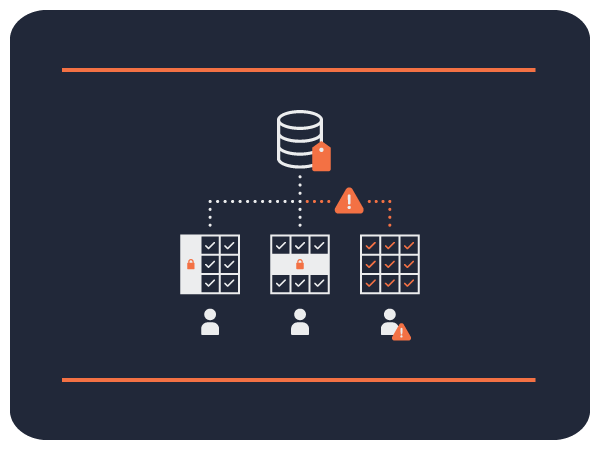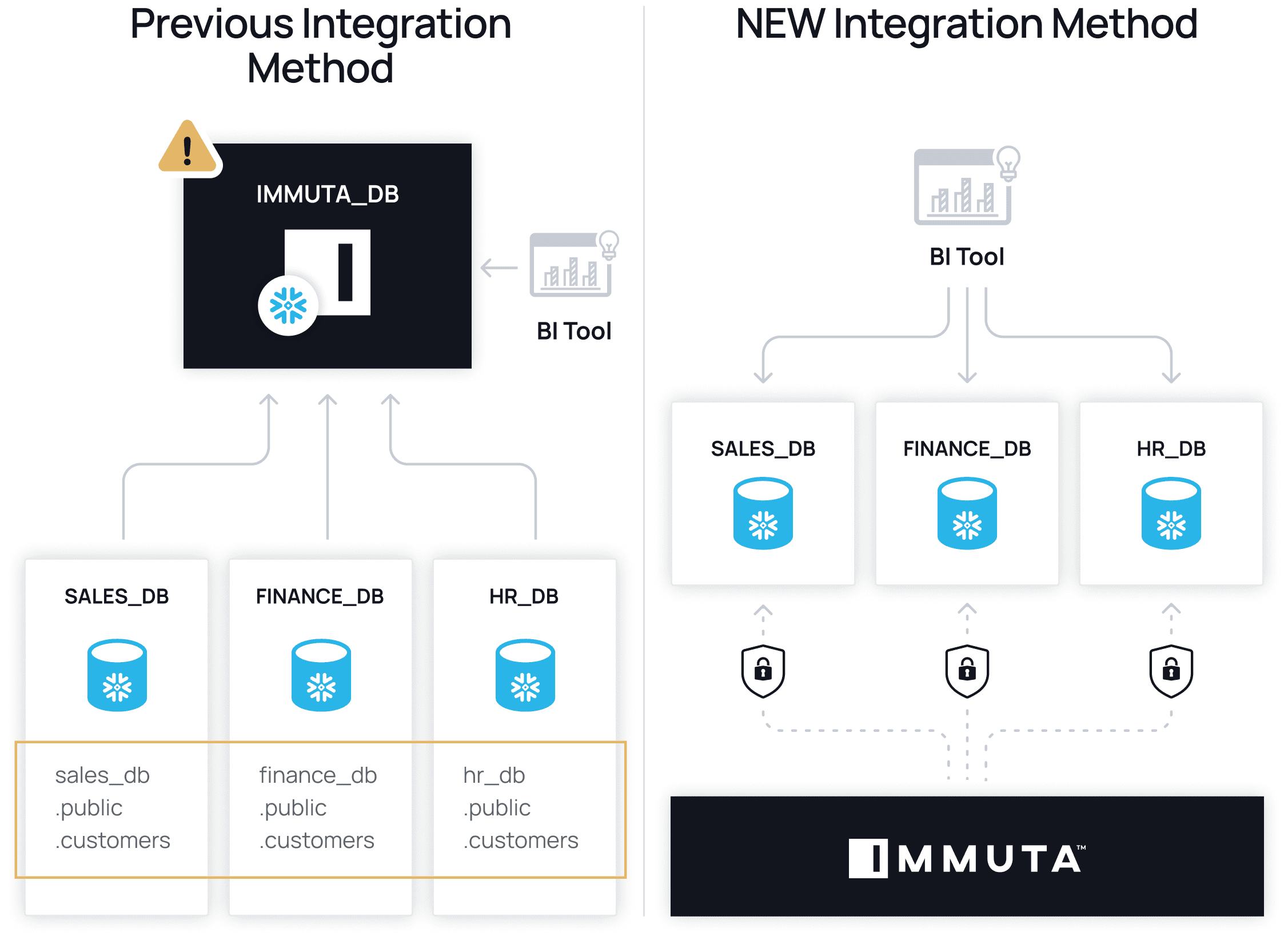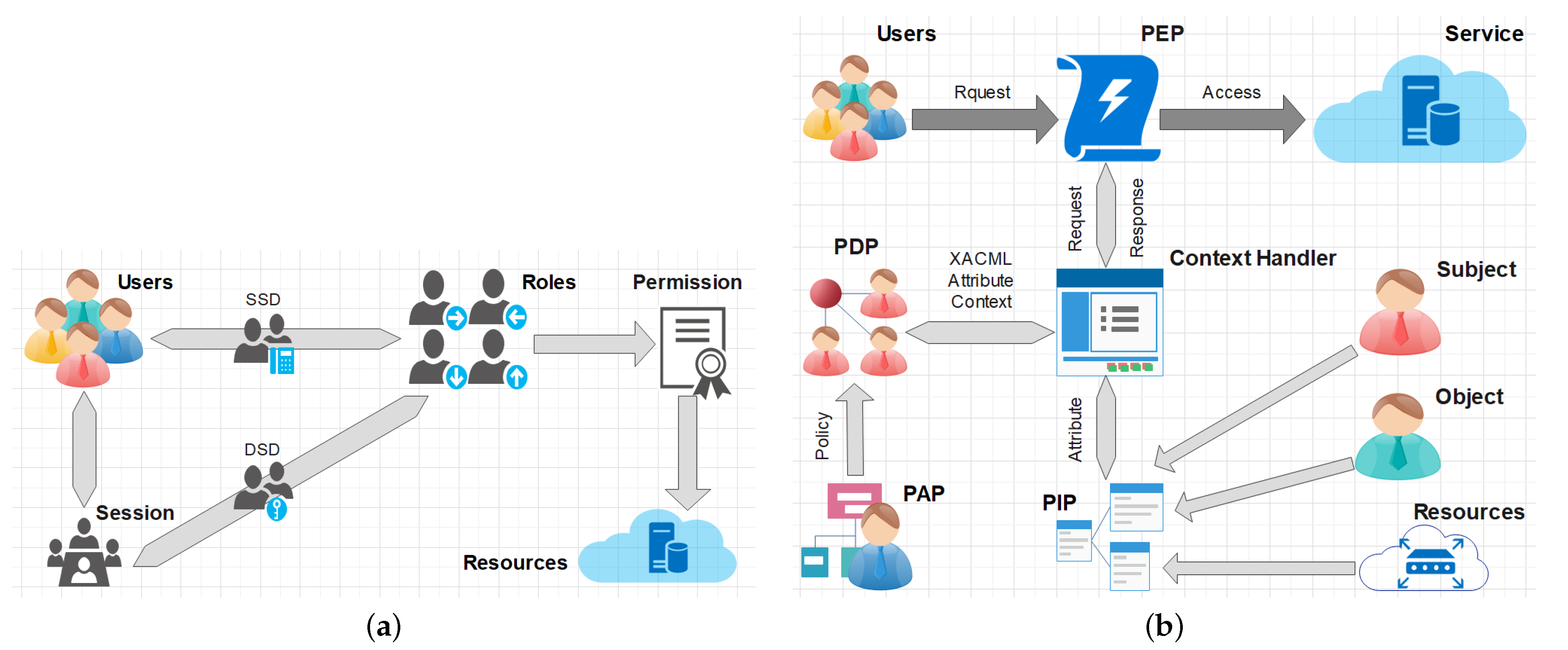
Electronics | Free Full-Text | Fine Grained Access Control Based on Smart Contract for Edge Computing
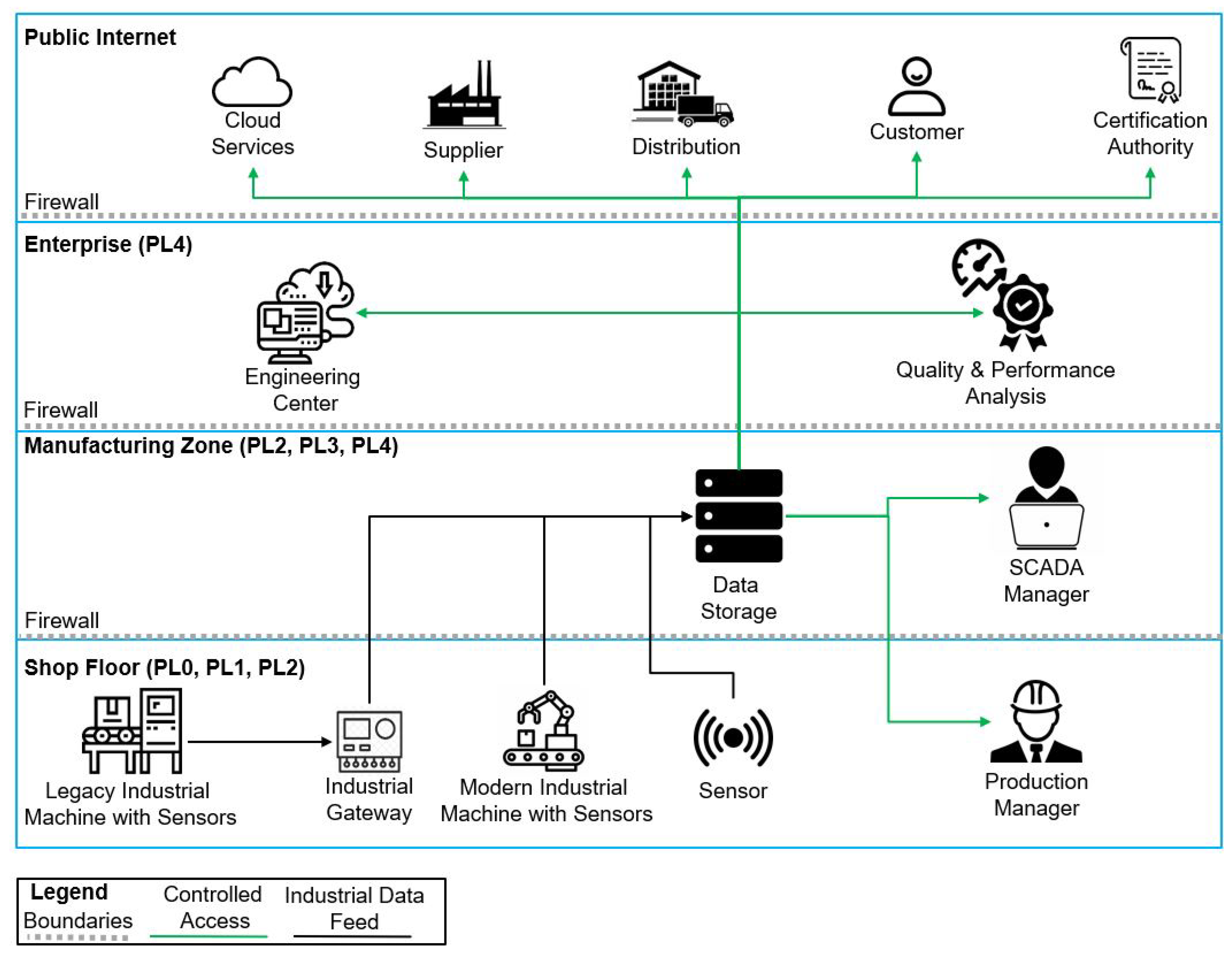
Electronics | Free Full-Text | Fine-Grained Access Control with User Revocation in Smart Manufacturing

a public access domain with fine-grained access control enabled, an access policy that doesn't use IAM principals,… | Access control, How to protect yourself, Users

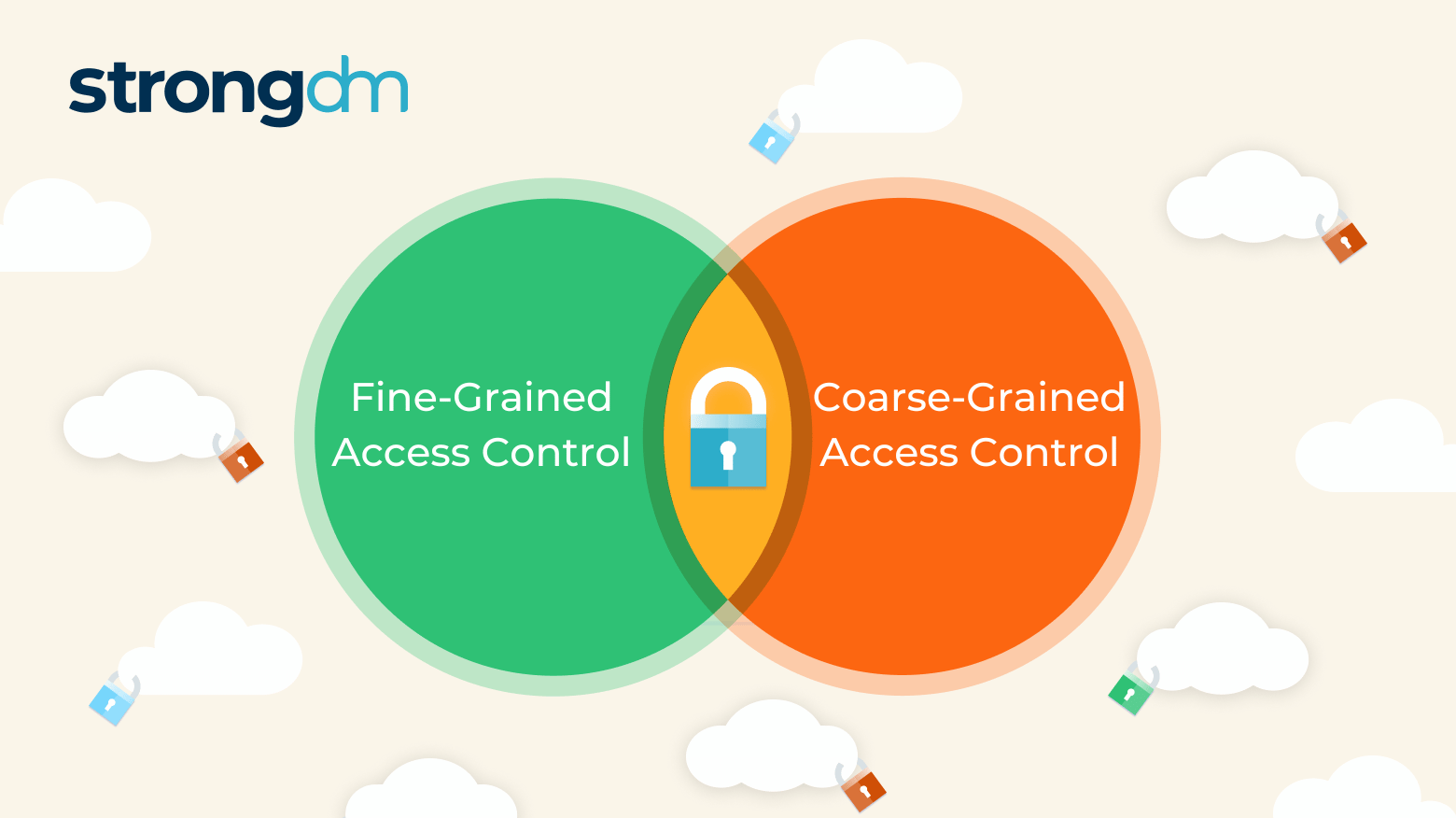
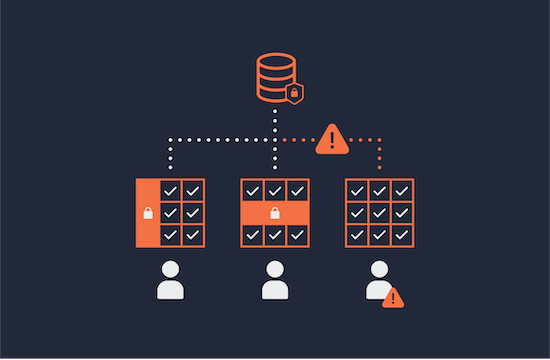
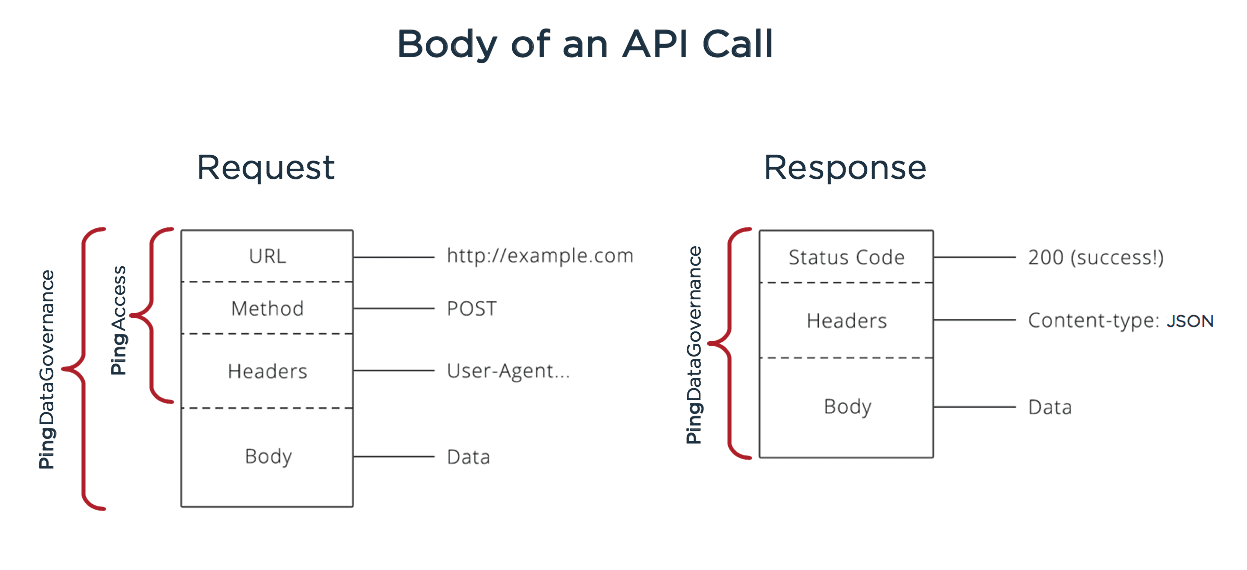
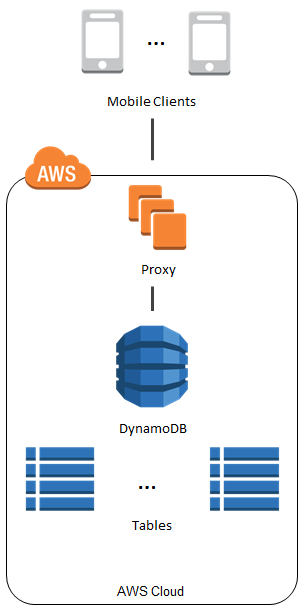

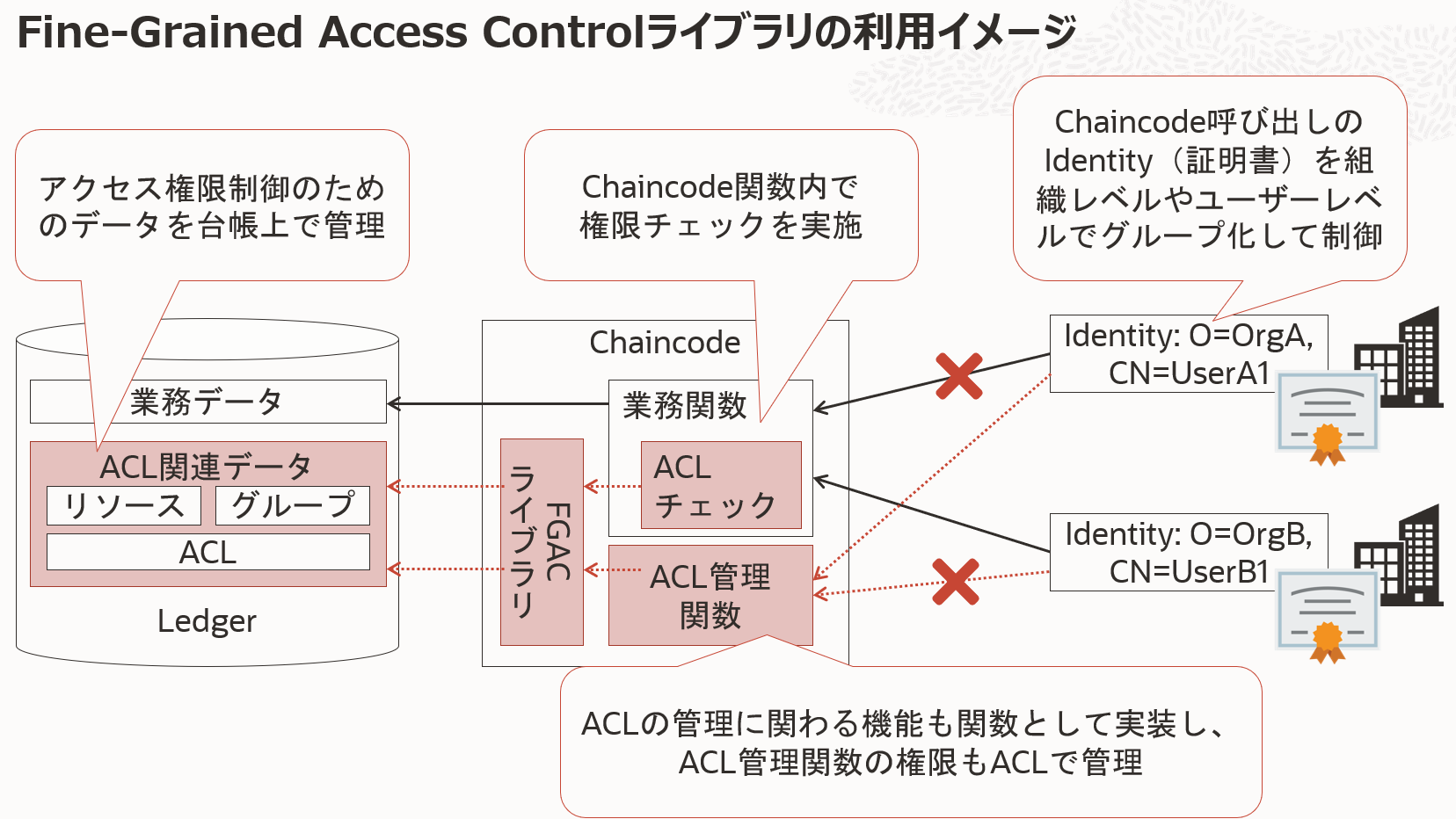
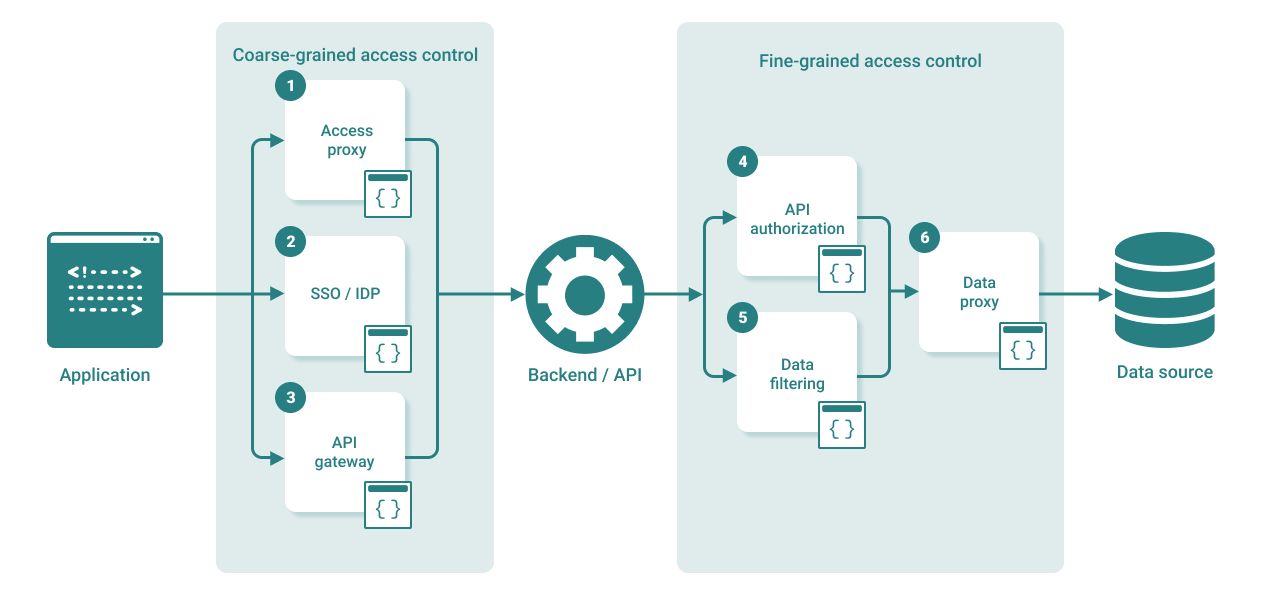
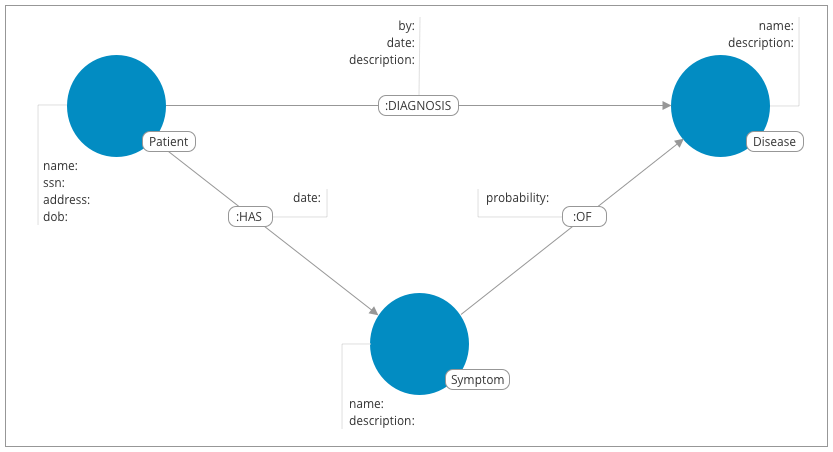

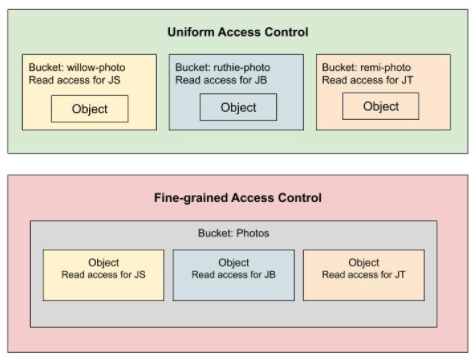




![Chapter 8] Deploying Fine-Grained Access Control Chapter 8] Deploying Fine-Grained Access Control](https://docstore.mik.ua/orelly/oracle/guide8i/figs/o8if.0801.gif)