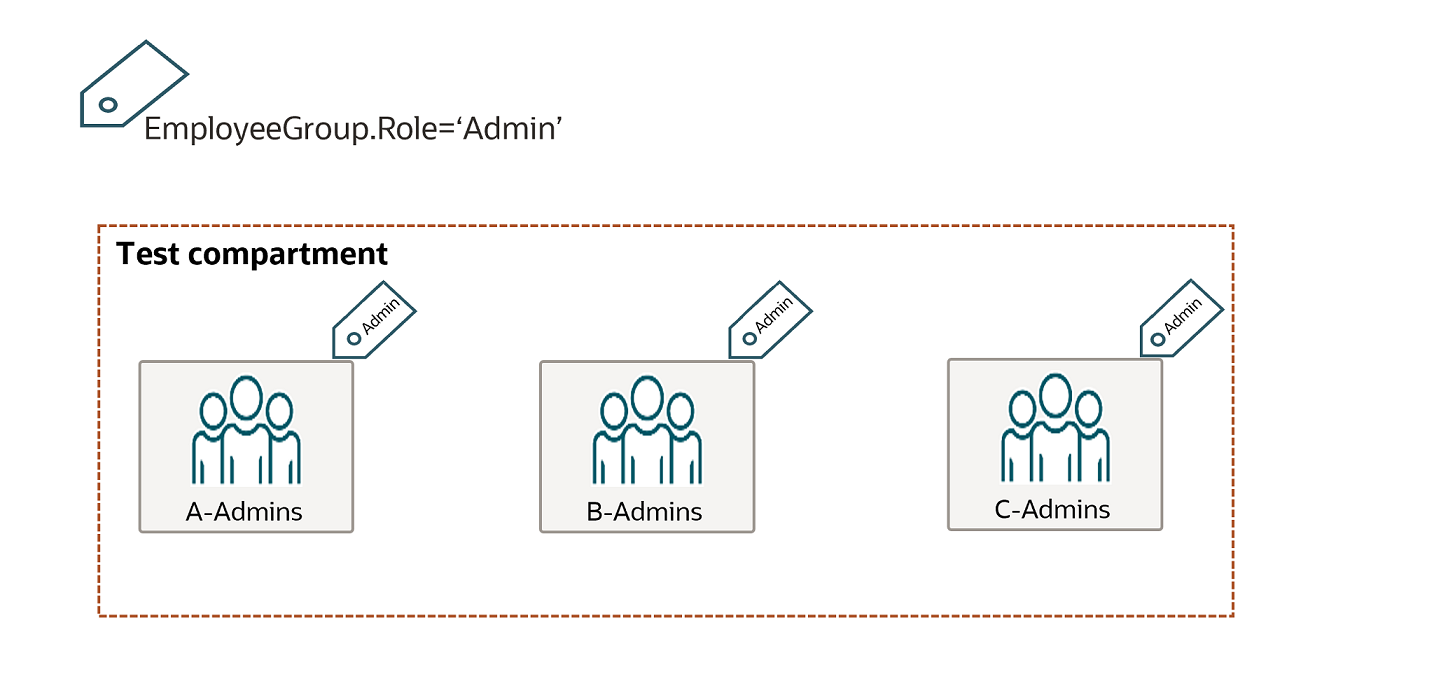
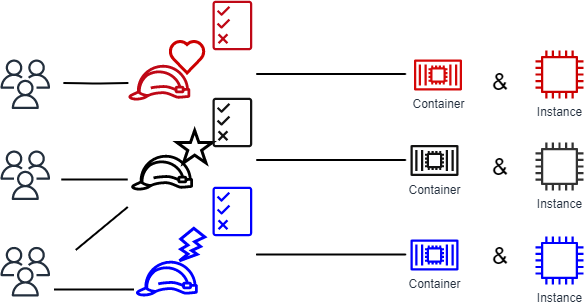
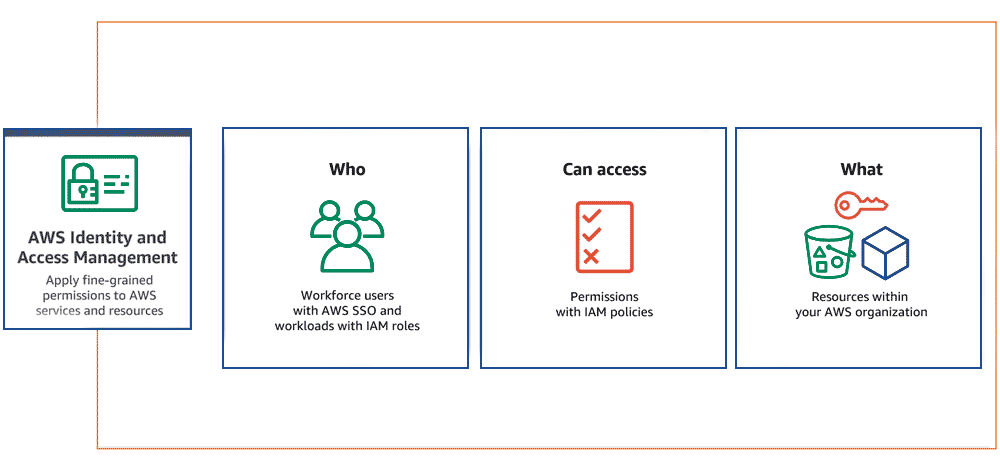
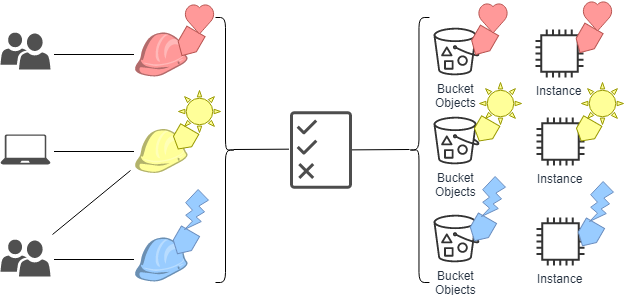
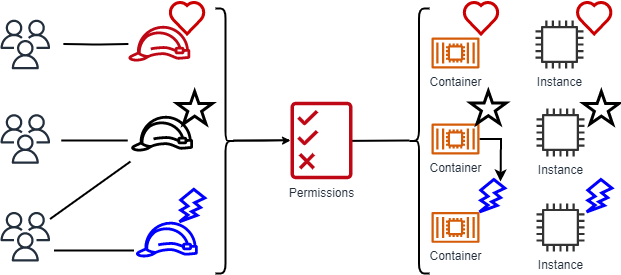
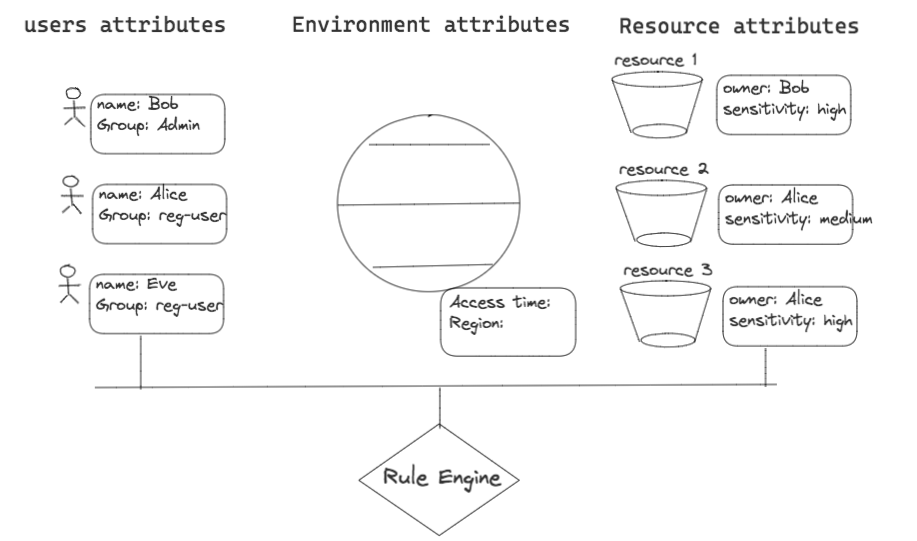
Use attribute-based access control with AD FS to simplify IAM permissions management | AWS Security Blog
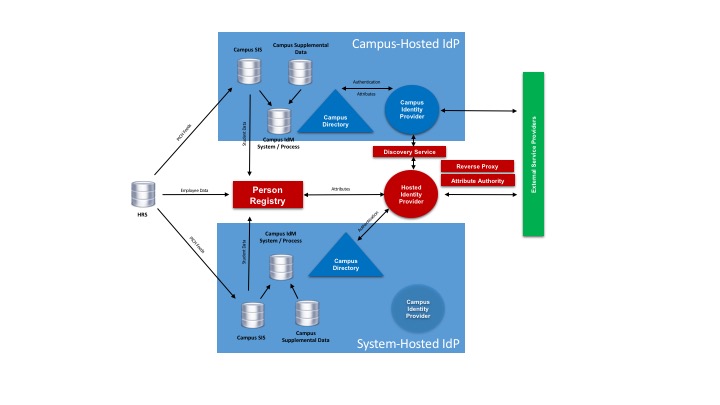
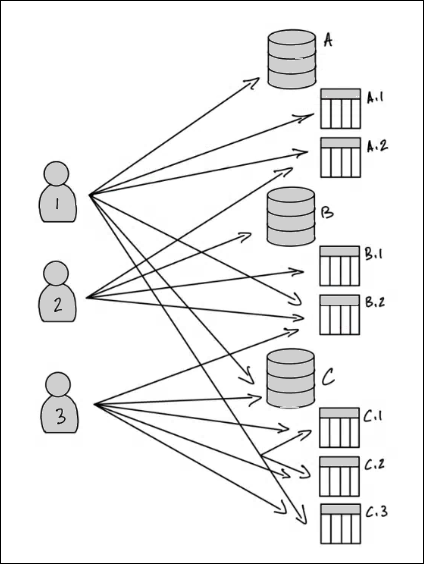
Identity and Access Management Technical Advisory Group (IAM-TAG) | Systemwide Information Technology
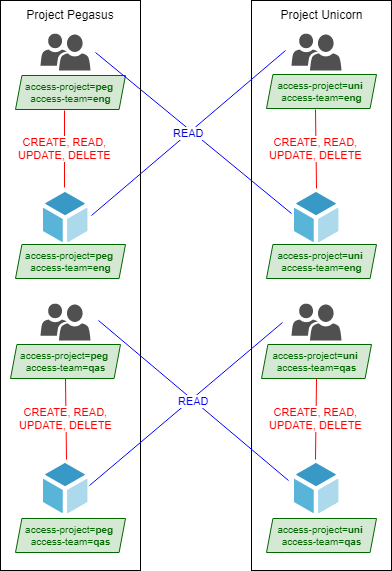
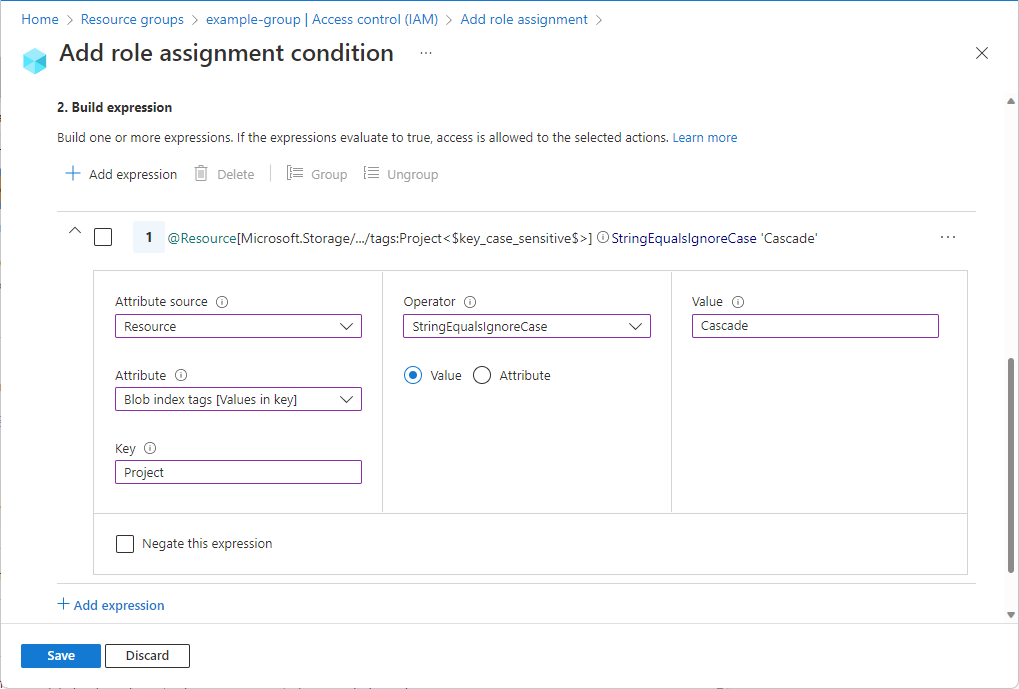
IAM tutorial: Define permissions to access AWS resources based on tags - AWS Identity and Access Management

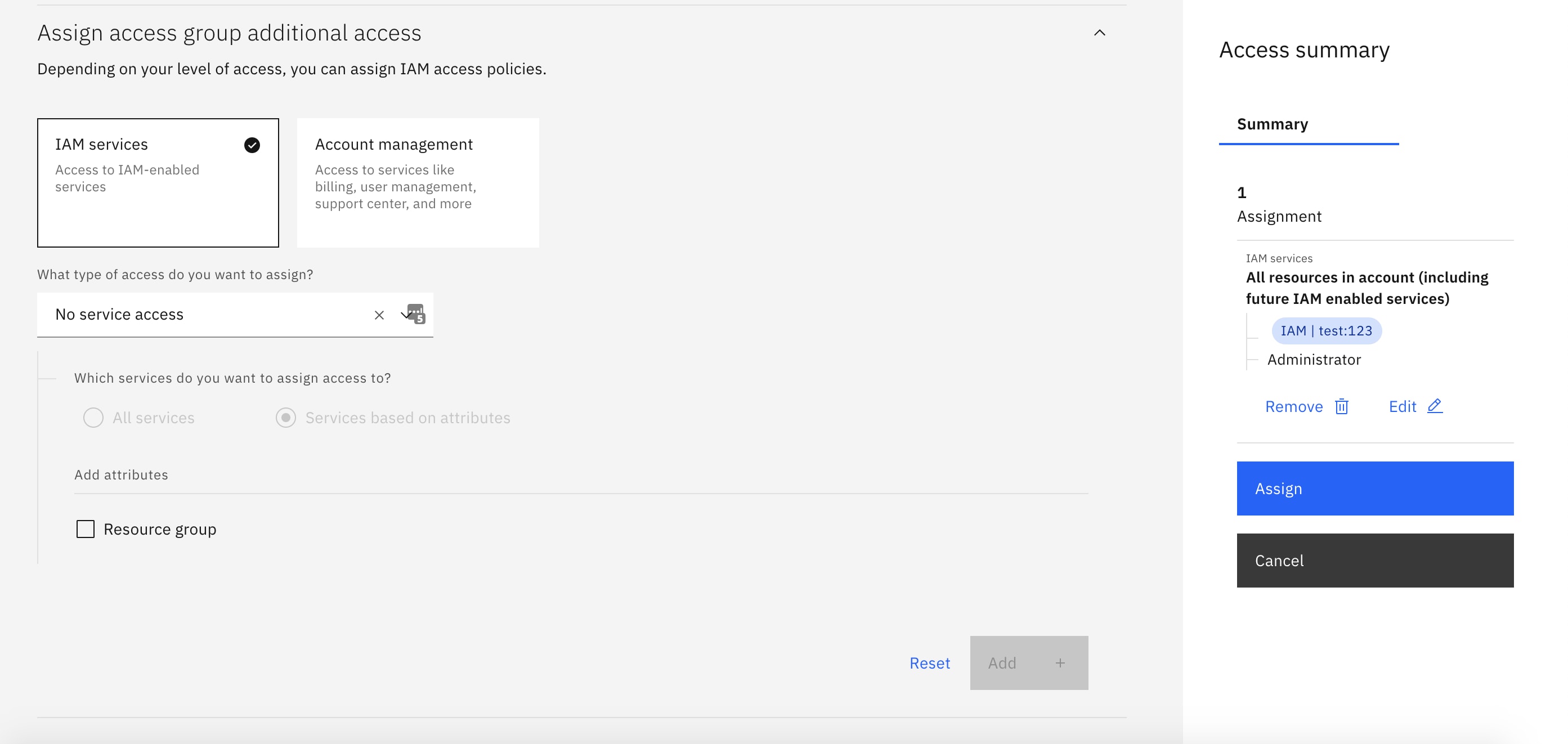
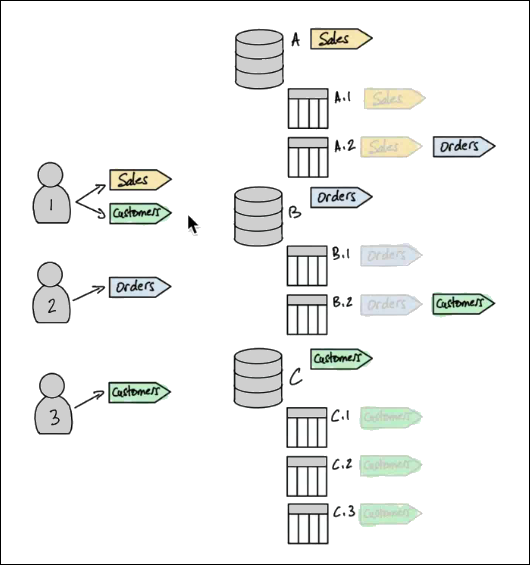
How we use LakeFormation to control access to our data lake? | by Amin Ullah | Funding Circle | Medium