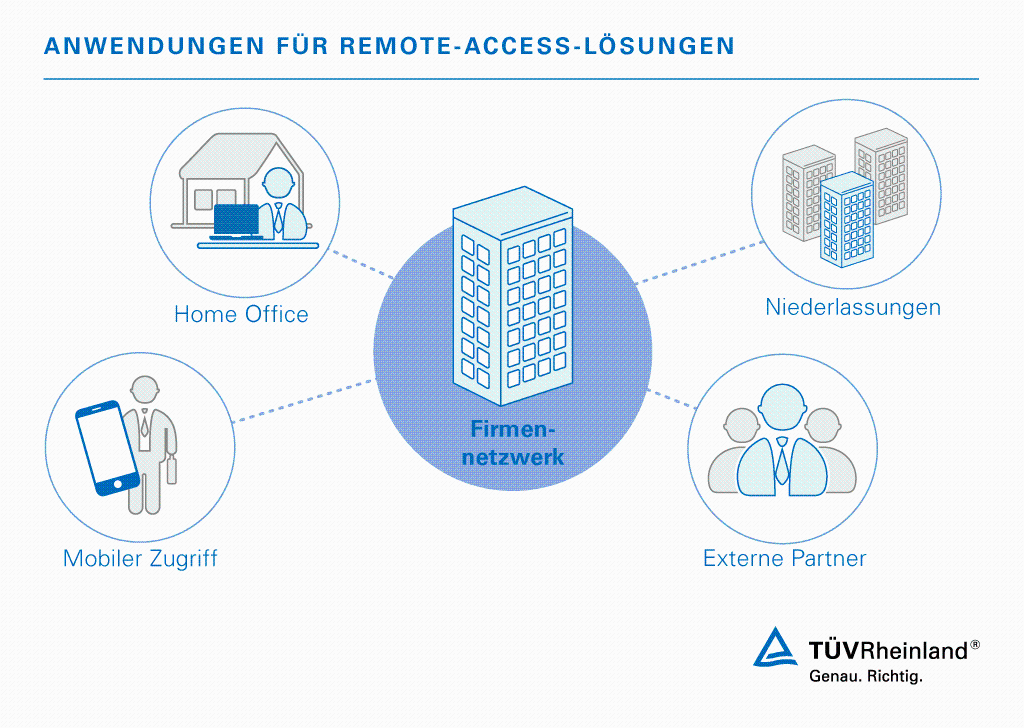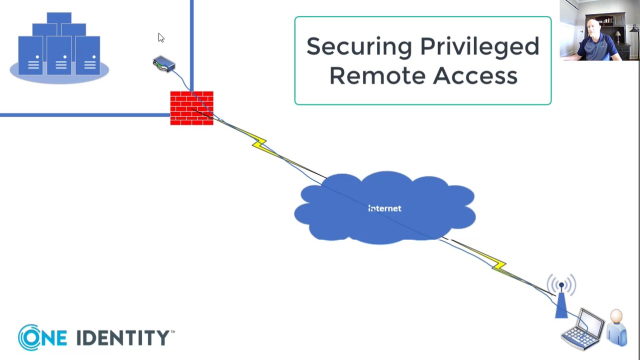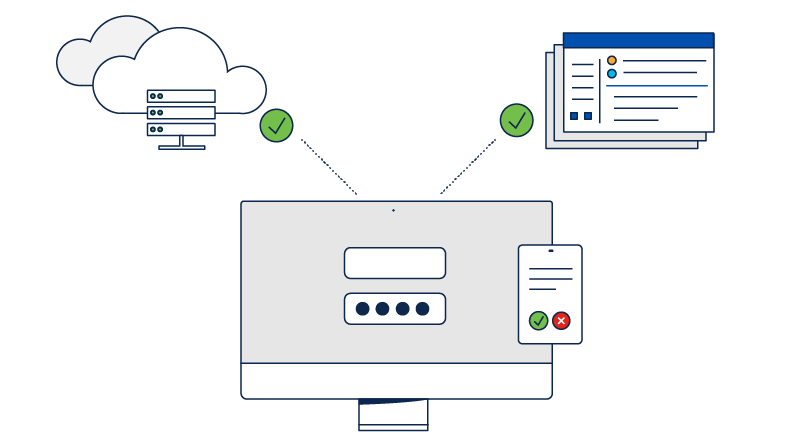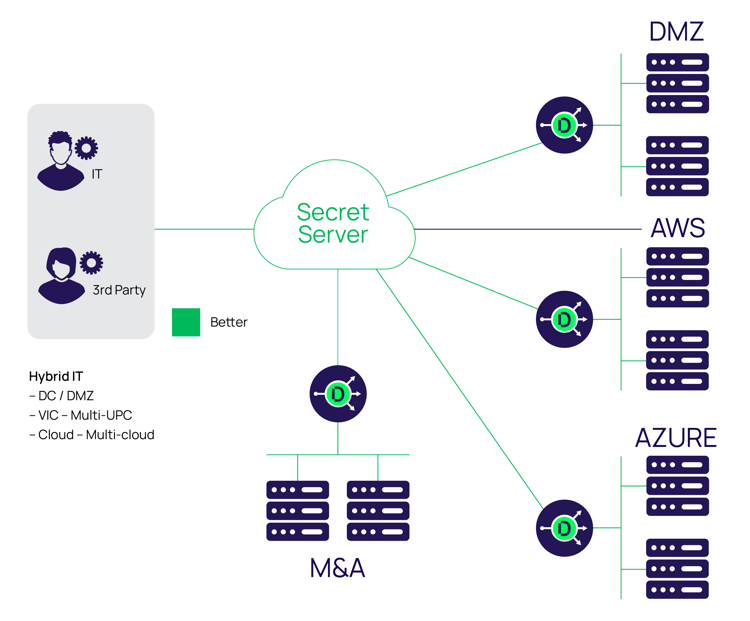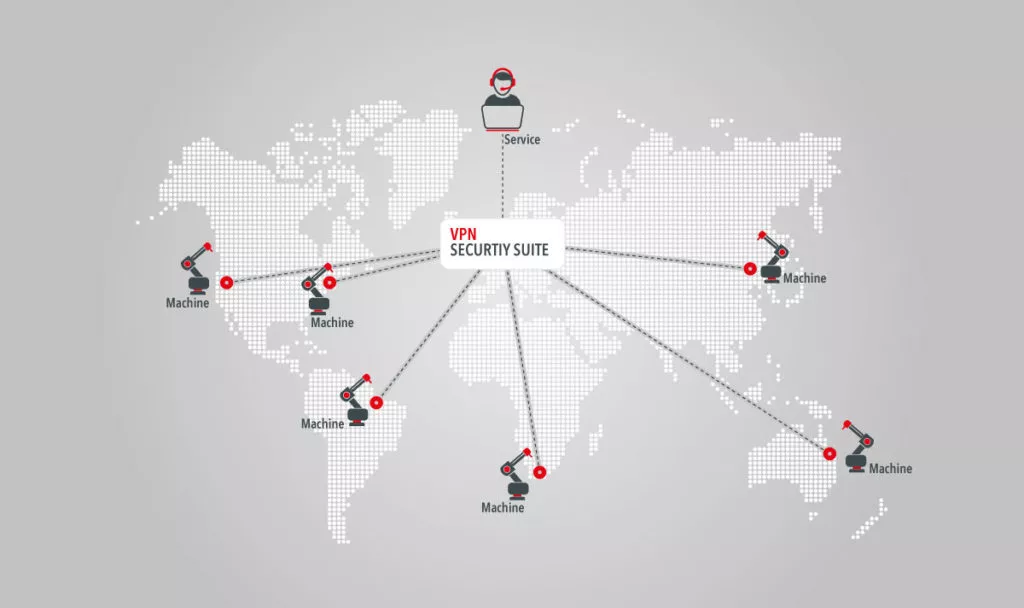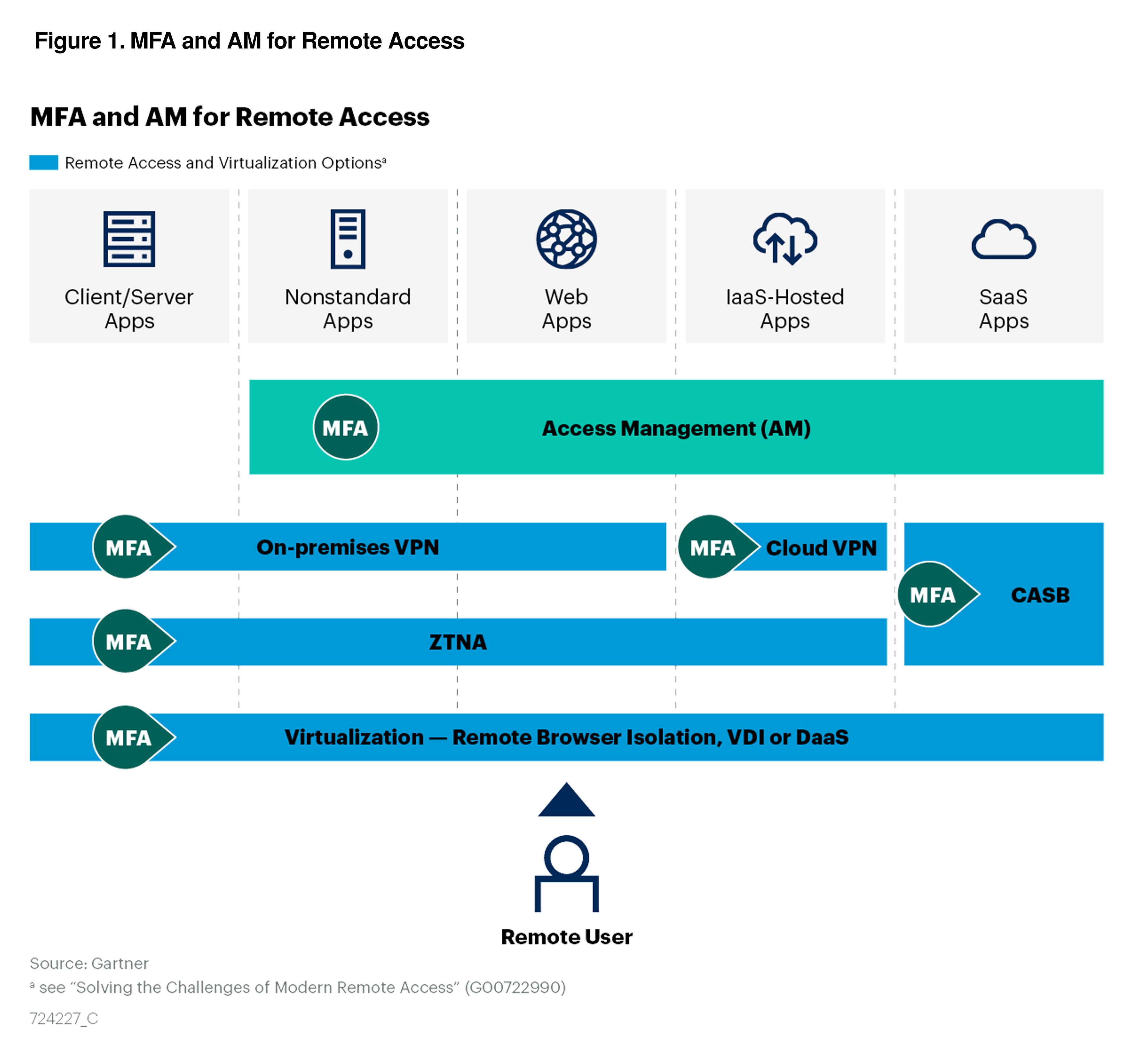
Höhere Sicherheit bei Remote-Zugriffen mit Multi-Faktor-Authentifizierung und Zugriffsverwaltung | Okta

Secure remote access: What it is, importance, benefits, and best practices | ManageEngine Access Manager Plus

Secure remote access: What it is, importance, benefits, and best practices | ManageEngine Access Manager Plus
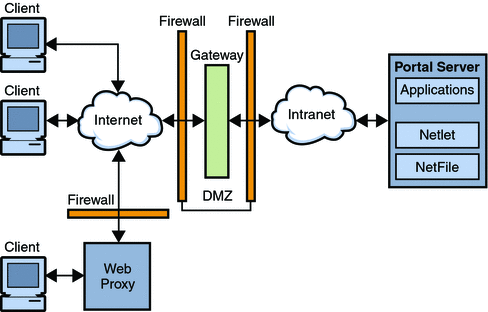
Introduction to Secure Remote Access (Sun Java System Portal Server Secure Remote Access 7.2 Administration Guide)

NSA, CISA Release Guidance on Selecting and Hardening Remote Access VPNs > National Security Agency/Central Security Service > Press Release View