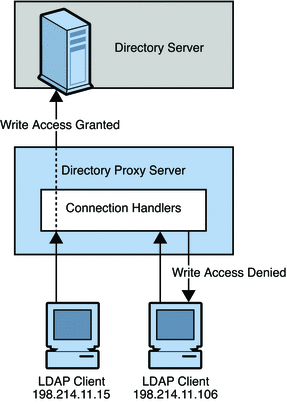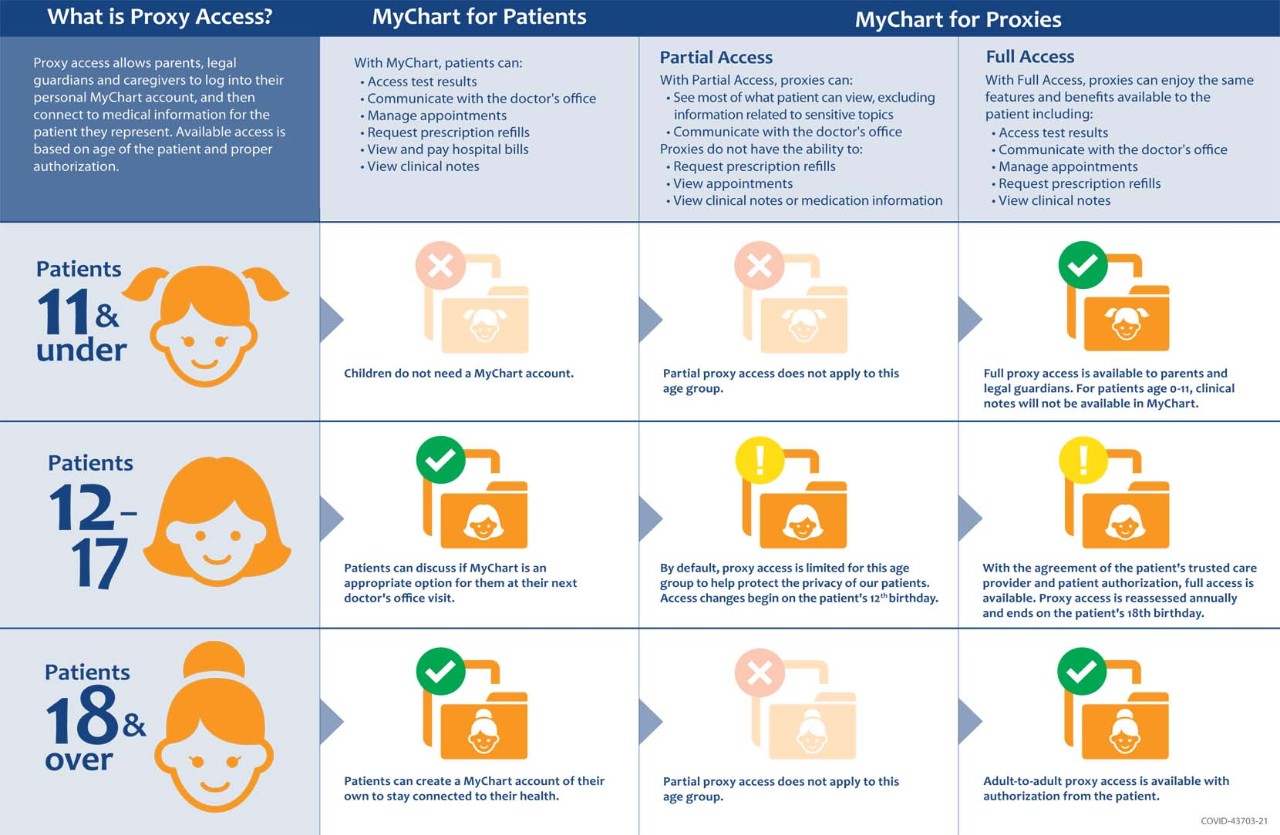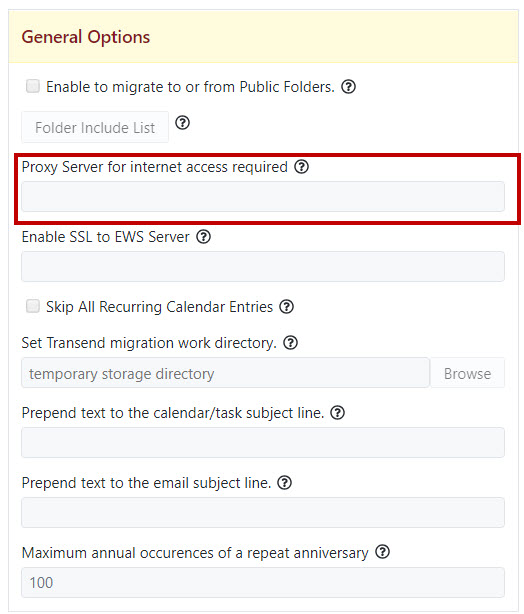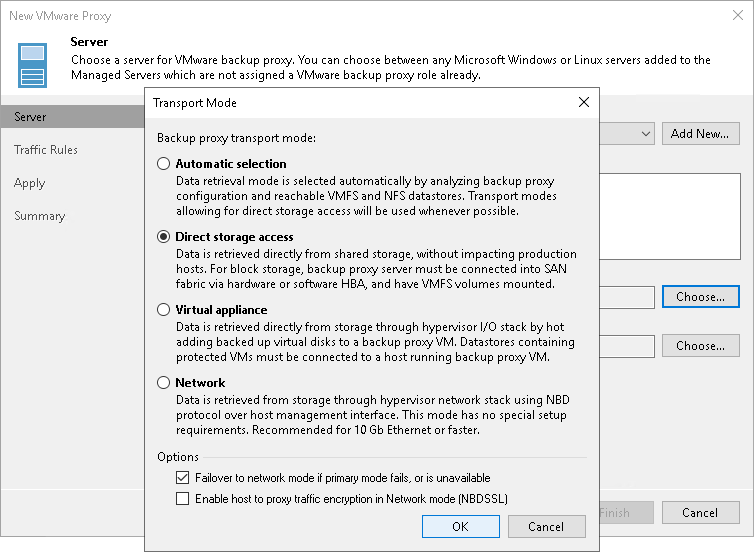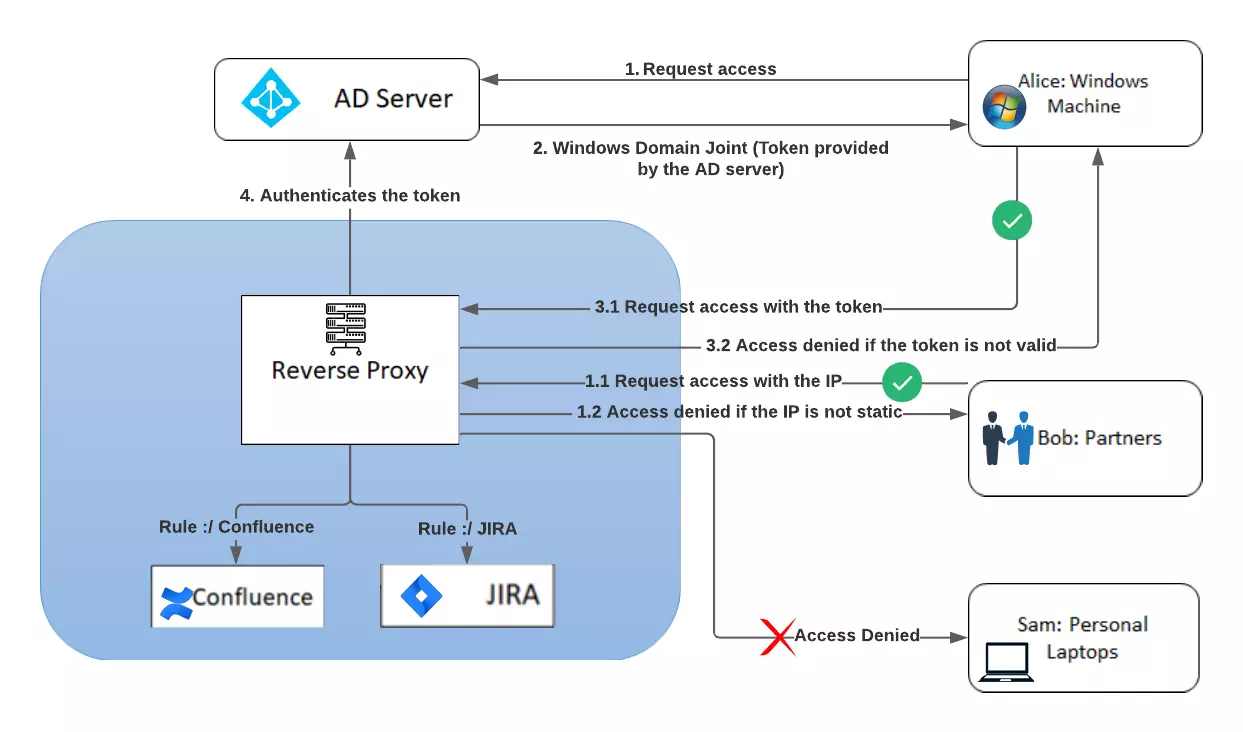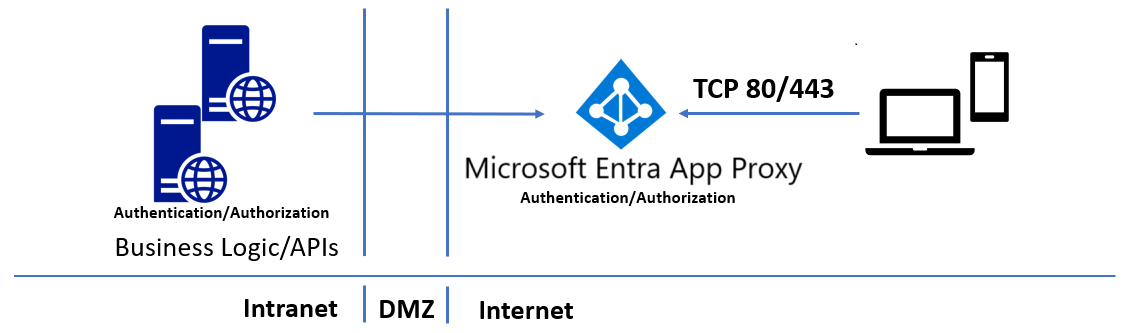
Zugriff auf die lokale Anwendungsprogrammierschnittstelle (API) mit dem Microsoft Entra-Anwendungsproxy - Microsoft Entra ID | Microsoft Learn
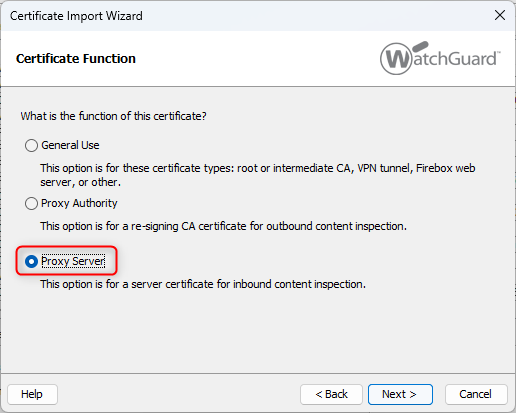
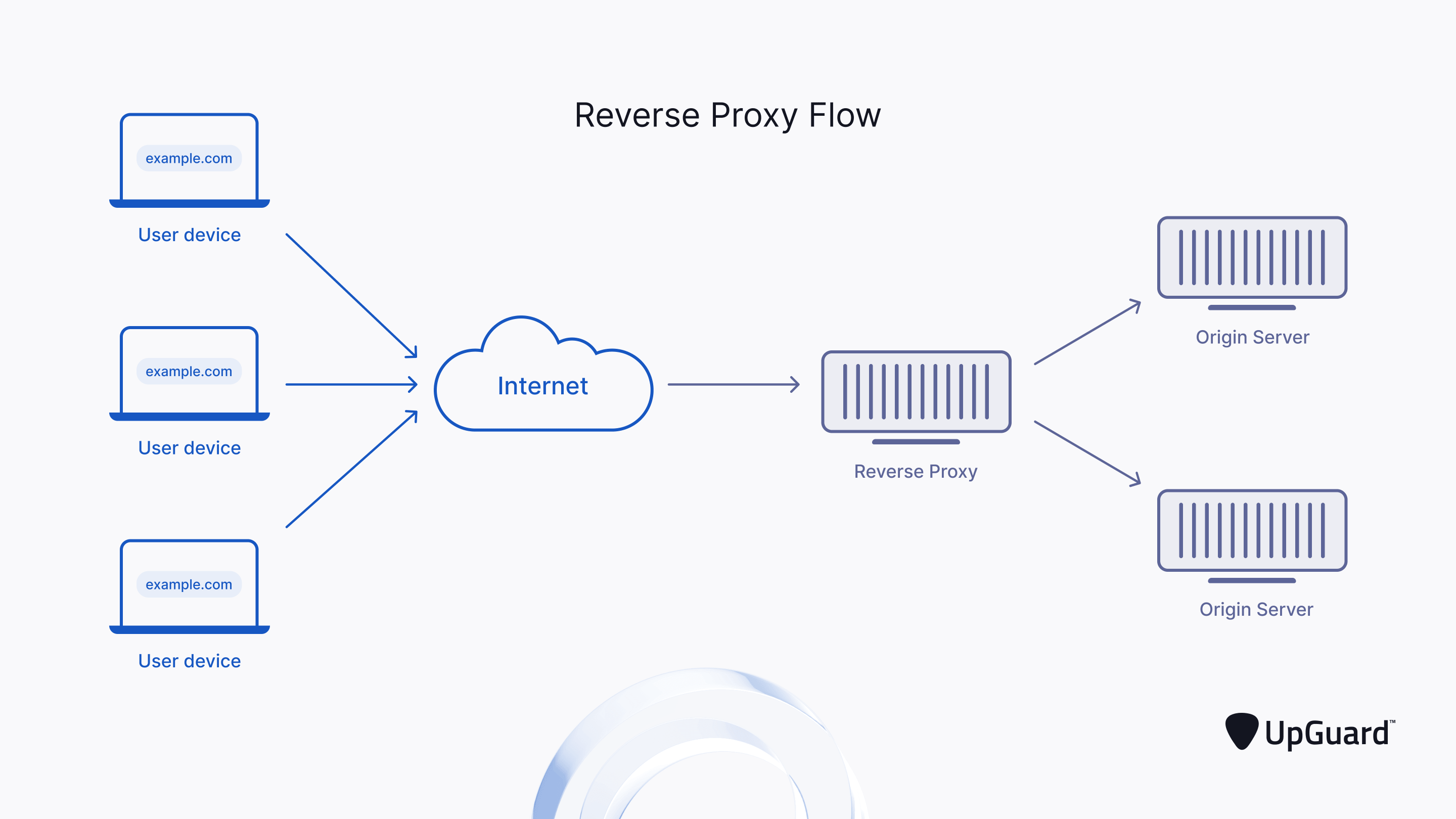
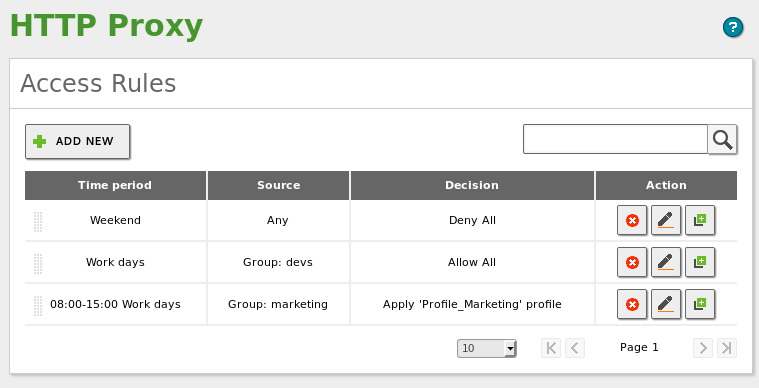
HOWTO: Exchange Reverse Proxy mit HTTPS Content Inspection (Ohne Access Portal) - BOC IT-Security GmbH

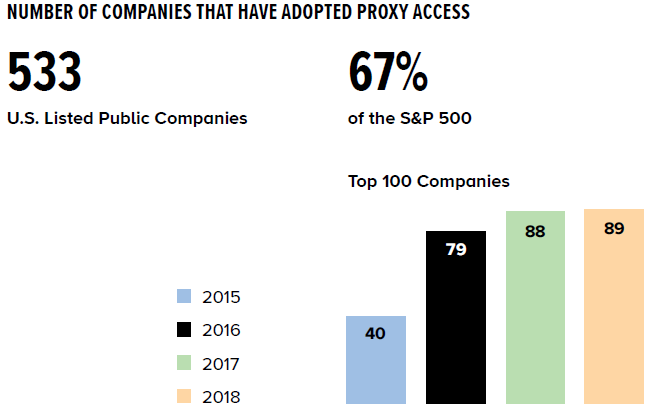
Network infrastructure: a) proxy managed by the access provider; b)... | Download Scientific Diagram

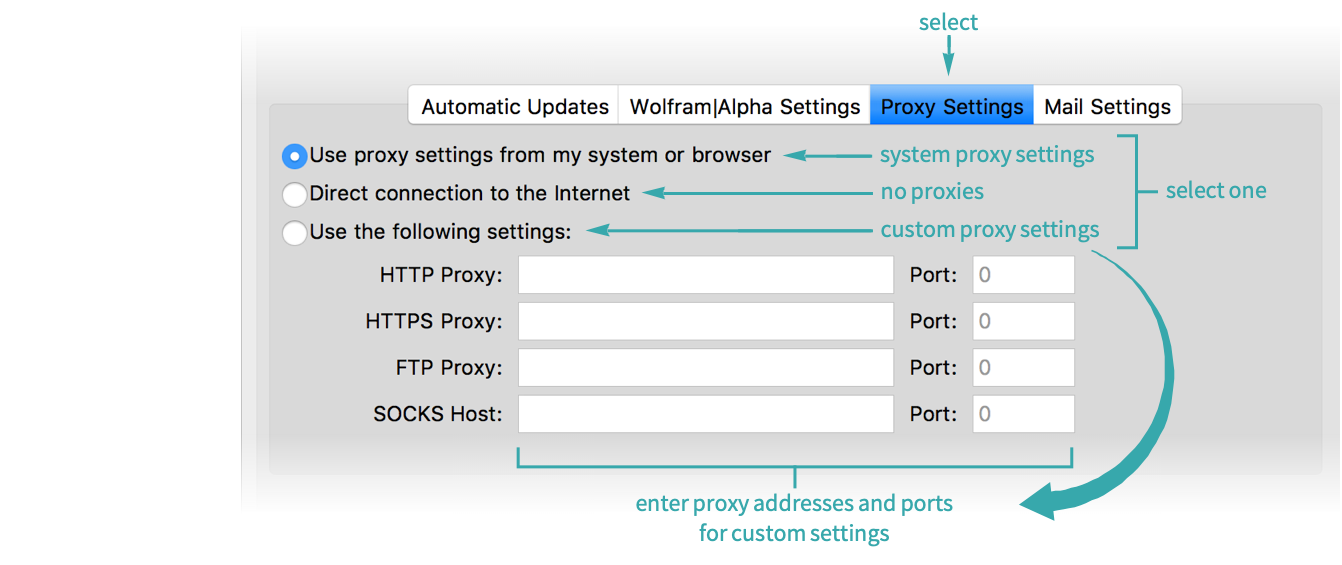
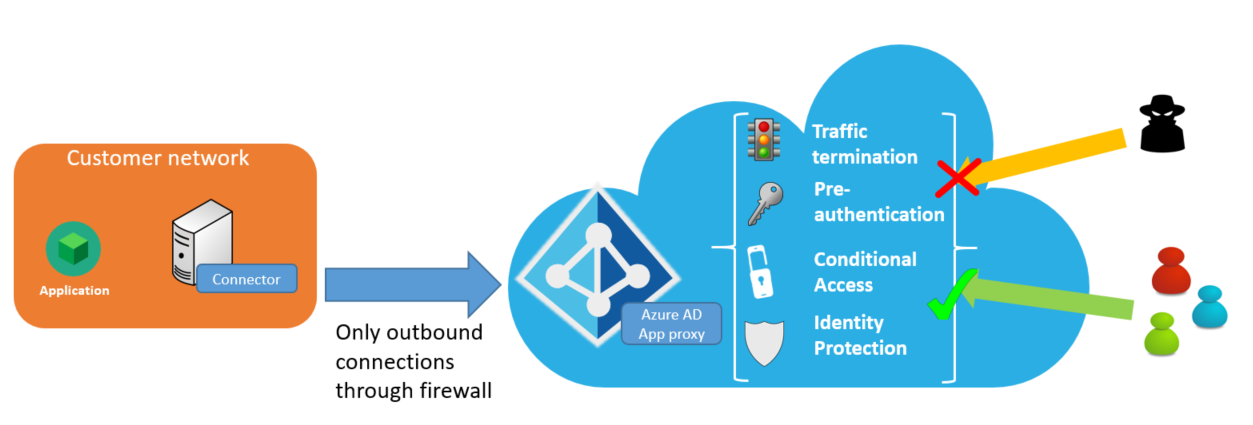
Using a Proxy - FlowJo Documentation | FlowJo Documentation - Documentation for FlowJo, SeqGeq, and FlowJo Portal