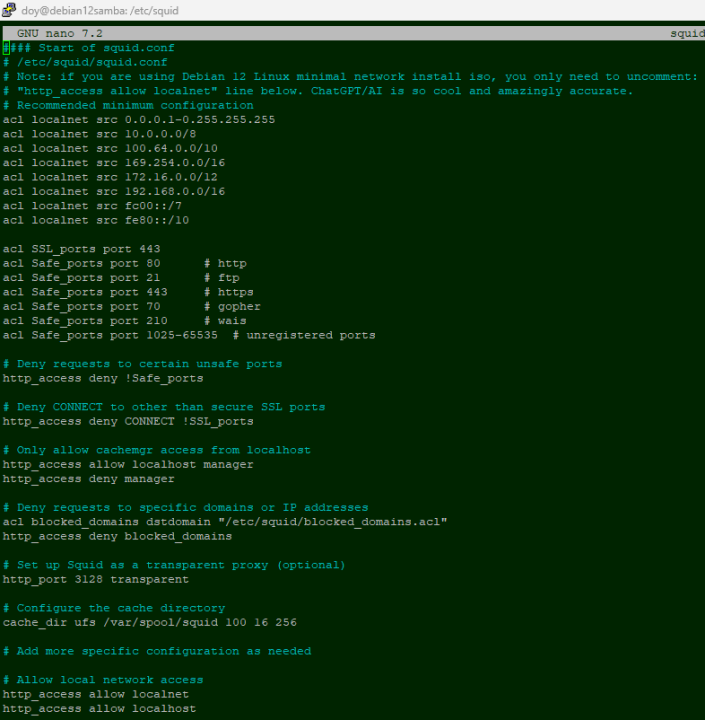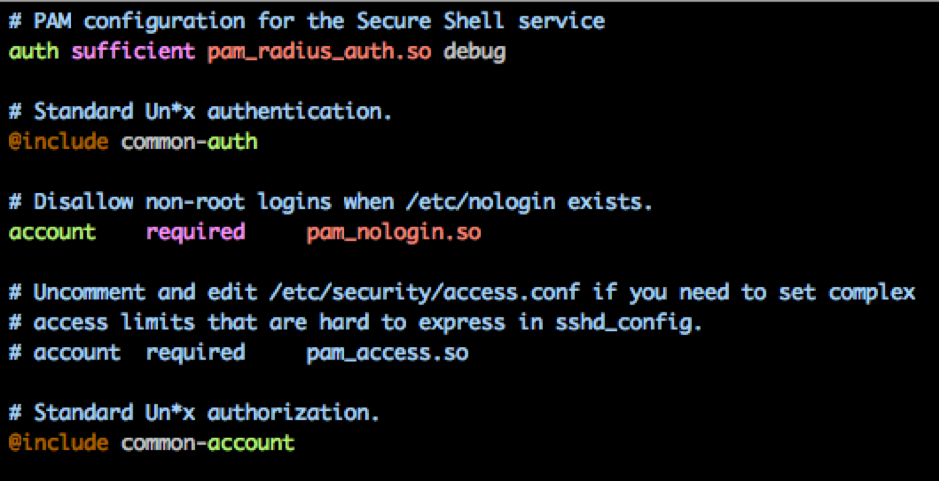
Use ForgeRock Access Manager to provide MFA to Linux using PAM Radius - Integrations - ForgeRock Community

active directory - Local groups mapped to AD users via groups.conf working - but only with ssh login - Server Fault
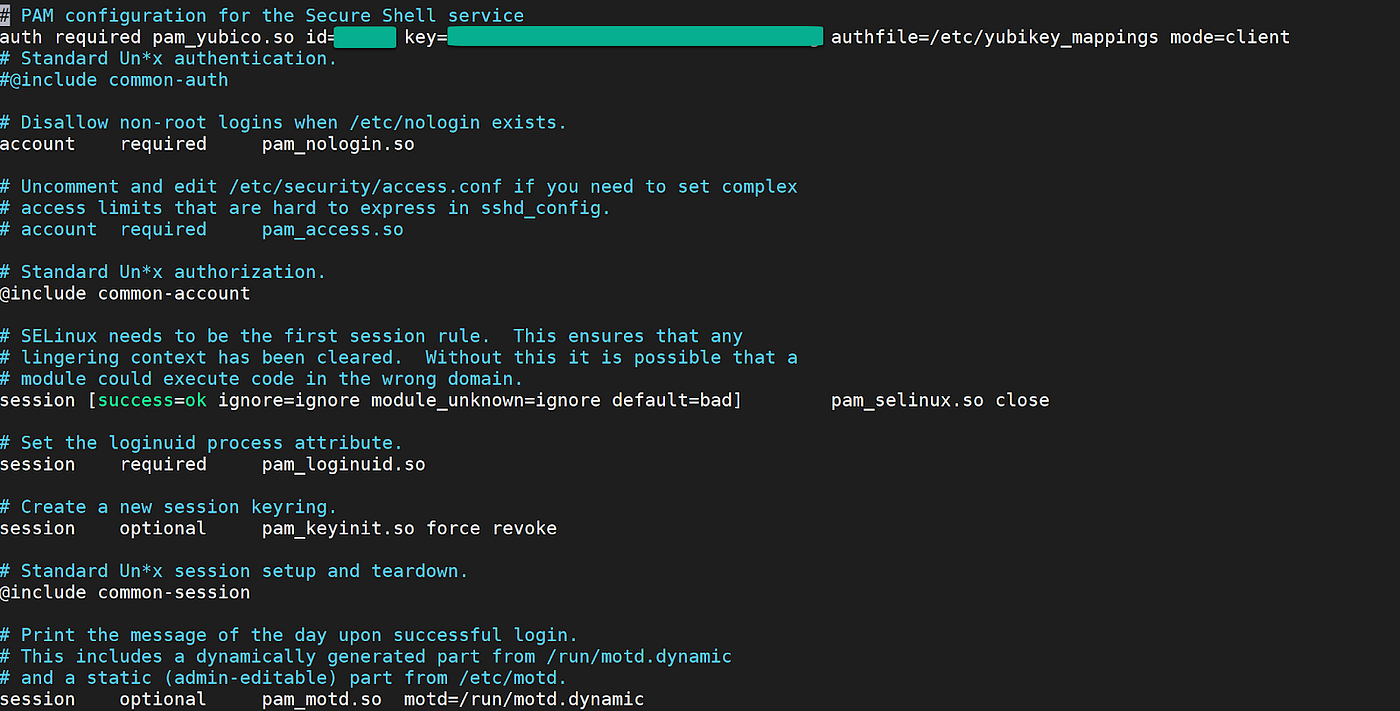
Improving Validator Security and using HSM Module for 2FA | by Chainode Tech | Chainode Tech | Medium

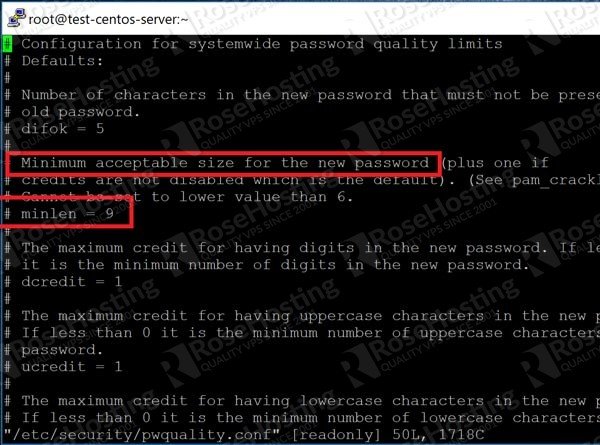
Crafting Malicious Pluggable Authentication Modules for Persistence, Privilege Escalation, and Lateral Movement | RoseSecurity Research