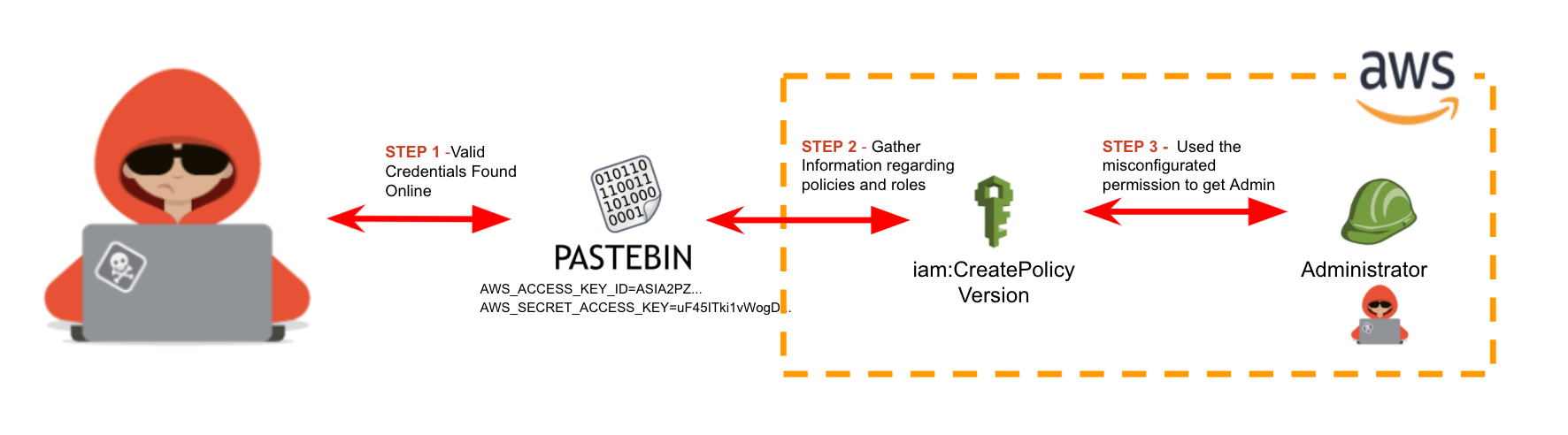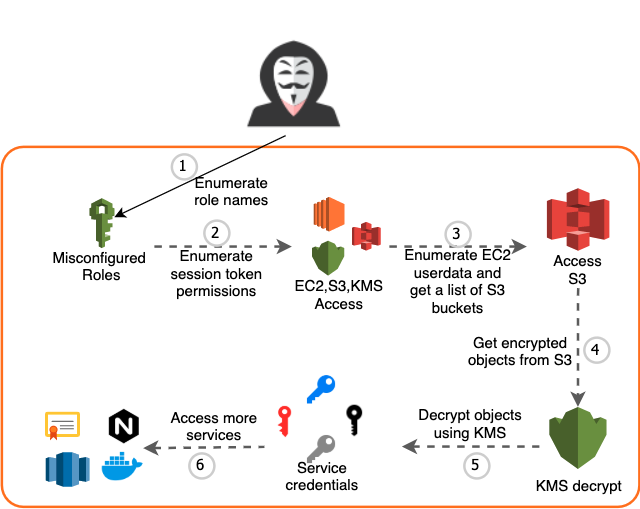
Unit 42 Cloud Threat Report: Misconfigured IAM Roles Lead to Thousands of Compromised Cloud Workloads
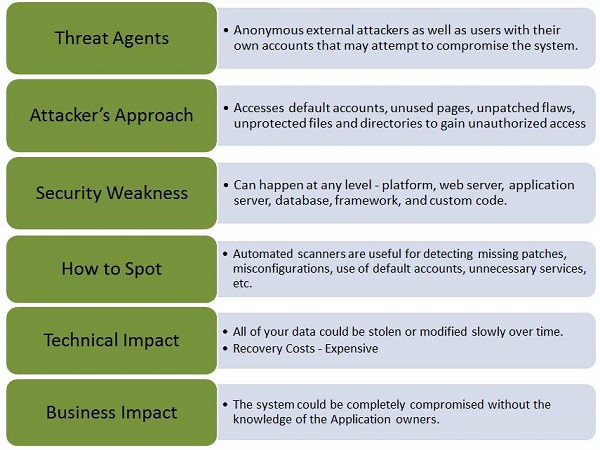
How to Catch Broken Access Control Security Vulnerabilities in Code Review Part 2 | PullRequest Blog
What is a security misconfiguration? | Preventing misconfigurations with ManageEngine Vulnerability Manager Plus