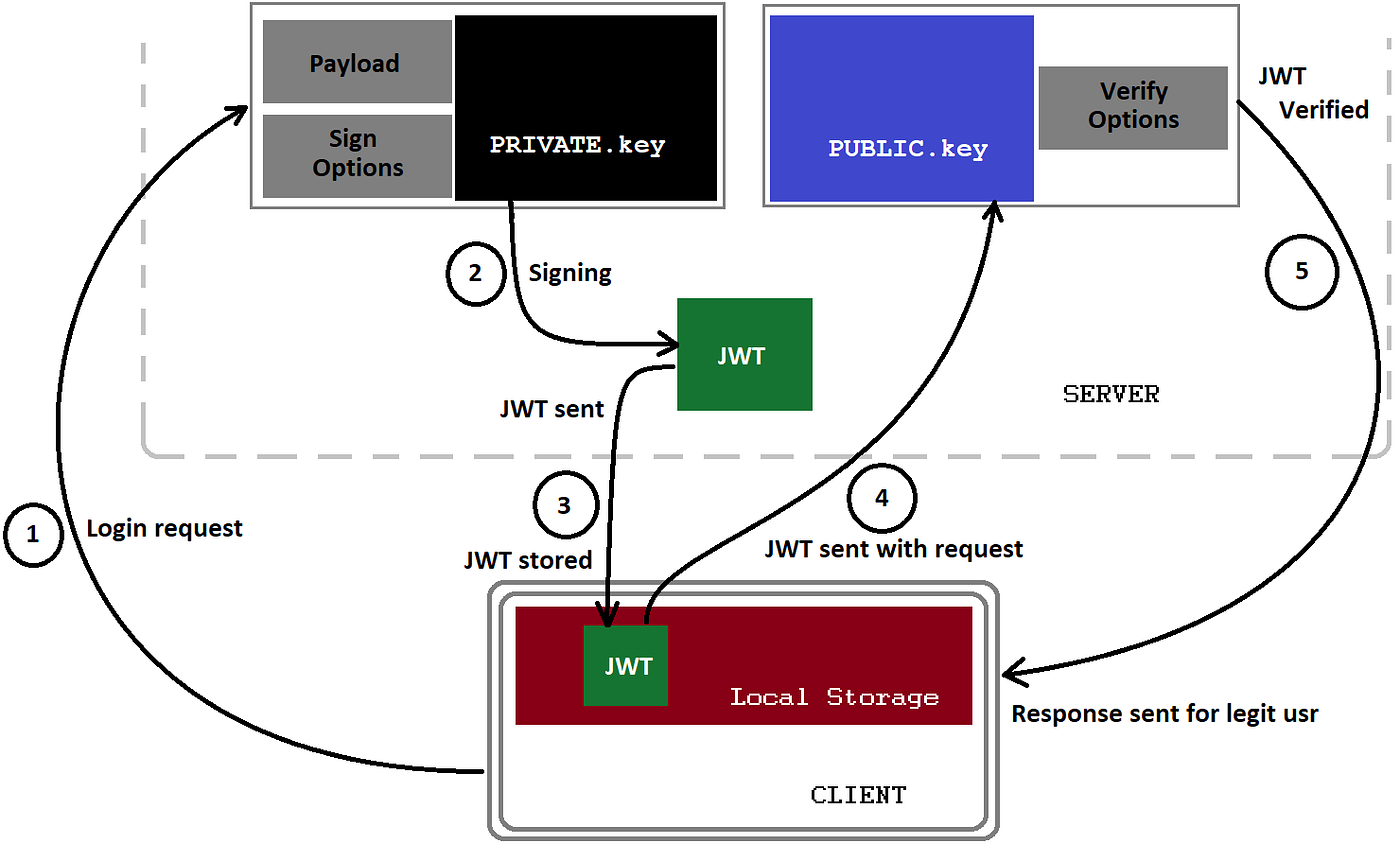
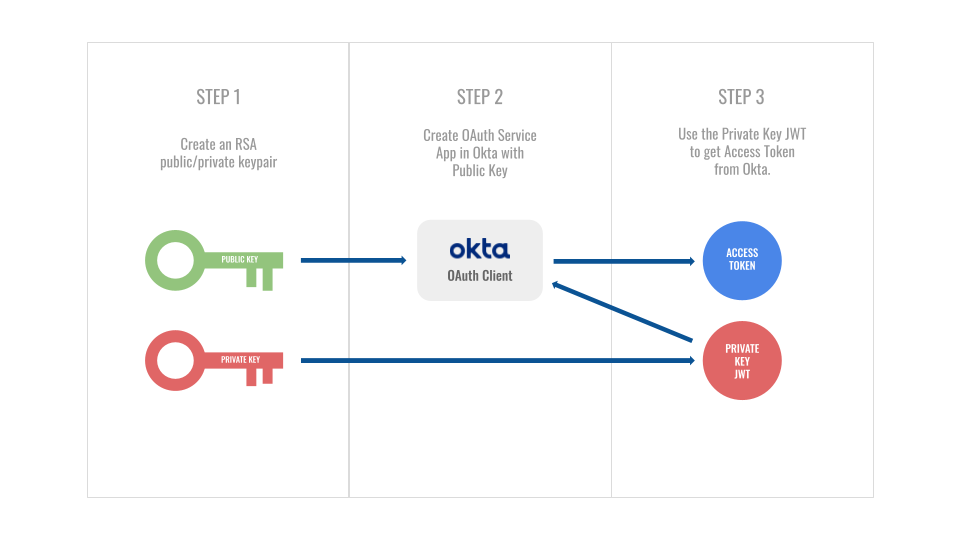
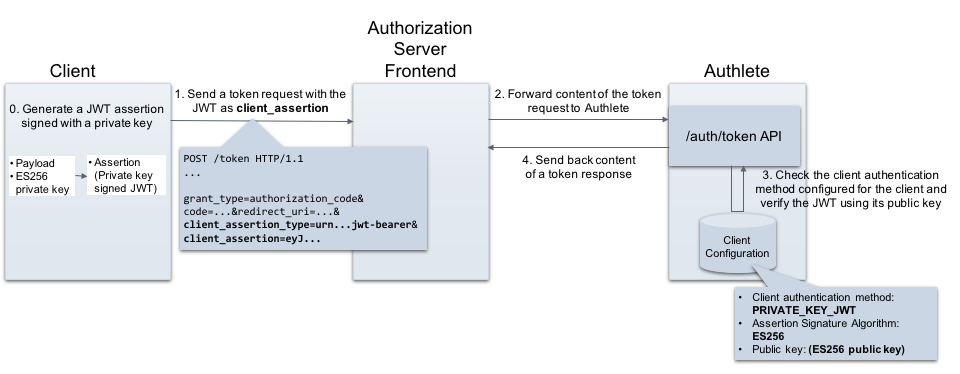
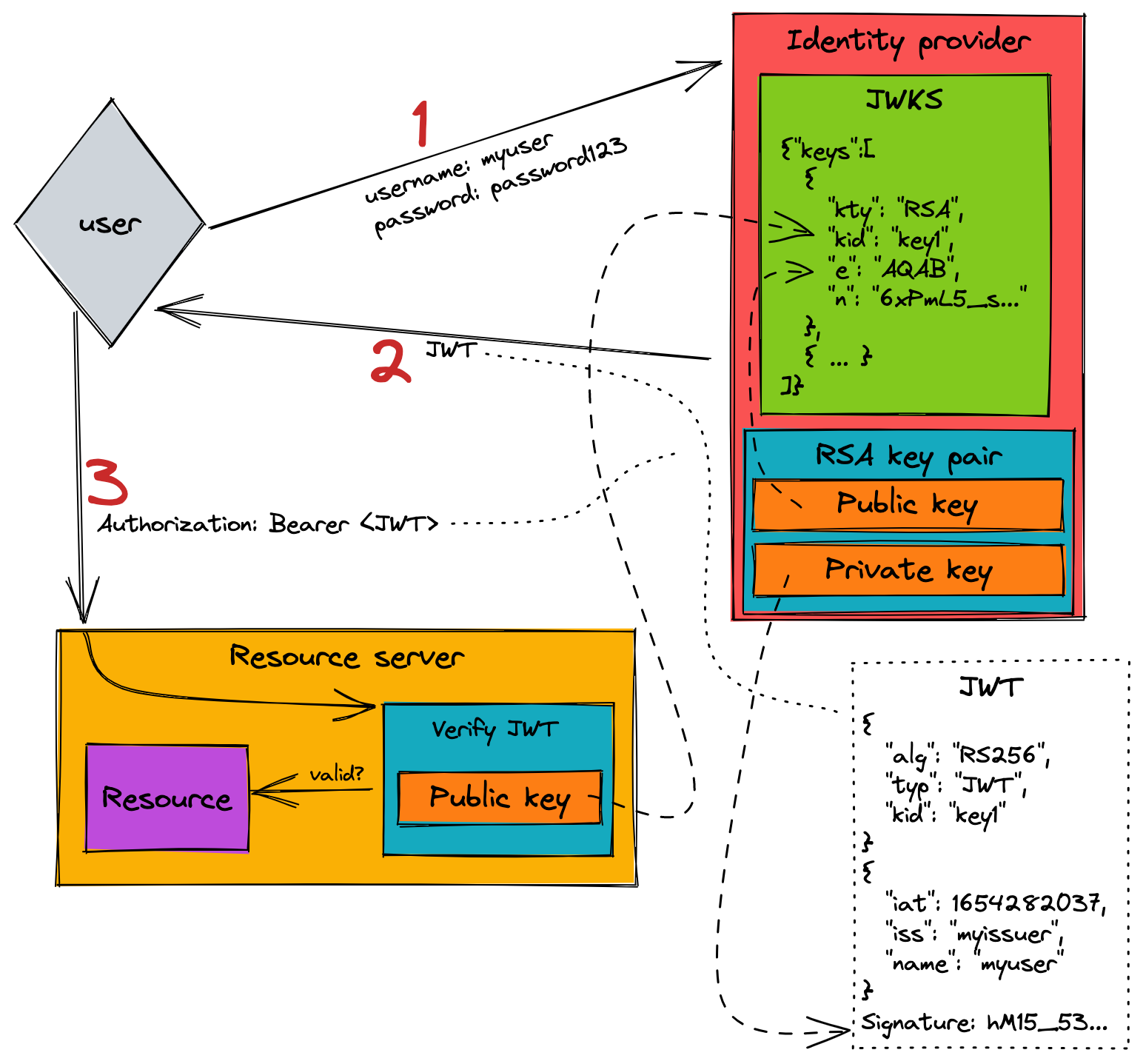
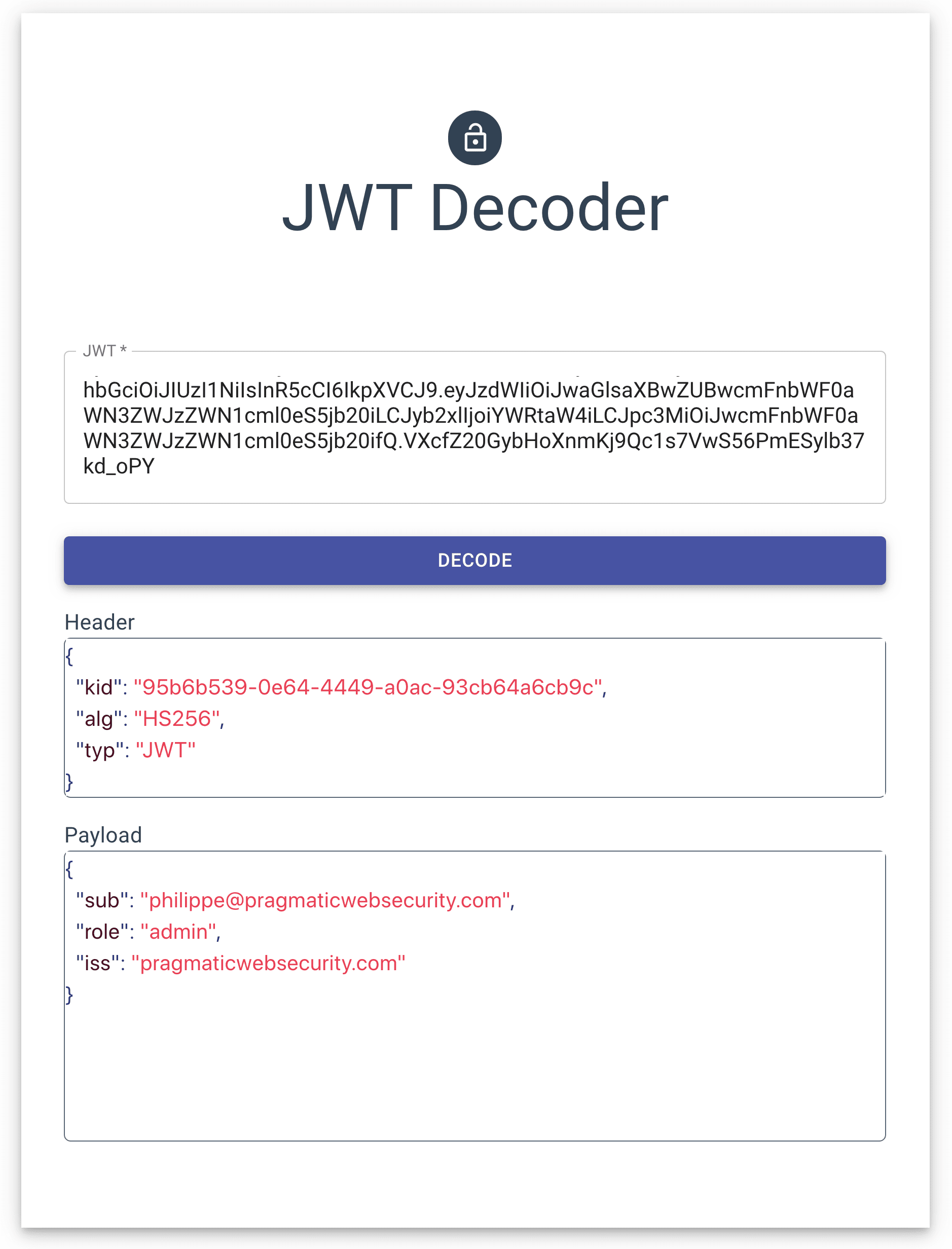
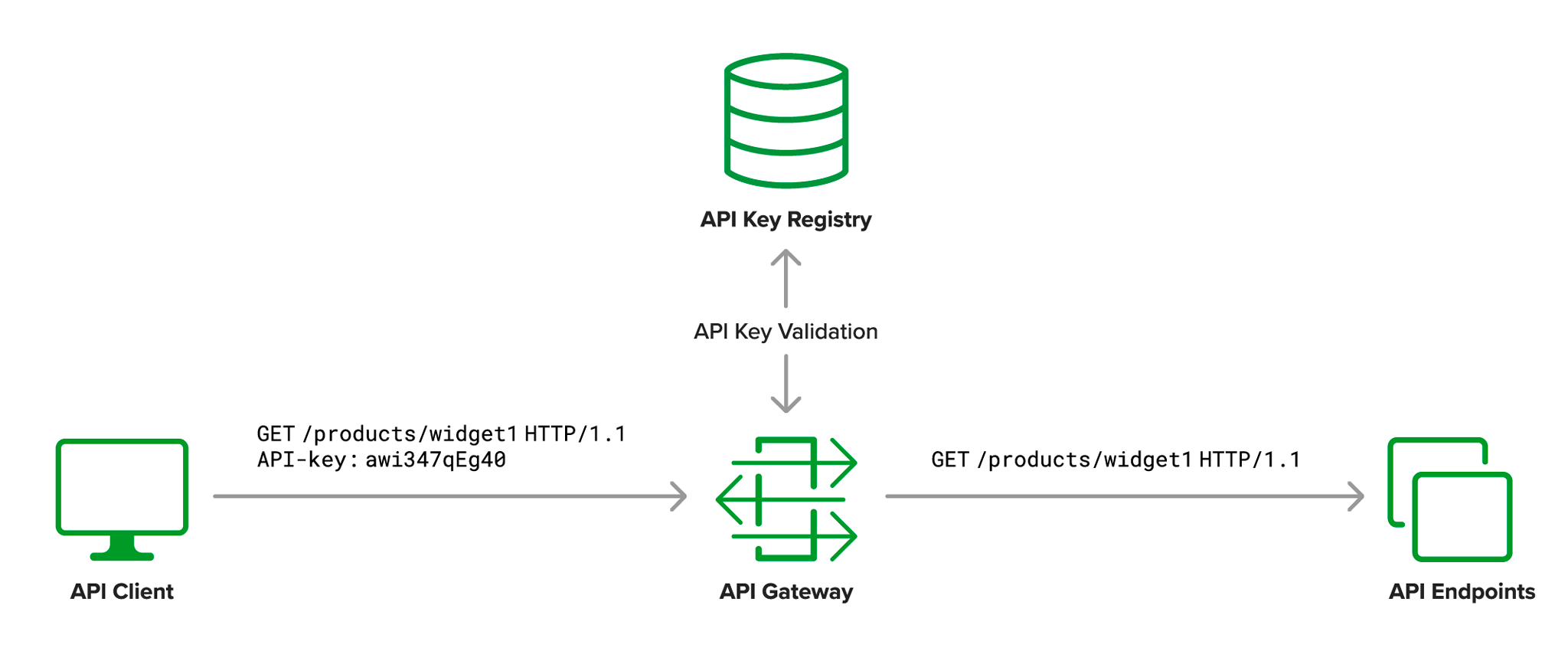
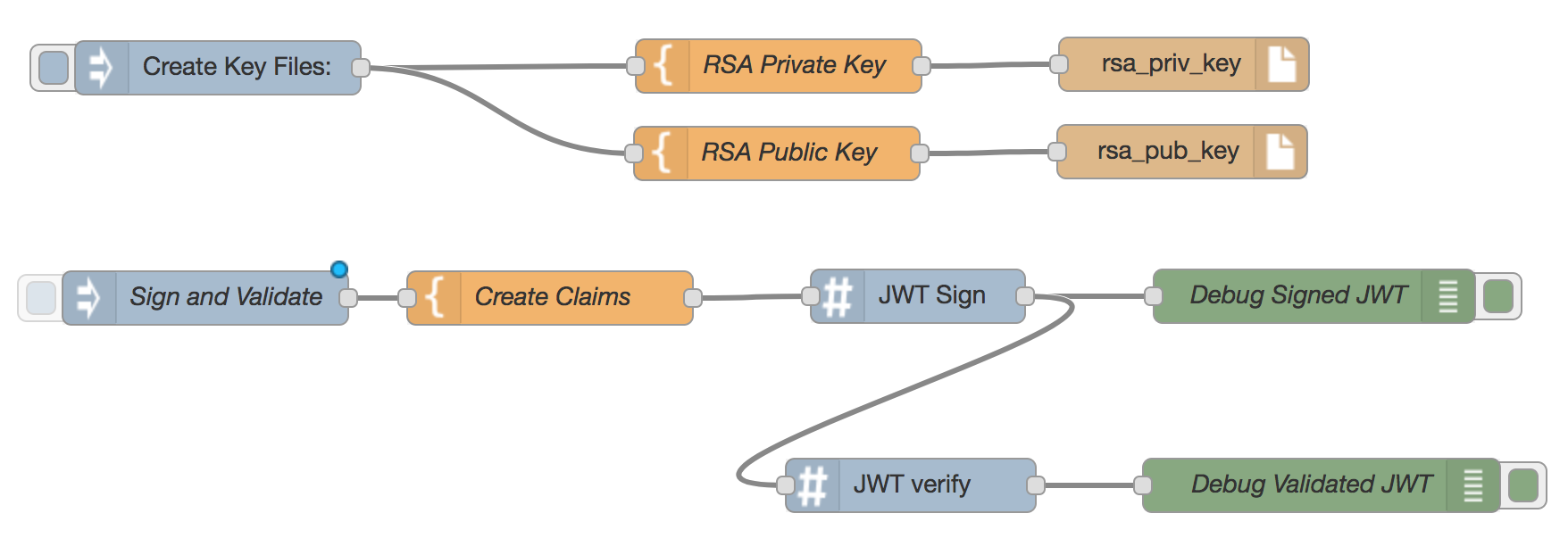
How to get public key to validate JWT received from "Bot Channels Registration" · Issue #89481 · MicrosoftDocs/azure-docs · GitHub
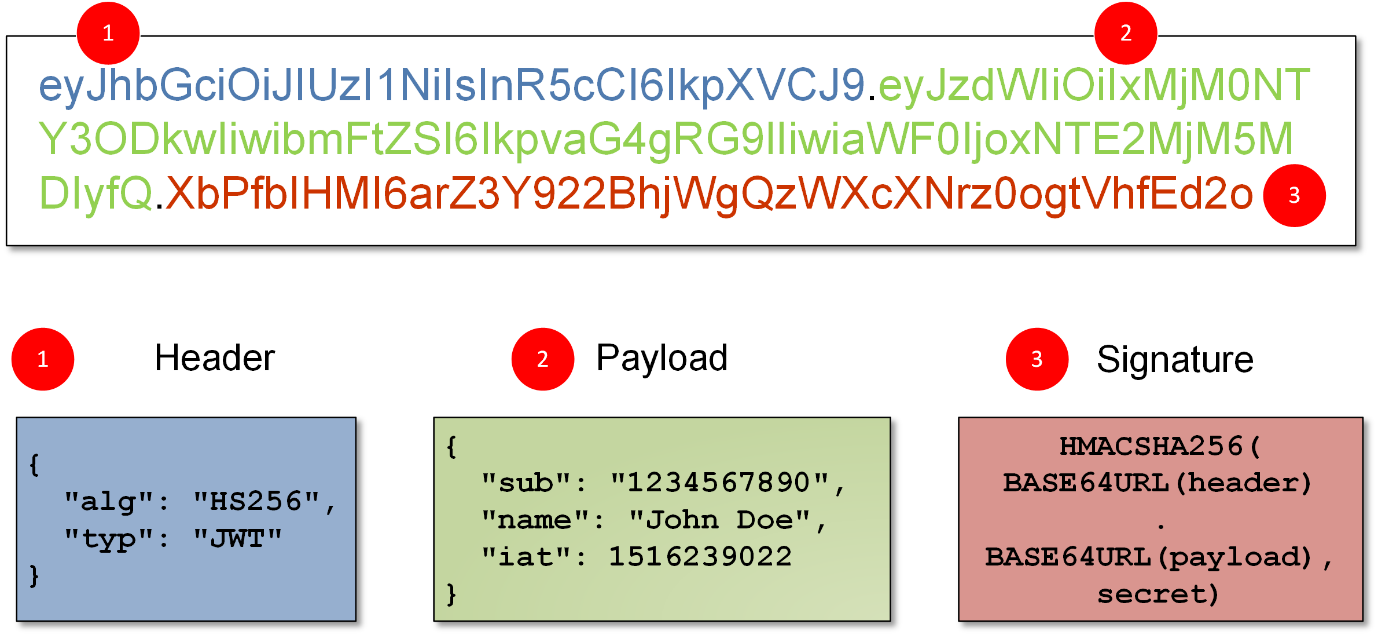
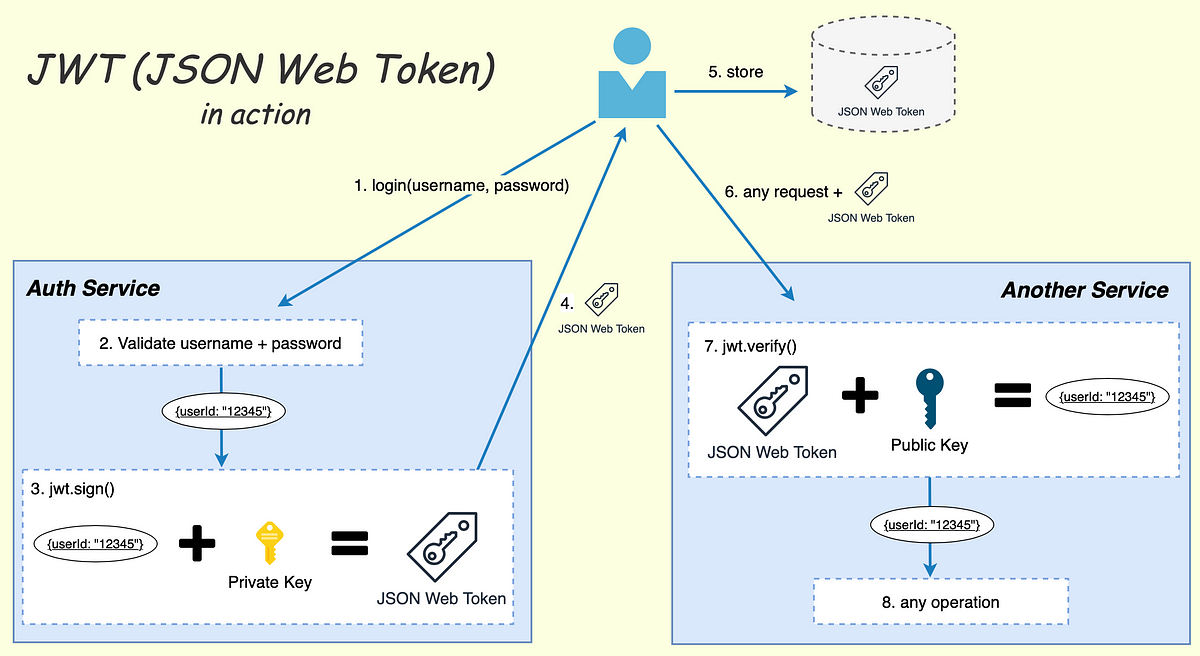
How To Validate a JWT Token. JWT stand for JSON Web Token. It is a… | by Muhammad Danyal | DataSeries | Medium

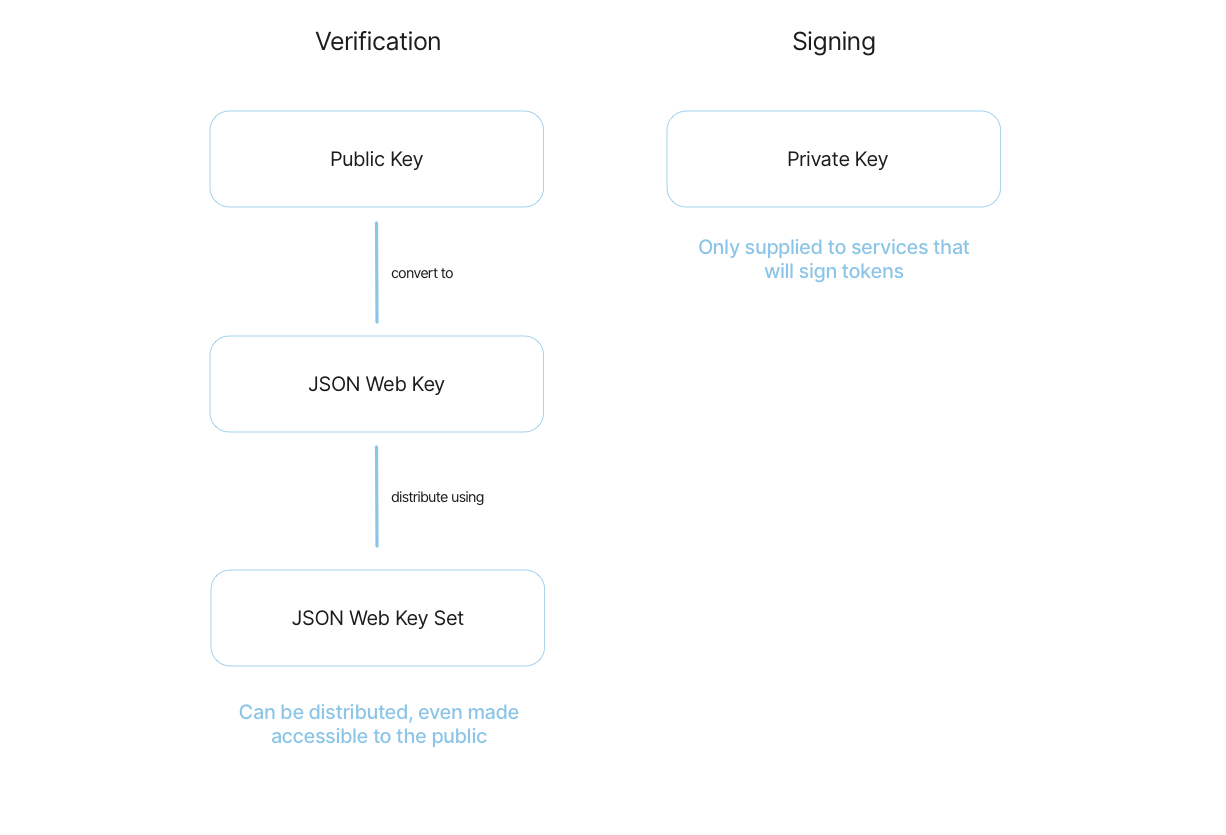
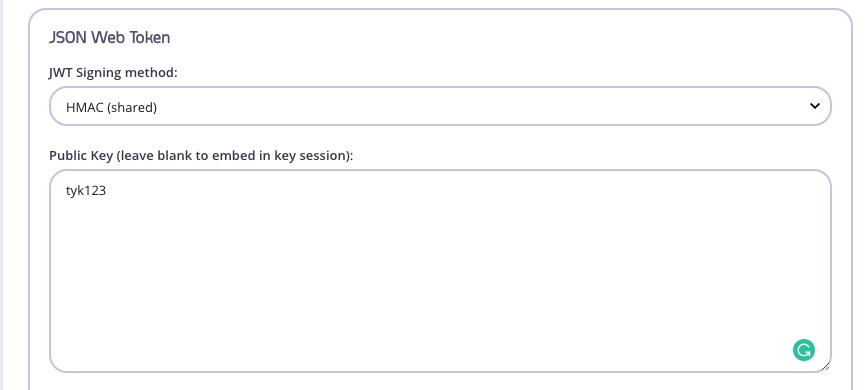
openid connect - What public key to use when verifying JWT.io signature OneLogin ID Token - Stack Overflow
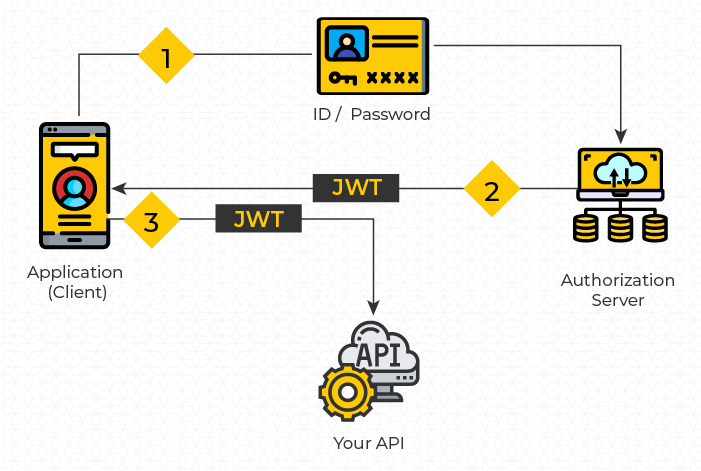
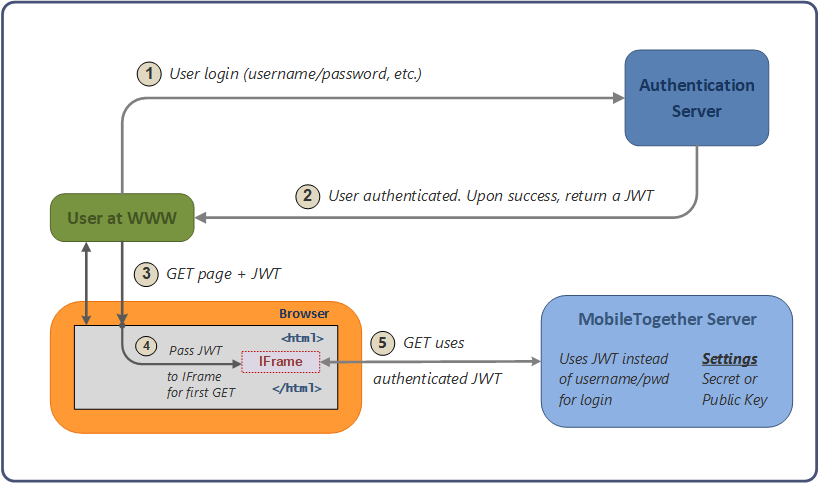
JSON Web Token (JWT): An Overview – Siddha Development Research and Consultancy (SDRC) – Enabling Social Change